Configure the Forcepoint Okta integration app for SCIM and SAML
Configure the Forcepoint Private Access Okta app to provide user and group provisioning, and single sign-on authentication for your Private Access end users.
Before you begin
Ensure you have administrator access to your organization's Okta account.
Steps
- Sign in to your Okta account with administrator privileges.
- On the Applications tab, click Add Application. Search for Forcepoint Private Access.
- Select the application and click Add.
- On the General Settings page, edit the App name (if required).
-
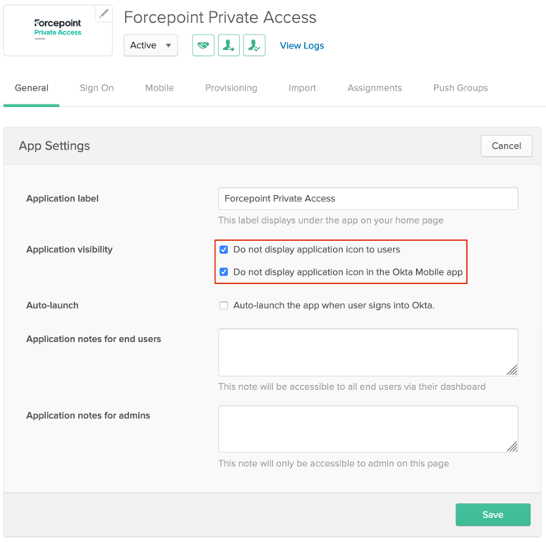
Hide the application from your Okta dashboard using the settings under Application visibility:
- Do not display application icon to users
- Do not display application icon in the Okta Mobile App
- Click Done.
-
In the Private Access management portal, go to Administration > SCIM Settings. Copy and make a note of the
Base URL for the Forcepoint SCIM service.

- Click Generate New Token. Copy and make a note of the token.
- Return to the Okta portal. Go to the Provisioning tab for the application, and open the Integration settings page.
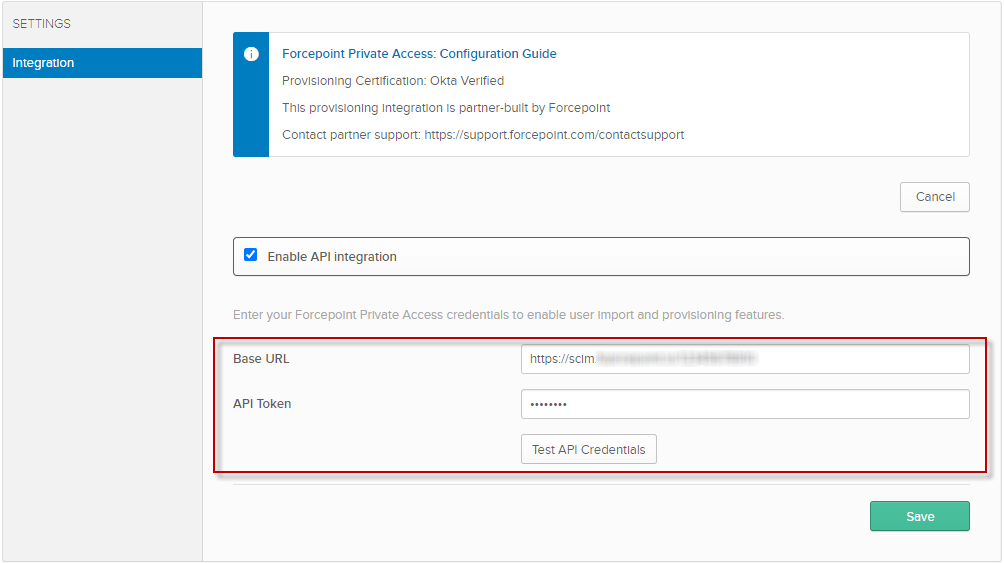
- Click Configure API Integration, then select Enable API Integration.
-
Paste the values you copied into the following fields:
- Base URL
- API Token
-
Click the Test API Credentials button to check that the connection to the Forcepoint SCIM service is
successful.
When you have verified that the connection is working, click Save.
-
When you have saved your integration settings, the To App page becomes available on the Provisioning tab. Go to the To
App page and click Edit.
Important: This step is required to enable User Provisioning.Select the following options:
- Create Users
- Update User Attributes
- Deactivate Users
-
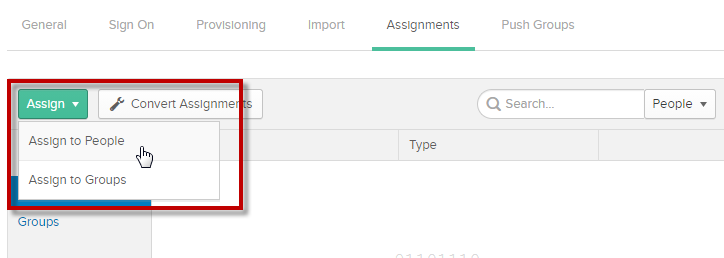
You can assign users to the application individually, or you can assign entire groups to the application. Go to the Assignments tab for your application,
and assign users or groups to the application:
- Click Assign, and select Assign to People or Assign to Groups.
- Search for the users and groups that you want to provision to Private Access, and click Assign for each user and group.
- For any users that you add, verify their user-specific attributes, and click Save and Go Back.
 Note: When you assign a group, all users that are members of that group will be provisioned to Private Access.
Note: When you assign a group, all users that are members of that group will be provisioned to Private Access. -
To provision groups to Private Access, select the Push Groups tab. Add each group that you want to provision into
Private Access.
Important: This step is required to provision groups to Private Access.
-
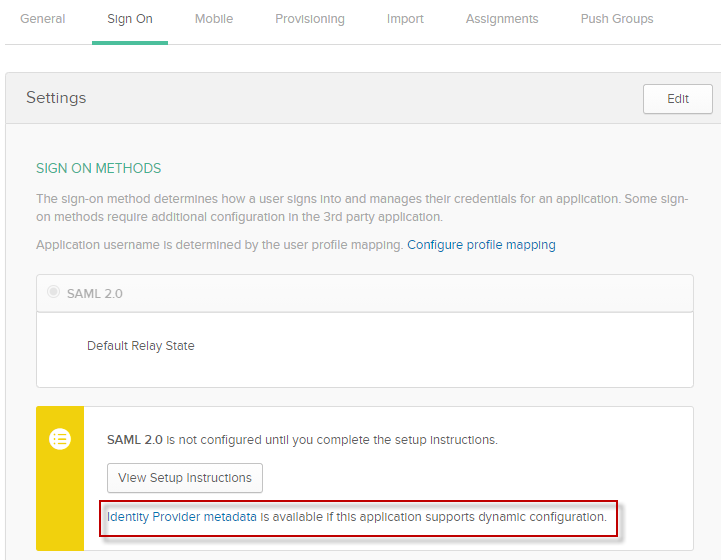
On the Sign On tab for your application, download the Identity provider metadata and save it with a .xml extension.
- In the Private Access management portal, go to Administration > Authentication > Identity provider.
-
Click New.

- Provide a name for the identity provider (for example, "Okta").
-
Copy and make a note of the values in the following fields:
- Service Provider Entity ID
- Service Provider Assertion URL (there may be multiple URLs)
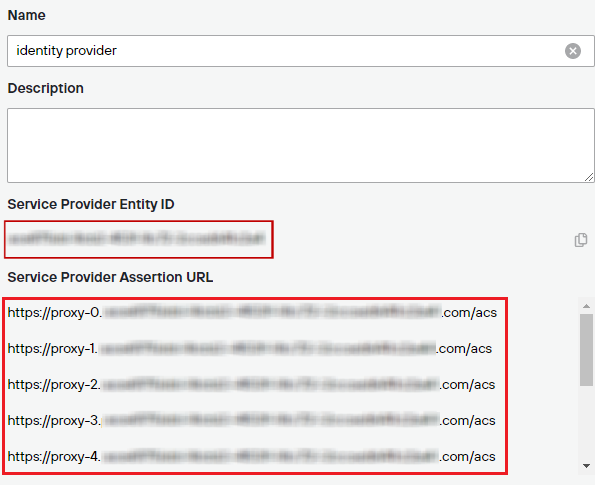
Your entity ID and each ACS endpoint must be configured in your Private Access Okta application to ensure SAML authentication is working properly for each of your configured Private Access Gateways.
- Under Identity provider metadata, click Upload, and select the XML file you saved in step 13. Upload the file.
- In the Domains field, add the domains your organization uses for authentication.
- Click Deploy Changes.
- Return to the Okta portal. On the Sign On tab for your application, click Edit.
-
Scroll down to Advanced Sign-on Settings.
- Set the Service Provider Assertion URL to your first Private Access ACS endpoint from step 19. For example:
https://proxy-1.acme.bba.services.amer.forcepoint.io/acs- Set the Service Provider Entity ID to the value you copied from Private Access in step 19.
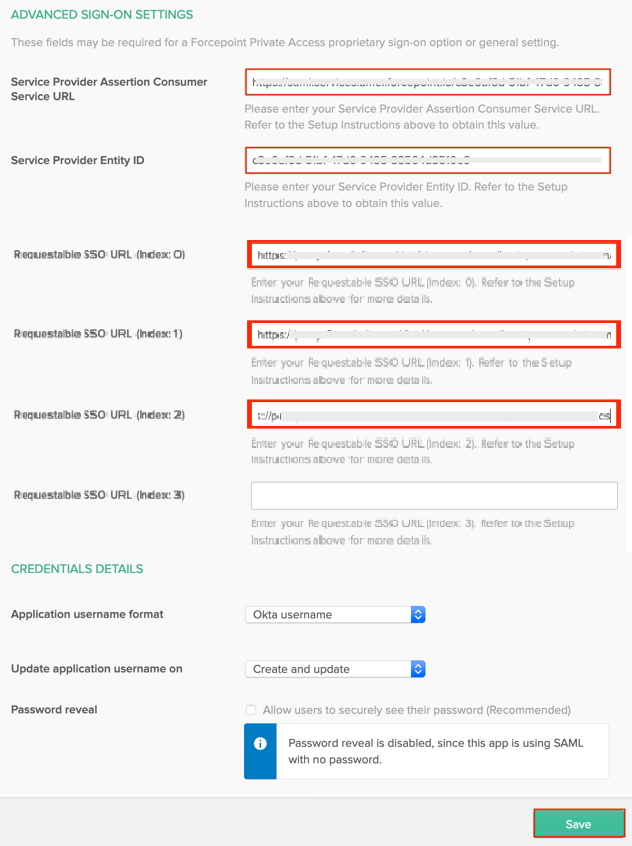
-
Set each available requestable SSO URL:
- In the Index 0 field, enter your second Private Access ACS endpoint.
- In the Index 1 field, enter your third Private Access ACS endpoint.
- Repeat until you have entered all of your available ACS endpoints to your Okta application.
Tip: Each URL is identical except for the sequence number. Copy the first URL and change the sequence number as appropriate.Note: Remember that Index 0 will correspond to https://proxy-1.acme.bba.services.amer.forcepoint.io/acs, and Index 1 will correspond to https://proxy-2.acme.bba.services.amer.forcepoint.io/acs. - Click Save. Your Okta integration is now configured.
If you have any issues with your Forcepoint/Okta integration, contact Forcepoint Customer Hub.
Note: If a user is deactivated in your Okta account, the user will be deleted from the Private Access user directory.