Data theft detection
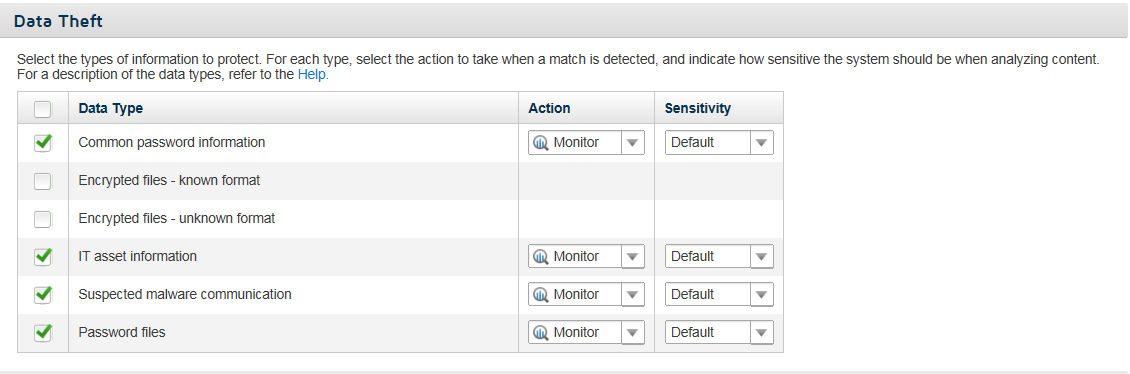
Use this section to detect when data is being exposed due to malware or malicious transactions. When you select these options, Forcepoint Web Security Cloud searches for and reports on outbound passwords, encrypted files, network data, and other types of information that could be indicative of a malicious act.
To see if your organization is at risk for data theft:
- Select the types of data to look for.
Information Type Description Common password information Searches for outbound passwords in plain text Encrypted file - known format Searches for outbound transactions comprising common encrypted file formats Encrypted file - unknown format Searches for outbound files that were encrypted using unknown encryption formats IT asset information Searches for suspicious outbound transactions, such as those containing information about the network, software license keys, and database files. Malware communication Identifies traffic that is thought to be malware “phoning home” or attempting to steal information. Detection is based on the analysis of traffic patterns from known infected machines. Password files Searches for outbound password files, such as a SAM database and UNIX/Linux passwords files - Select an action to take when matching data is detected. Select Block to prevent the data from being sent through the web channel. Select Monitor to allow it. (Incidents are created either way.) You can filter by action in the Data Security Incident Manager.
- Select a sensitivity to indicate how narrowly or widely to conduct the search. Select Wide for the strictest security. Wide has a looser set of detection criteria than Default or Narrow, so false positives may result and performance may be affected. Select Narrow for tighter detection criteria. This can result in false negatives or undetected matches. Default is a balance between the two. Severity is automatically calculated for these types.