Setting file upload controls
Most managed applications will support DLP actions on upload of files.
Apps include O365, GSuite, Box, Dropbox, Salesforce, Exchange, Egnyte, ServiceNow, Slack. For all apps, Allow and Block are supported actions, while Office 365 and Salesforce also support encrypt on upload.
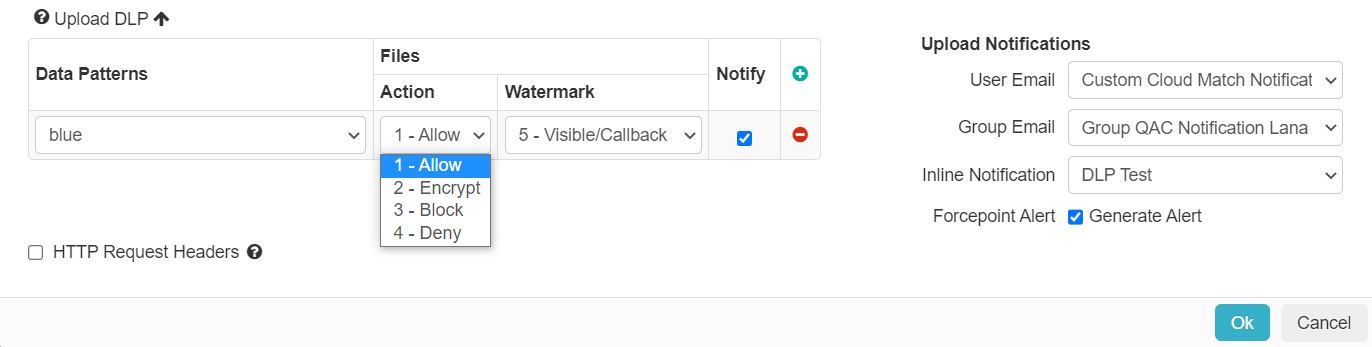
- Allow: Makes no changes to the file and allows the upload directly.
- Encrypt: With Microsoft 365, Google Workspace, or Salesforce, you can choose to encrypt data that contains sensitive information (for example, Credit Card digits or SSN’s) during the
upload process.Note: Forcepoint Data Security Cloud | SSE supports Encryption at rest for many apps via API. The encryption performed is the same as the encryption during upload for apps that support it. While the file will be encrypted at rest in the cloud application, users will not be able to open the file inside of the application (since the SaaS app will not be able to decrypt the file in order to display it). Users will need to download encrypted files through the Forcepoint Data Security Cloud | SSE proxy in order for the files to be decrypted.
- Block: Replaces all contents of a file with a block message.
Block message are configurable under .
- Deny: Will deny the upload action outright instead of attempting to convert the file to a block message. This is useful for situations where you are trying to control things such as malware.
Note: If you select Forcepoint DLP as the data pattern, then FSM Enforced
option gets populated in Action field as the action is provided from FSM. The FSM Enforced is the only option available for selection. Refer to
Configuring FSM controlled policies for CASB and SWG channels to enable the Forcepoint DLP data pattern.
Text Matching DLP
For Microsoft 365 and Salesforce, Forcepoint Data Security Cloud | SSE customers are able to apply DLP policy on Form Text (this includes Yammer and Sharepoint Lists in Microsoft 365 and Chatter in Salesforce). For example, you could apply policy to text entered into Yammer or posted to a Sharepoint list if it contained sensitive or personal information.
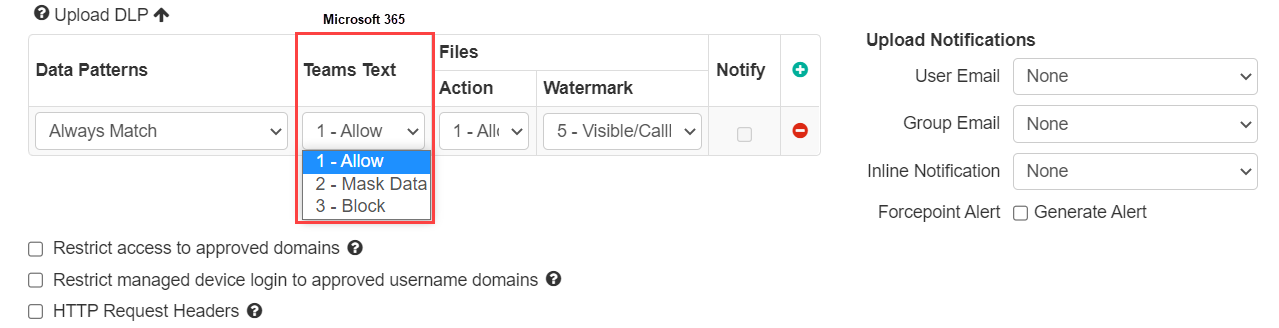
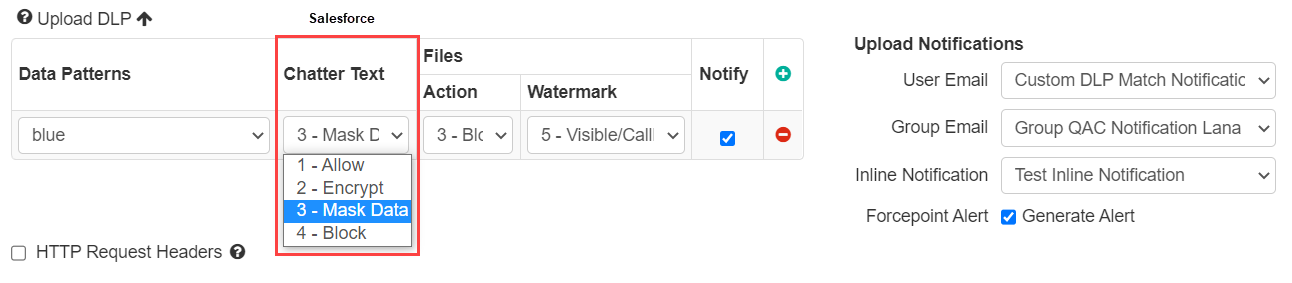
- Allow: Allows the text to be sent “as is” (default)
- Mask Data: Replaces the matched DLP text with "XXXXXX."
- Block: Replaces the DLP matched text as well as the surrounding text with a block message you have configured in .
Note: If you select Forcepoint DLP as the data pattern, then the text matching field is set to its default value as
this field is not supported and is grayed out. Refer to Configuring FSM controlled policies for CASB and SWG channels to enable the Forcepoint DLP data pattern.