Applying manual cloud action in API logs
In addition to triggered cloud policy actions, Forcepoint Data Security Cloud | SSE provides the ability for admins to apply manual cloud actions to files through the API Logs.
Admins can directly Quarantine files that did not trigger the cloud policy or Create Copy of file(s) for later inspection. Admins can also Add to Whitelist or Remove from Whitelist.
Note: Manual actions are supported by Google, Office 365, Box and Dropbox.
- Navigate to view.
- On the Event Logs card, select any number of files that you wish to apply for an action too.

- In the top right corner of the Event Logs card, you will see a drop-down box titled -Manual Cloud Actions-. Selecting the drop-down will bring up
the following options.

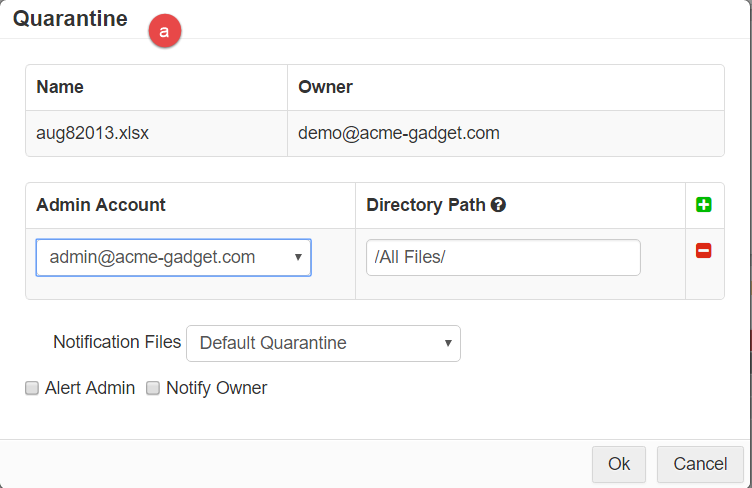
- Quarantine: Will move your file into an admin designed Quarantine account and Directory for additional inspection. A Notification File is
put in its place with the name of the original file +_quarantined.
- Add To Whitelist: Will mark the file to be moved to the Whitelist. The file, if quarantined, will then be moved out of quarantine otherwise the file will be marked
with Action = Whitelisted. Files that are whitelisted will be bypassed by cloud policies that would otherwise place it in quarantine.

- Remove from Whitelist: Will remove the files from the Whitelist.

- Create Copy: Will create a copy of the file and place the copy in an admin designated location for later viewing and inspection.

- Encrypt: Will encrypt the file selected if the application supports encryption of data at rest.

- Quarantine: Will move your file into an admin designed Quarantine account and Directory for additional inspection. A Notification File is
put in its place with the name of the original file +_quarantined.