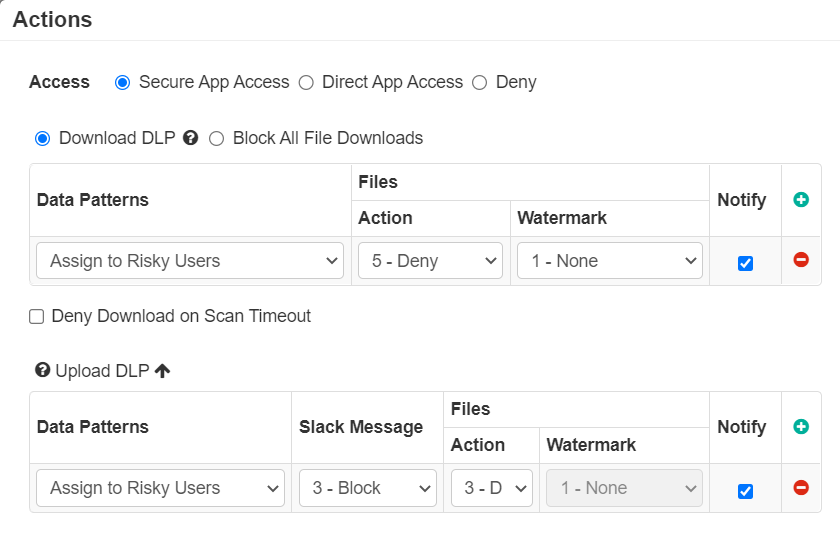
At times you might want to create a policy that, when violated, will assign users to a risky group to restrict further access and allow admins to review their activity before removing
them from the risk group. You can accomplish this using Advanced Patterns and the AssignToGroup construct.
Similarly, use the RemoveFromGroup construct in Advanced Patterns to remove users from the local user group Risky, if the above data pattern matches.
Steps
-
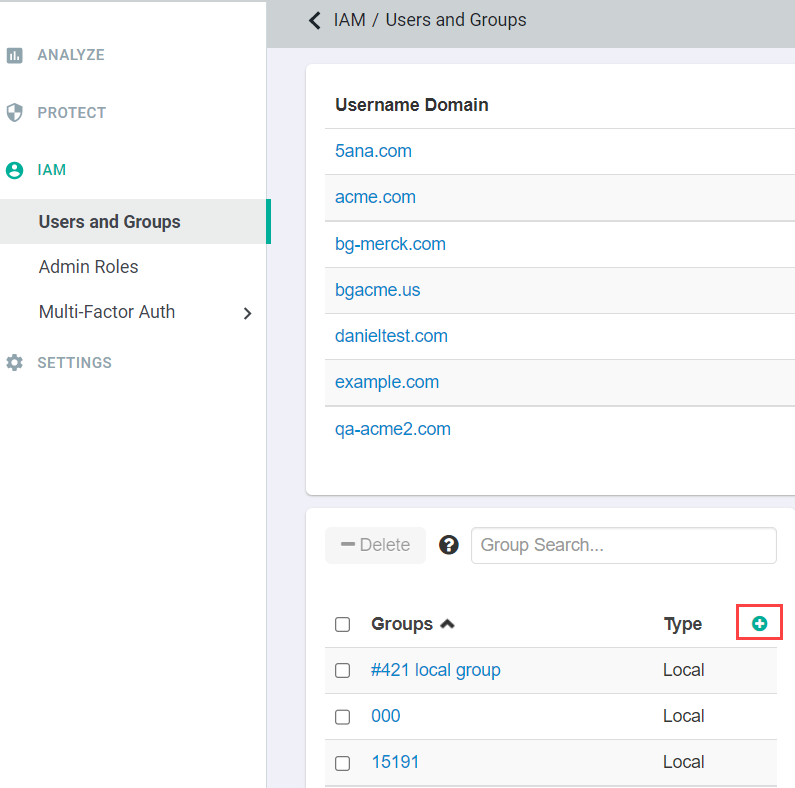
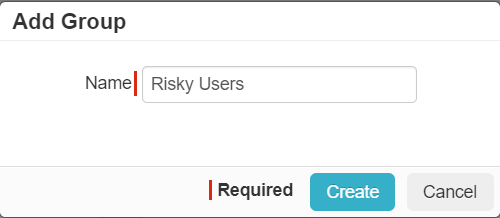
Create a user group that you want to control. On the page and then click the green plus icon to create a new group. Conversely, this group could also be a group that is synced from your IAM system (for example, Active
Directory, Okta, etc) that you have integrated with Forcepoint Data Security Cloud | SSE.
-
Provide a recognizable name to the group and Create.
You can then add a policy line to each of your application for this specific group with limited or no access (blocking all downloads or just denying access all together).
This policy line should be the first line of each application to ensure users in this group hit the heavily controlled policy instead of hitting others.
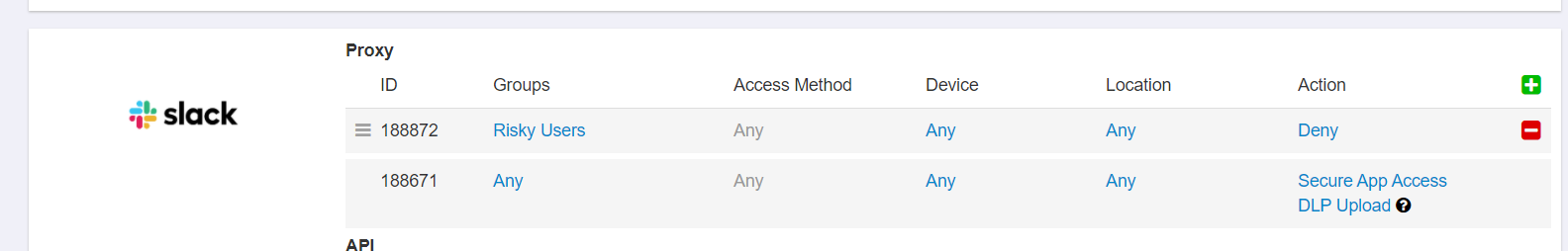
This policy is applied by creating an Advanced Pattern that triggers when it matches a specific other data pattern you are looking for.
-
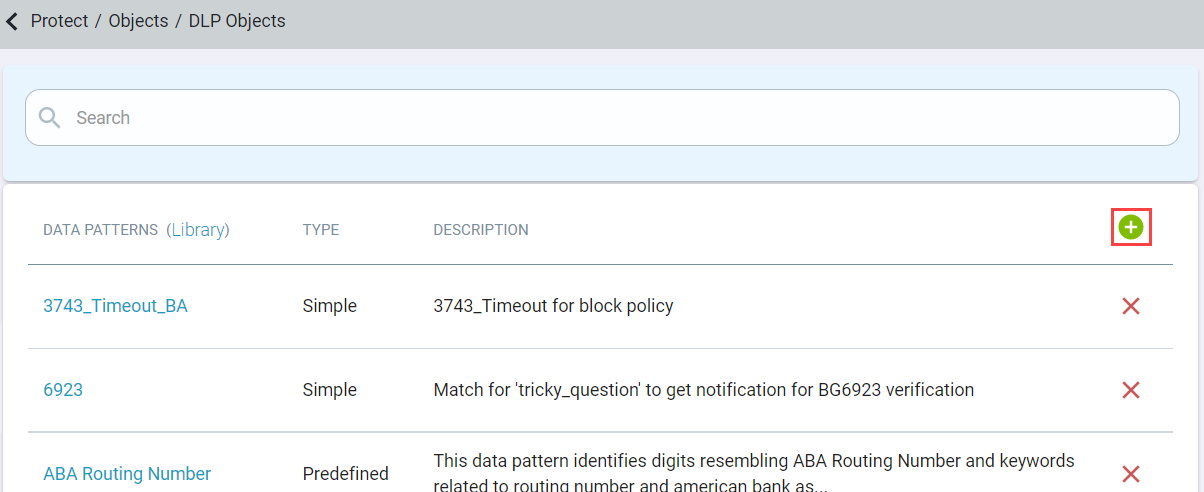
Navigate to the page.
-
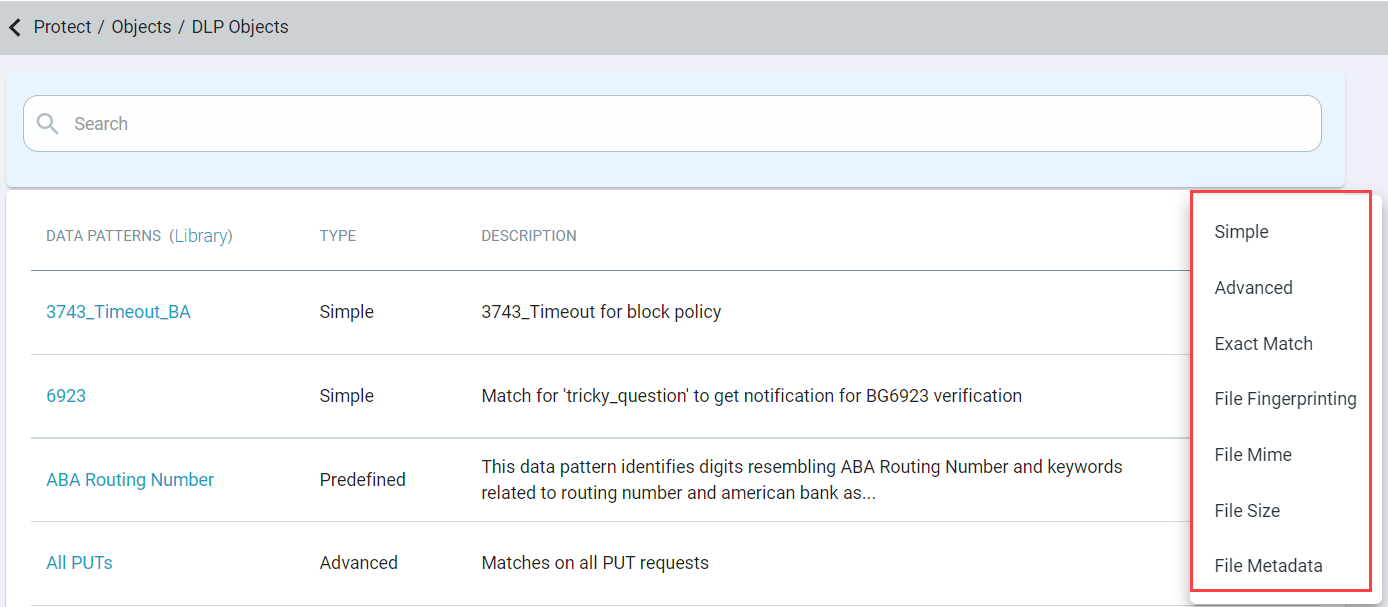
Click the green plus icon and select Advanced to create the data pattern.
-
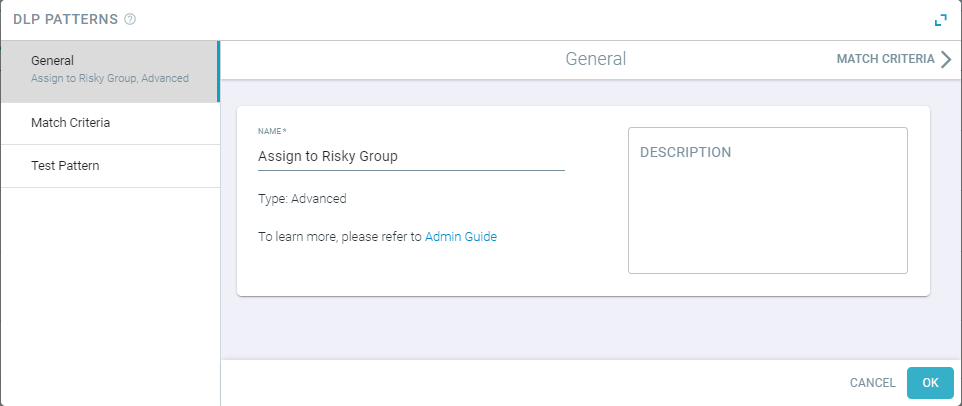
Enter a name that is recognizable and a description for what the pattern is doing.
-
Click on the Match Criteria tab and then enter advanced pattern.
The format you will follow is as follows:
<RegEx Pattern> ->(AssignToGroup "<Group Name>")
RegEx Pattern: This can be any RegEx Pattern(s) you wish to identify/trigger on for an inline policy. Can be referencing an existing simple datapattern or
can be an advanced pattern with boolean logic/etc.->(AssignToGroup "<Group Name>")): Sets the action to be taken when the pattern is identified. In this case, it will add the user who violated the
policy line to the specified group.If the group specified in the condition does not exist (), then an error similar to the Group Risky does not exist is displayed.
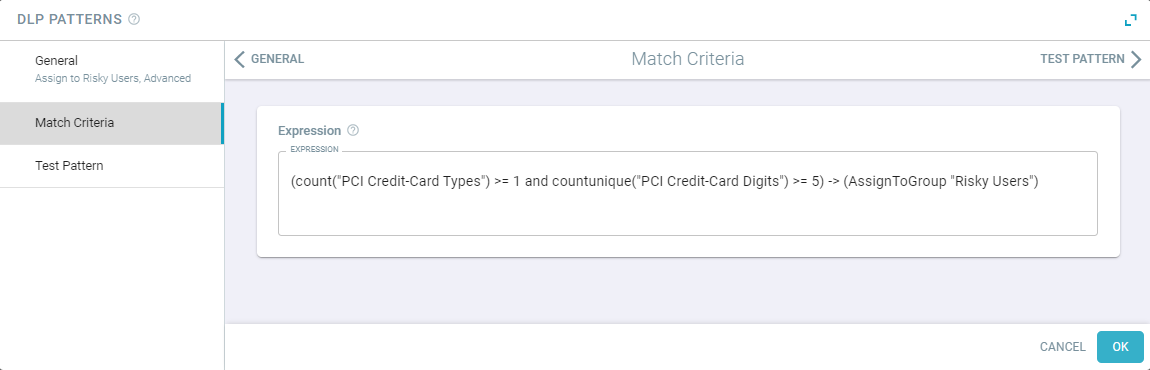
For example, the below screenshot is a pattern that will
trigger whenever a user triggers a policy with a file that contains multiple credit cards and will then assign that user to a user group called Risky Users.
-
This pattern can be added to inline proxy policies or to at rest API policies. You should still apply an action to prevent a file from being uploaded/downloaded/etc so the initial
action is still controlled.