Introduction
Use investigative reports to analyze Internet activity in an interactive way.
When you first open the page in the Web module of the Forcepoint Security Manager, a high-level summary report is displayed.
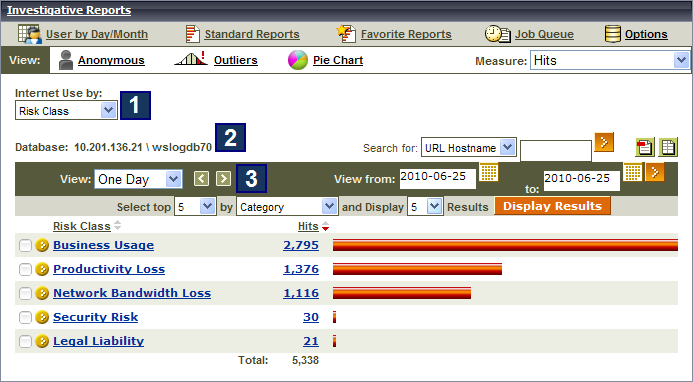
By default, this initial view shows activity:
- Grouped by risk class
Risk classes are groupings of categories used to suggest possible types or levels of vulnerability posed by sites in those categories.
- Recorded in the specified Log Database
- That has occurred since midnight todayTip: You can click Options at the top of the page to change the default time period.
Only activity that you are authorized to see is displayed.
- For self-reporting users, this is information about your own Internet activity.
- For many delegated administrators, this is information about your managed clients.
- For some administrators, this is information for your entire organization.
Use this overview as a quick check for areas of potential concern. Are there a high number of Security Risk or Legal Liability requests? Does the overall amount of activity seem appropriate?
From here, you have several options:
- If the high-level summary shows areas of potential concern, Drill down to find details.
- Use standard reports to get a targeted view of monitored Internet activity.
- Customize summary reports or Customize detail reports to create a report that better reflects your needs.
- For quick reference explaining the types of data that can be included in investigative reports, see What information can I see in a report?.
- Create Favorite reports to minimize the work required to get to the data you need, and optionally schedule them to run at regular intervals.