Set up automatic log collection for Shadow IT reporting
The Discovery Portal page is where you can upload Firewall/proxy logs or setup syslog streaming to be analyzed.
Forcepoint Data Security Cloud | SSE Discovery provides a detailed report to identify the ShadowIT cloud applications your users are interacting with and to identify possible data leakage. Forcepoint Data Security Cloud | SSE utilizes machine learning to scour the web for information about cloud applications so that our Cloud App database is always up to date. This means any time a new app is created or an application’s attribute changes (have they been breached, did they add new features meeting a prior requirement, etc), Forcepoint Data Security Cloud | SSE will see that information and immediately incorporate the app into our database and auto categorize it. Currently our database contains over 600k cloud applications and continues to grow. App Risk scores are computed with a proprietary algorithm that analyzes the reputation of the application relative to other apps in a category, which map to an associated risk level (example: High, Medium, Low). When an app is a member of multiple categories, the median value across categories is reported.
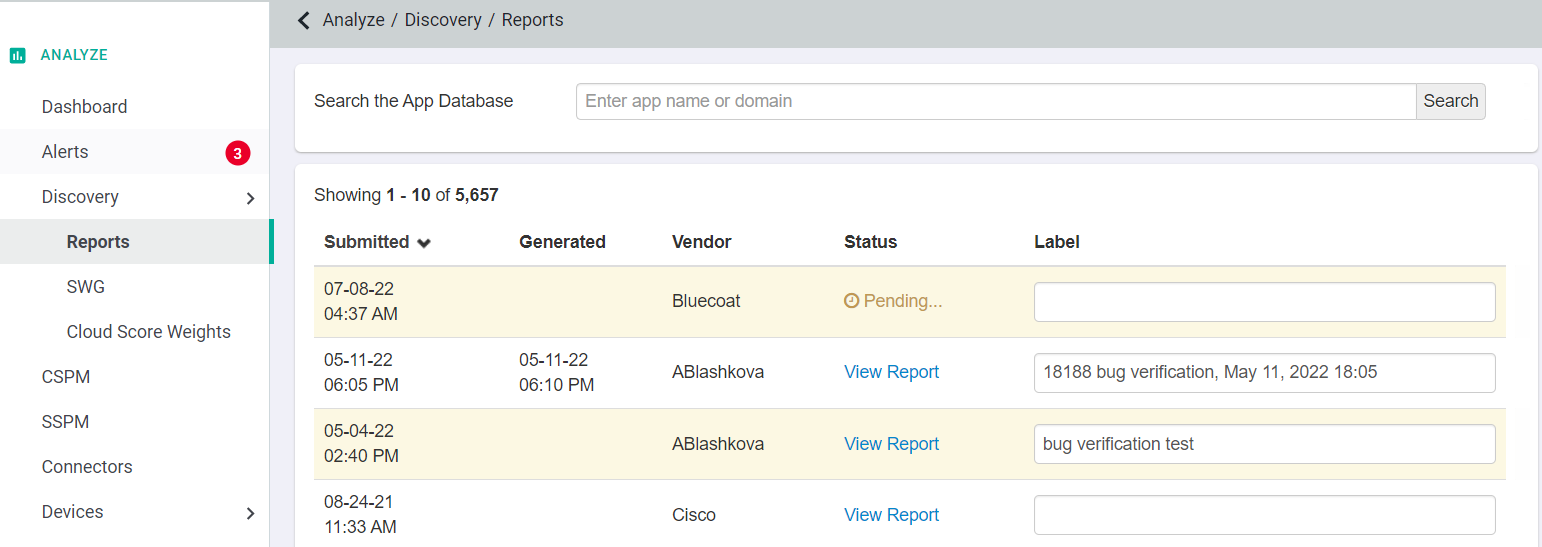
To access the Forcepoint Data Security Cloud | SSE Breach Discovery page, navigate to . This landing page will display all submitted reports, a section to download the syslog collector certificate for syslog streaming, and an option to manually upload a log file.
- Submitted: The date/time when the log was submitted for analysis.
- Generated: The date/time when the report was generated after analysis.
- Vendor: The firewall vendor is used for tracking the types of logs.
- Status: Once the logs are uploaded, the Status changes to pending and later when the report is approved and available for viewing the Status is updated to View Report.
- Label: User defined label for each report.