Once you have the above input information that Forcepoint Data Security Cloud | SSE uses in the
code, you now need to figure out the request information in order to tell the Forcepoint Data Security Cloud | SSE system what to block.
To do so you will need to run an HTTPs inspection when performing the action you wish to control. You can do this from the browser or using a capture tool such as Charles Proxy.
Let's say for example that you want to prevent users from posting to Twitter. Assuming you do not know what the web request info is for this action, you would need to perform a post
action in twitter while inspecting the network traffic.
Steps
-
Open a web browser and logging in to twitter.
-
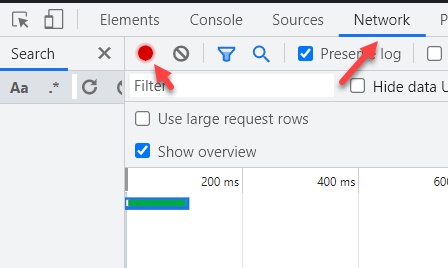
In your web browser, open the Inspect developer tool.
-
Once you have done so, click the Network tab and then ensure the circle icon is red to record traffic.
-
Make a post on twitter.
-
Once the post is done, you can stop the recording and review the web requests.
Depending on the app, you might need to click through a few to find the actual request that performed the action, for Twitter you will see that it is an update.json with the
domain showing as twitter.com. Click into that one.
-
When crafting your Lua code, it is best to be as specific as possible to prevent catching other requests in policy code. Thus when inspecting the traffic, you will need the
following fields of information:
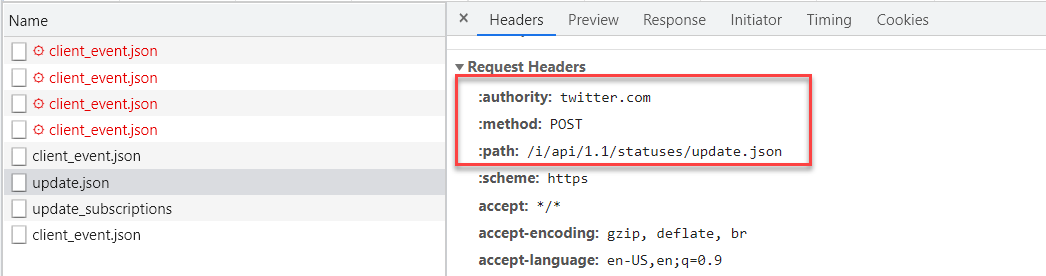
- Method: The method of the transaction, in this case a POST. Forcepoint Data Security Cloud | SSE can also support other methods being used
depending on the action such as GET, PUT, and so on.
- Domain: The domain (authority) of the URL being called, in this case twitter.com
- URL Path: The specific URL Path request that is being made, in this case /i/api/1.1/statuses/update.json
-
With the above information at hand, you can now craft code and insert it into a Forcepoint Data Security Cloud | SSE Advanced Data Pattern.