Recommended Default M365 Policy
A good general policy when deploying M365 for the first time would be to setup two policies: One allowing Direct App Access through Client Apps for Any Group, Device, or Location. The second policy would be setup to restrict ActiveSync and Web access through Secure App Access (with applied DLP).
Your policy should look something like this:
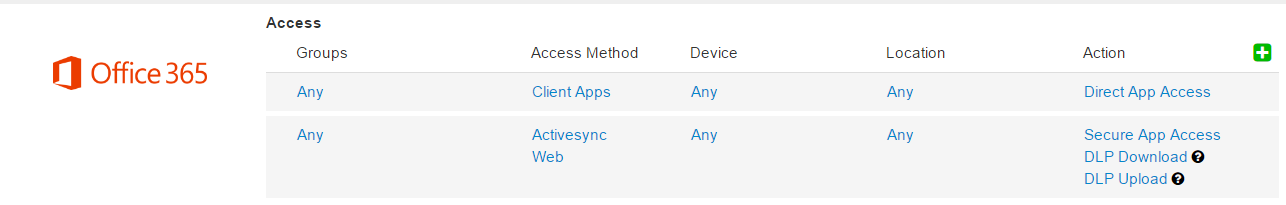
This policy is recommended to allow for an easy setup while still securing your data and providing minimal disruption to your employees. The first rule allows your employees to continue using their locally installed applications seamlessly as it allows direct app access (i.e. non-proxied). Applications such as Outlook or the OneDrive sync client will continue working without any issues. The second rule forces all web and ActiveSync traffic through the Forcepoint Data Security Cloud | SSE proxy allowing your data to be secured on any device and from anywhere. Once the deployment is complete, you can use the information garnered from the event log reports to begin to adjust and enforce stricter policy as needed. For more information on logs and the different dashboards view the guide page.
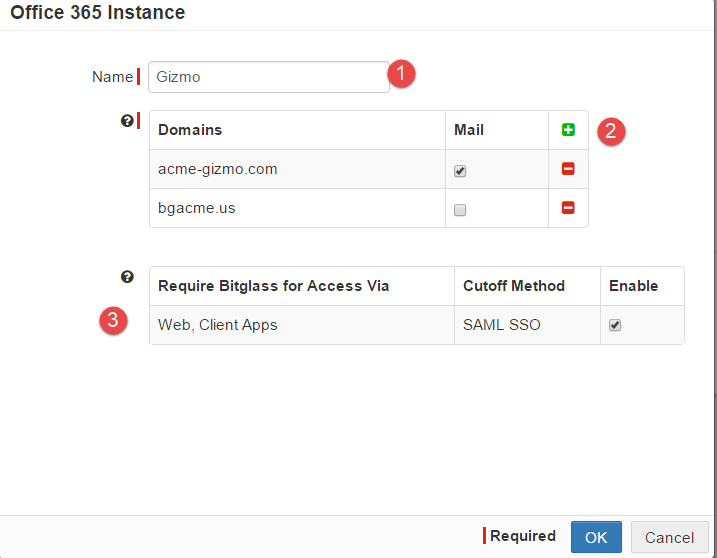
To get here, navigate to the page and click the Green Plus icon to add a new application. Select Microsoft 365 from the options presented.

- Give a name to the App Instance.
- Click the green plus to add your domain or domains if you have more than one.
- Check both of the boxes to enable cutoff to force traffic to be directed through Forcepoint Data Security Cloud | SSE.
- Remove Client Apps from the Access Method. Click into Access Methods (by selecting all the words under that column highlighted in blue).
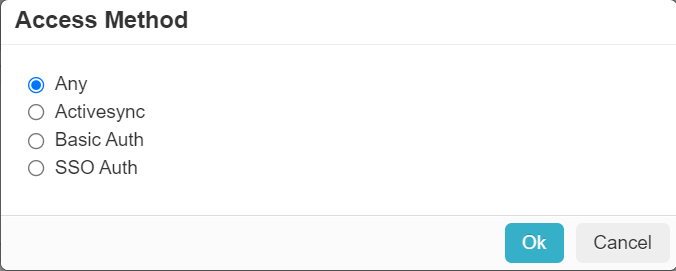
- On the Access Method dialog, uncheck SSO Auth and then select Ok.
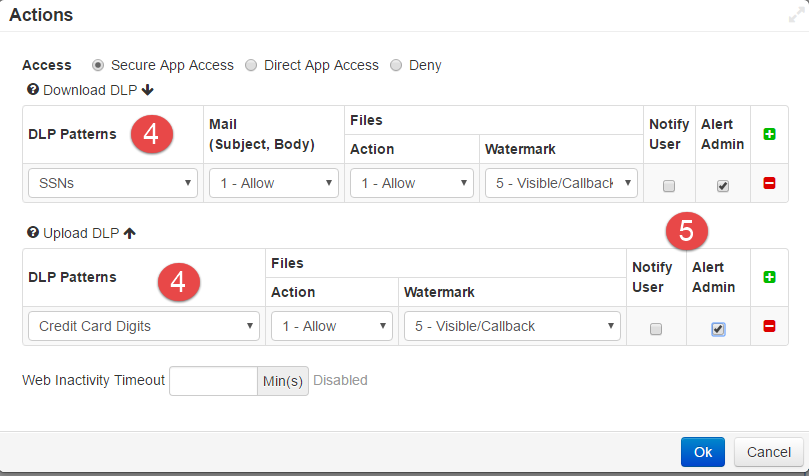
- Adjust the DLP and set a server timeout. Click into the Action column to bring up the Action dialog.
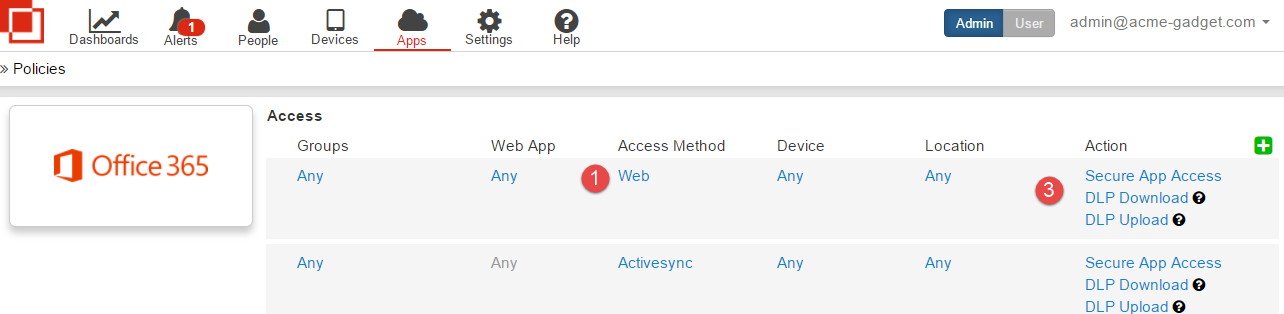
- On the Action Dialog setup your DLP patterns. Again it is recommended to leave most things to allow for the initial setup then enforce more strict policies after users have been migrated. For more information on DLP and how to create your own patterns view the
- Select if you wish to have the user or admin alerted if a DLP pattern were to match. This is recommended for the admin in order to track events that will allow you to refine your
policy at a later date.
- Click into the Access Method on the new policy
- In the Access Method dialog, uncheck SSO Auth and ActiveSync.
- Click into the Action column on the new policy.
- On the Action dialog, select Direct App Access.
This will create a policy that will allow all devices to access Office 365 through an installed client app (for example Outlook or OneDrive sync client).