Creating AWS roles
You will need to create an AWS Role in order to provide access to the management console when going through Forcepoint Data Security Cloud | SSE.
Steps
- Login to the AWS console.
-
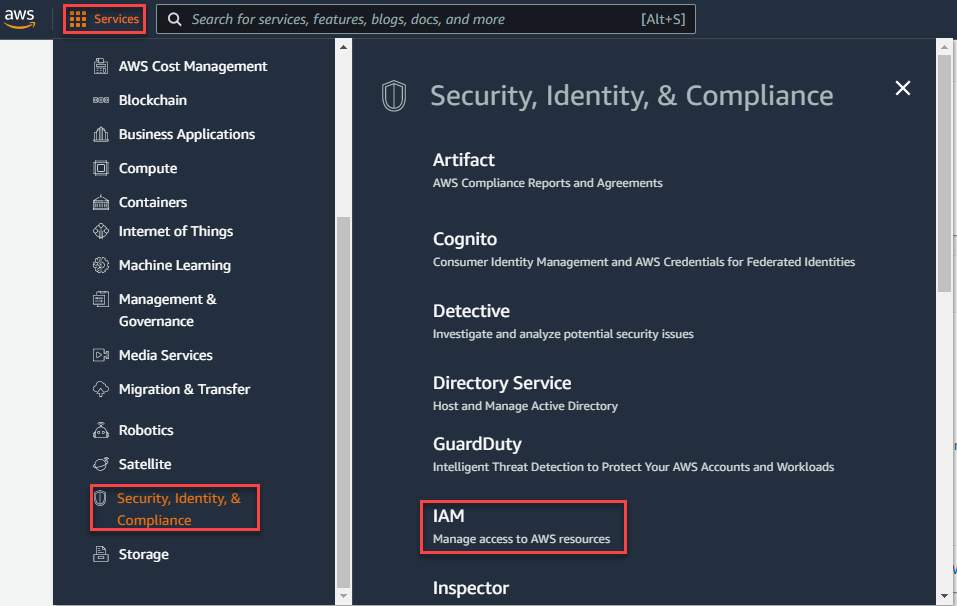
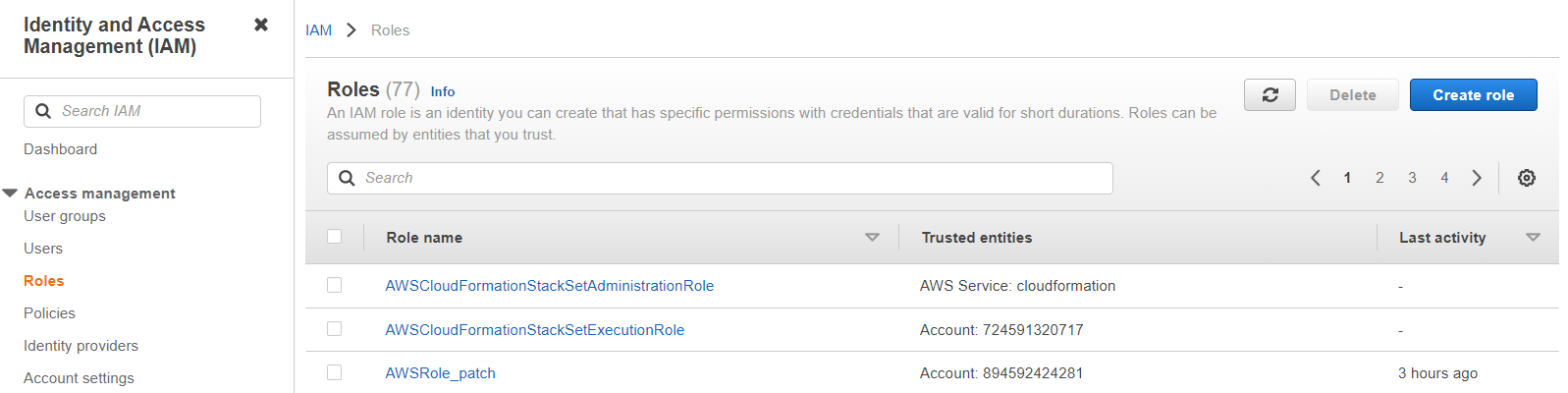
Navigate to the Services > Security, Identity, & Compliance > IAM page and further navigate to Access management > Roles and then click Create role.
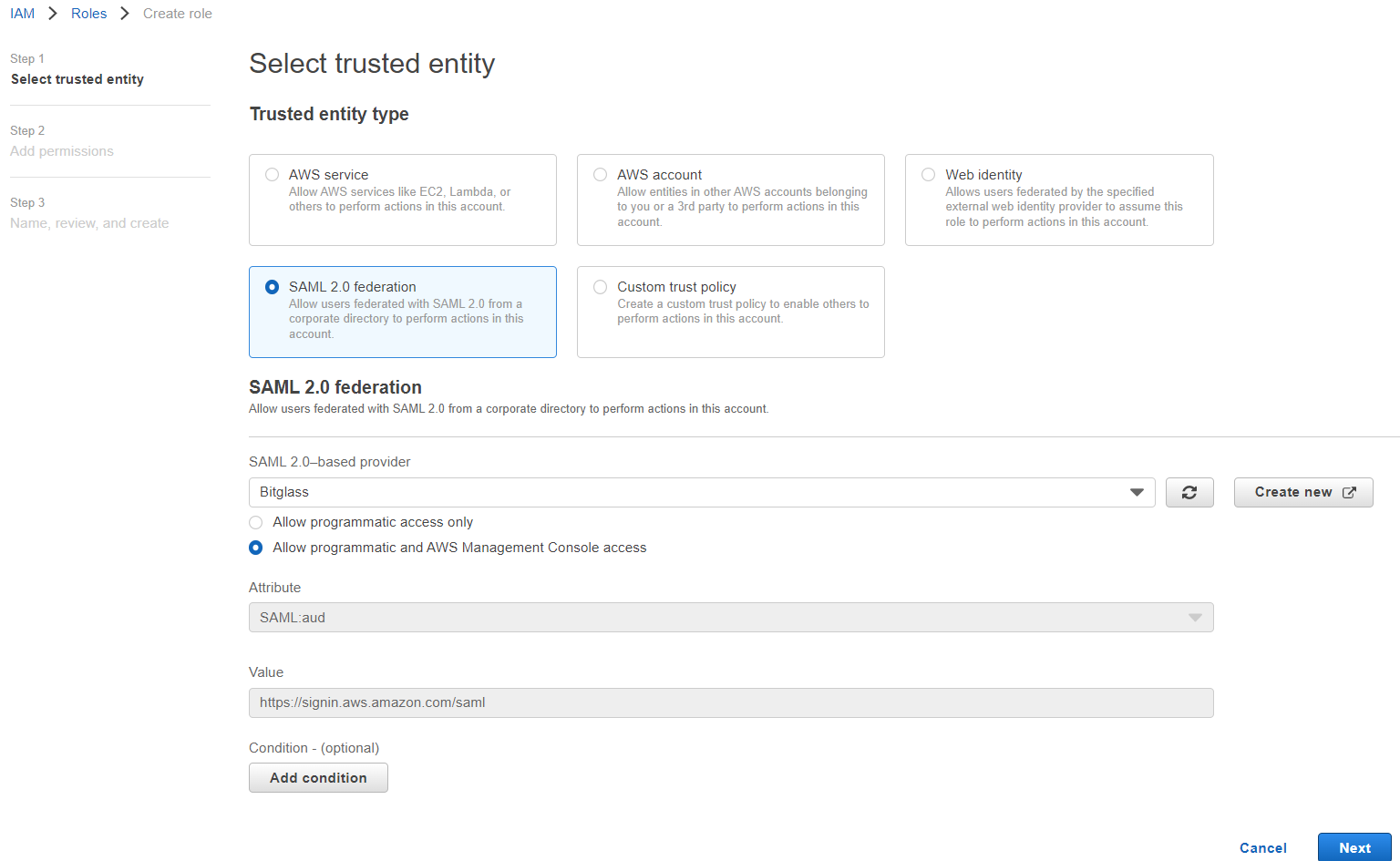
- Select SAML 2.0 federation for the trusted entity and then select the SAML provider that you created in the prior setup above.
-
With the SAML Provider selected, check off the Allow programmatic and AWS Management Console access option and you will notice that
the Attribute and Value fields will automatically populate. Leave Condition blank and click Next at the
bottom.
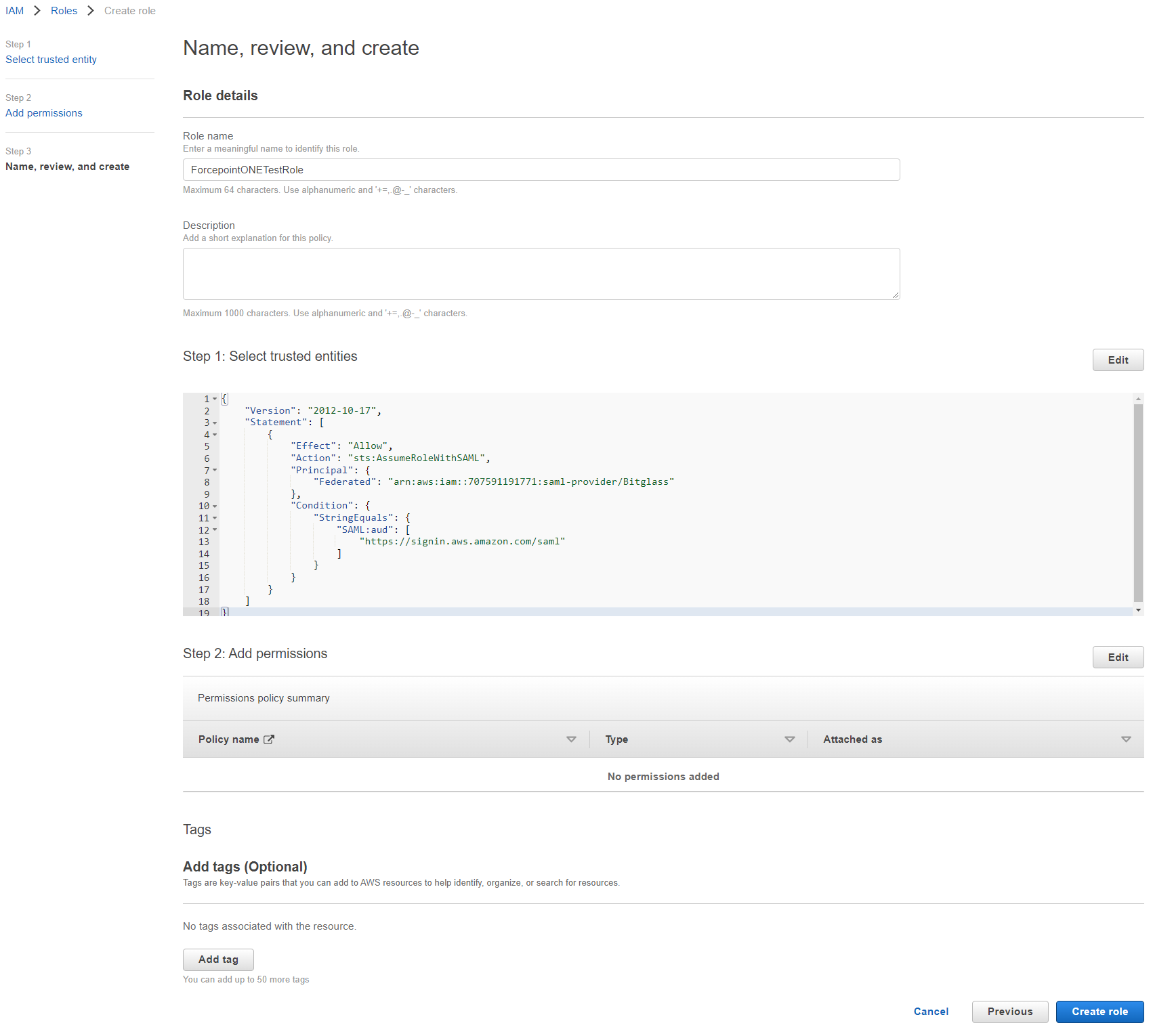
-
You can choose to grant whatever permissions you want for the role. This role will be used by admins accessing the AWS console via Forcepoint Data Security Cloud | SSE. You can create a role to give them only read access,
full admin permissions, or anything in between. Once you have chosen your permission, click Next then on the next page provide a name (and description
optional) and then click Create Role at the bottom.

- Once you are done with the setup, navigate back to Forcepoint Data Security Cloud | SSE and to the Protect > Policies page and scroll down to the AWS application. Before setting up a policy line to send users through Secure App Access (reverse proxy) you will need to setup one policy line for Direct App Access and have an admin or a user login directly once to validate the SAML SSO setup. Once done you can then adjust your policies to start sending people through the Forcepoint Data Security Cloud | SSE proxy.