Configuring policy based routing
Configure two policy based routing rules, that is one rule to route traffic through the primary tunnel and a second policy rule to route traffic to the secondary tunnel whenever the primary tunnel is down and route back through the primary tunnel once the primary tunnel is up.
Note: Ensure to place the policy based forwarding rule to Forcepoint ONE SSE after the existing rules to avoid breaking existing routing.
Steps
- Navigate to Policies > Policy Based Forwarding > Add.
-
Configure policy based routing to route traffic through the primary tunnel:
-
On the General tab, enter an appropriate rule Name.

-
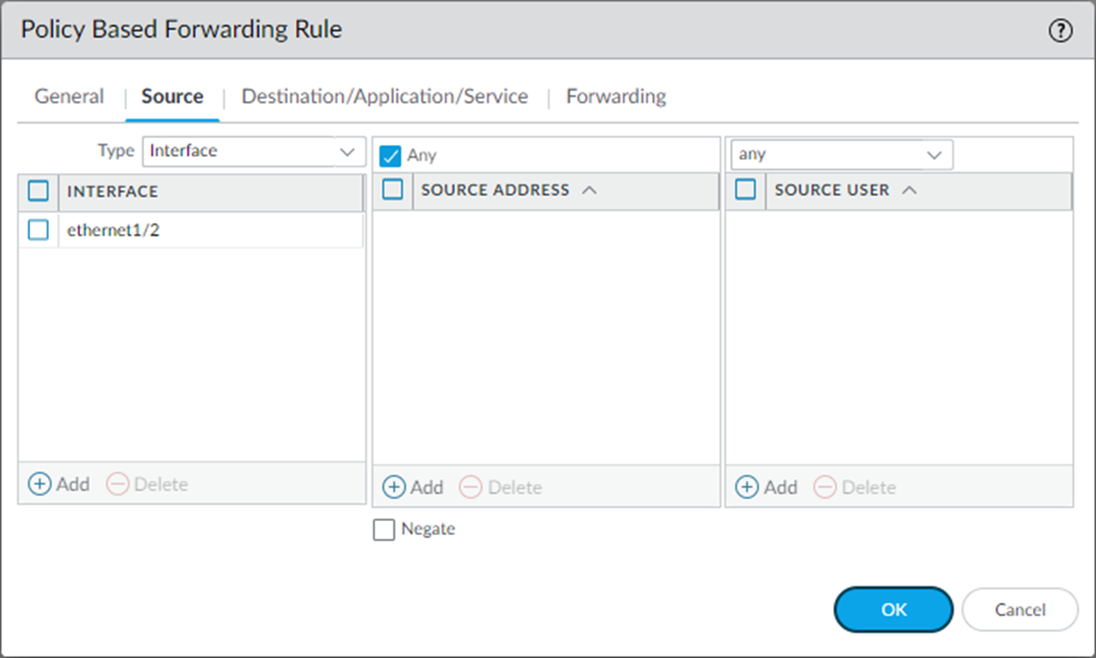
On the Source tab, select Interface from the Type drop-down and choose the interface (in trusted zone)
connected to the clients.
-
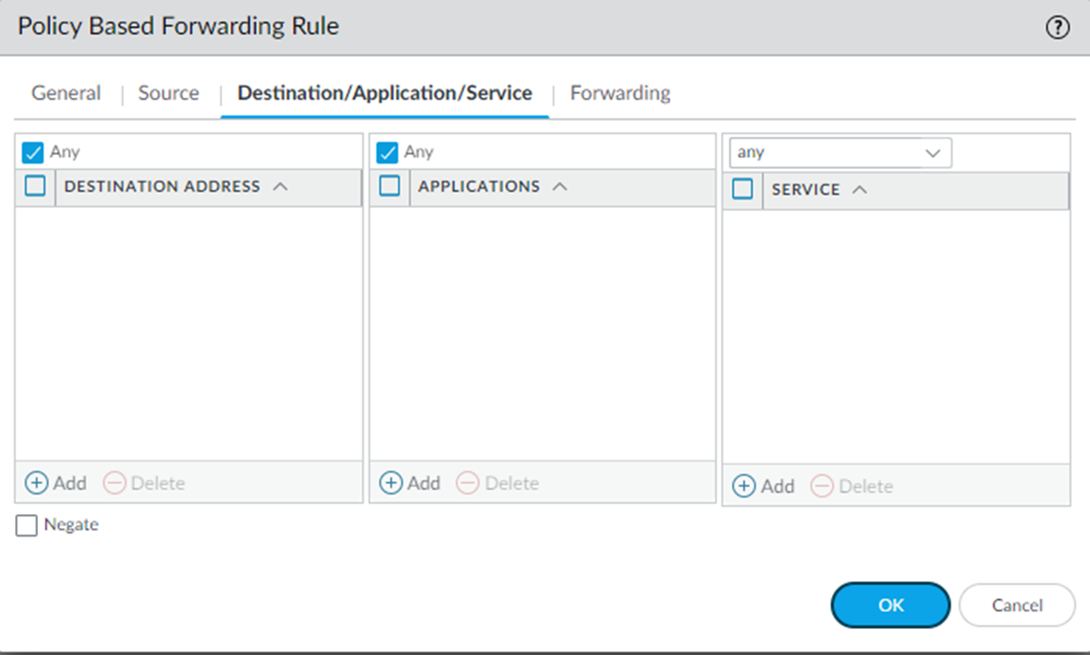
On the Destination/Application/Service tab, Select Any, Any, Any to send all
traffic down the tunnel.
Select Any, Any, service-HTTP & service-HTTPS to send just the web traffic down the tunnel.
-
On the Forwarding tab, enter the following details:
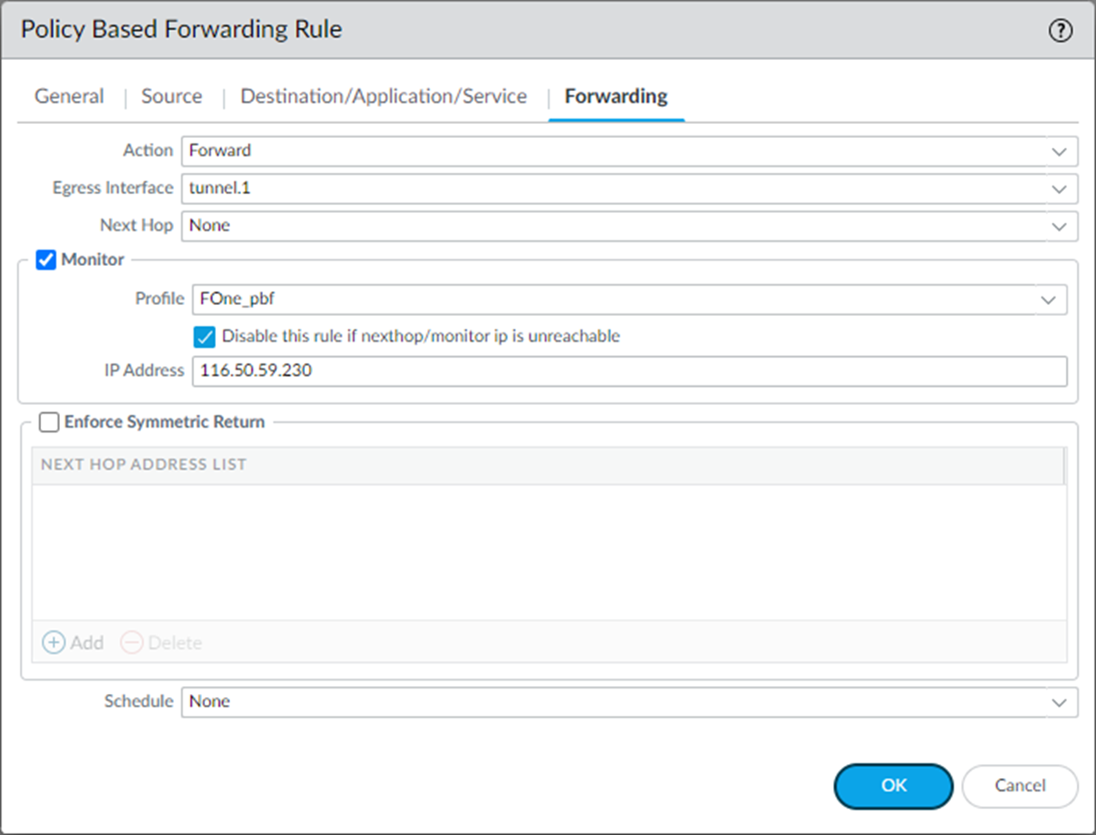
- Action: Select Forward to direct the traffic to the selected Egress Interface.
- Egress Interface: Select the primary tunnel interface that you have created from the drop-down. For example, tunnel.1
- Monitor: Select the Monitor checkbox to verify connectivity to a target IP address.
- Profile: Select the monitoring profile that you have created.
- Disable this rule if nexthop/monitor IP is unreachable: Select the checkbox to disable the rule if nexthop/monitor IP is unreachable.
- IP Address: Enter the monitoring IP address 116.50.59.230.
You can obtain the Monitoring IP from Forcepoint ONE SSE by navigating to the Analyze > Tunnels > Setup Info dialog of the primary or secondary IPsec tunnel.
- To create policy with the entered details, click OK.
-
On the General tab, enter an appropriate rule Name.
-
Create a second policy based forwarding rule for the secondary tunnel.
Note: Configure the General, Source and Destination/Application/Service tabs same as step 2.
- On the General tab, enter an appropriate rule Name.
- On the Source tab, select Interface from the Type drop-down and choose the interface (in trusted zone) connected to the clients.
-
On the Destination/Application/Service tab, Select Any, Any, Any to send all
traffic down the tunnel.
Select Any, Any, service-HTTP & service-HTTPS to send just the web traffic down the tunnel.
-
On the Forwarding tab, enter the following details:
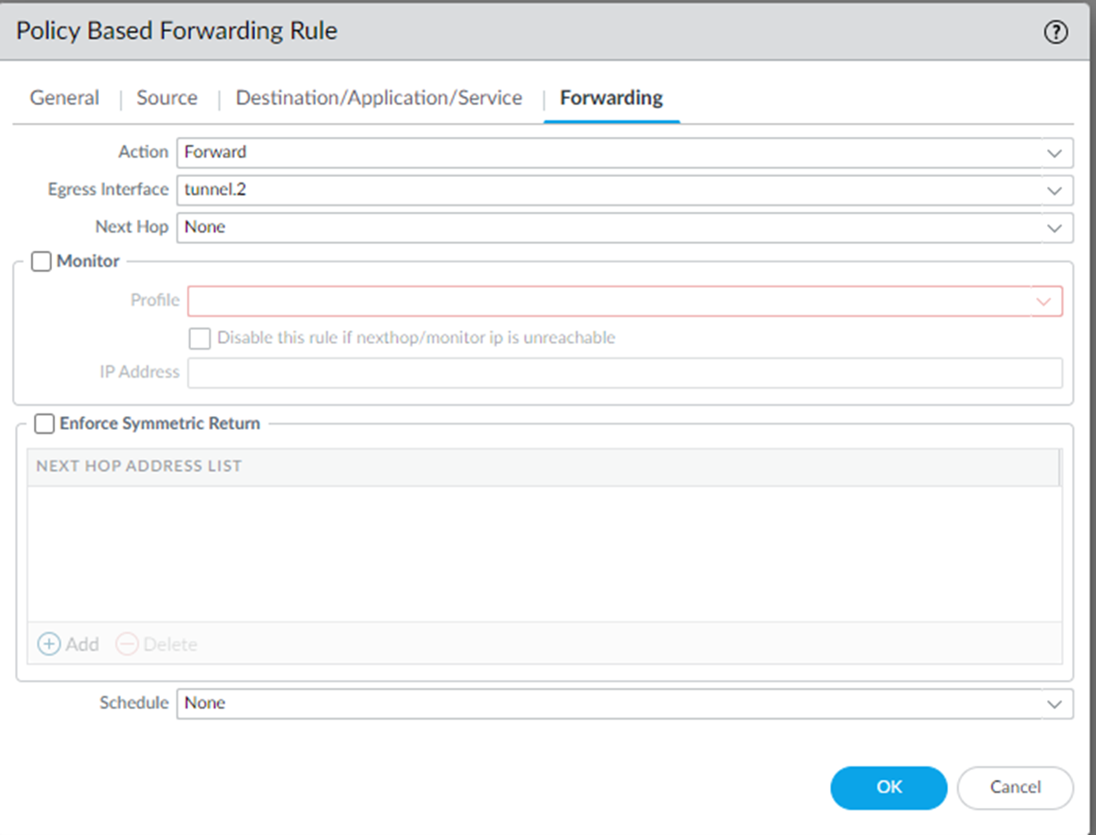
- Action: Select Forward to direct the traffic to the selected Egress Interface.
- Egress Interface: Select the secondary tunnel interface that you have created from the drop-down. For example, tunnel.2
- Disable this rule if nexthop/monitor IP is unreachable: Do not select the checkbox so that if the primary tunnel comes back up, Palo Alto will automatically route the traffic back to the primary tunnel.
- To create policy with the entered details, click OK.
-
Once the policy based forwarding rules are created, they should look like following:
