PingOne: Configuring Forcepoint Data Security Cloud | SSE as a SAML SP
You can configure PingOne as an external IdP inside of Forcepoint Data Security Cloud | SSE.
Before you begin
Note: Forcepoint Data Security Cloud | SSE UI supports UTF-8 characters. However, the SAML
assertion only supports low-ASCII characters as attribute values. If an attribute value contains characters that are not low-ASCII, then SAML sign-in failures occur.
Note: When attempting to setup a new SAML app inside of PingOne, the option will be grayed out until you complete the initial setup.
Steps
-
Login to Forcepoint Data Security Cloud | SSE as an admin and navigate to Protect > Objects > Common Objects and locate the External IDP card. Click the green plus icon to add a new IdP object.
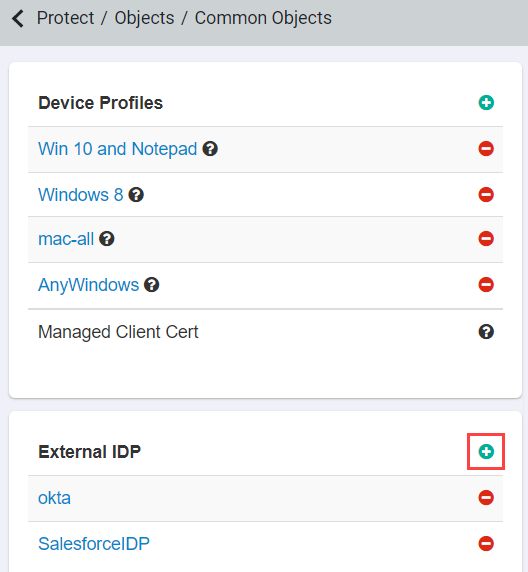
-
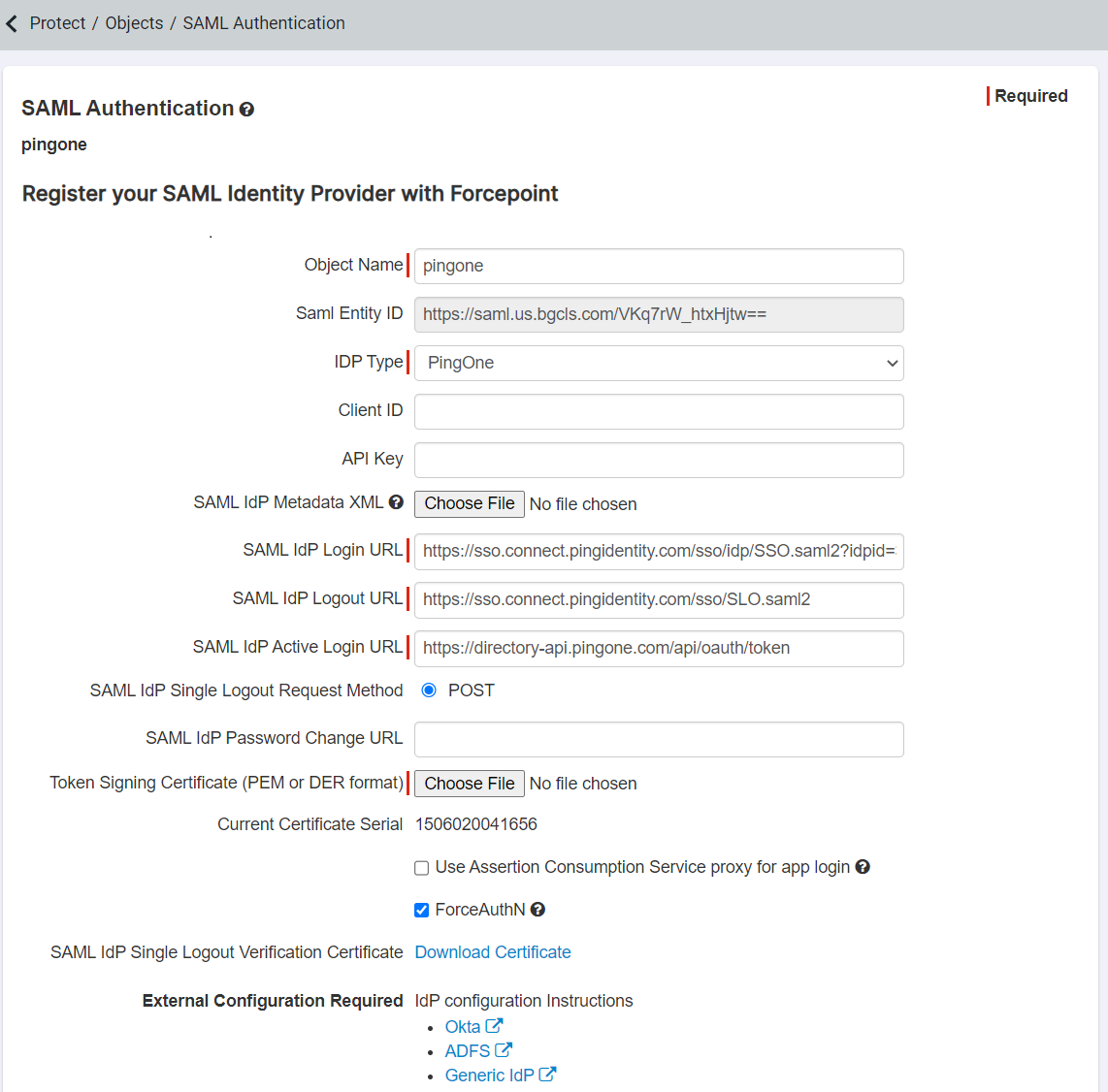
Provide an Object Name (PingOne) and select PingOne from the IDP type drop-down.
In addition, download the SAML IdP Single Logout Verification Certificate at the bottom and save it for later. Leave this page open in it's own tab or window as you will need information from here later on. To configure the rest of the settings on this page, you will need to begin your configuration inside of PingOne.
- Login to the PingOne admin console with an administrator account.
-
From the left pane, expand Application and click on the Applications tab:
- On the Applications page, click + next to Applications.
-
On the Add Application section, enter Application name, description, icon for application, and set the Application Type to
SAML Application.
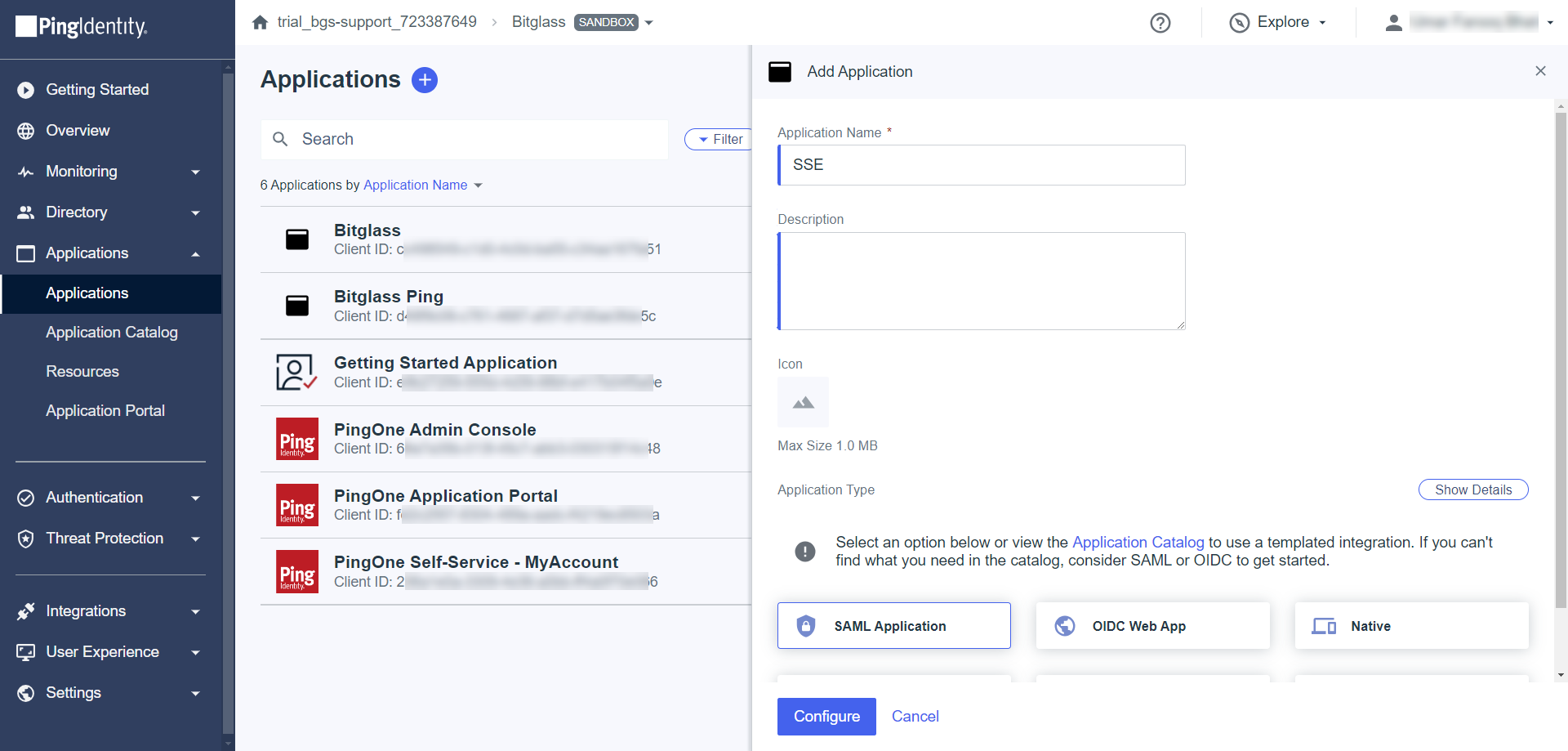
- Click Configure.
-
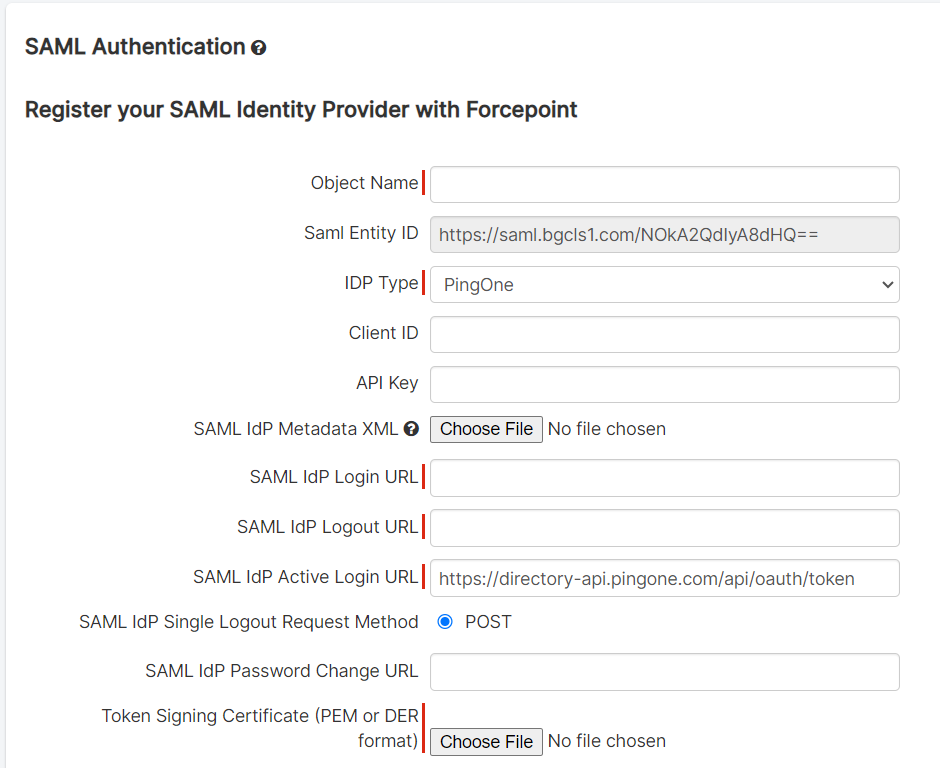
On the SAML Configuration tab, set Provide Application Metadata to Manually Enter option, add ACS URLs and
Entity ID:
- ACS URLs: https://portal.bitglass.com/sso/acs/
- Copy the Entity ID from your Forcepoint Data Security Cloud | SSE IdP setup page and paste it here.
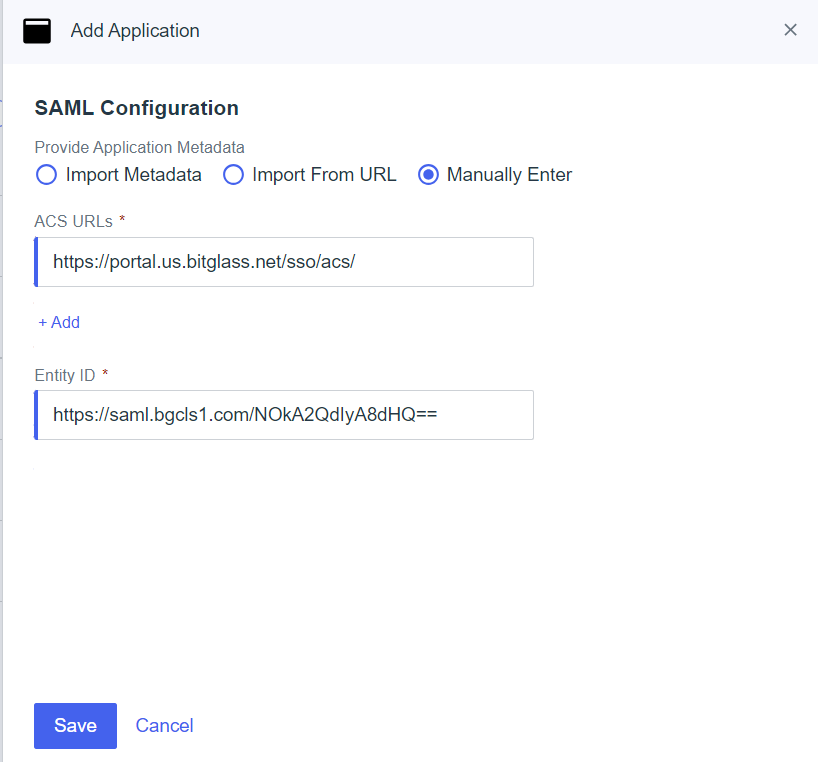
- To create the application, click Save.
-
On the Attribute Mappings tab:
- On the upper-right corner of the page, click the edit icon.
-
Under pre-existing saml_subject attribute, select Email Address.
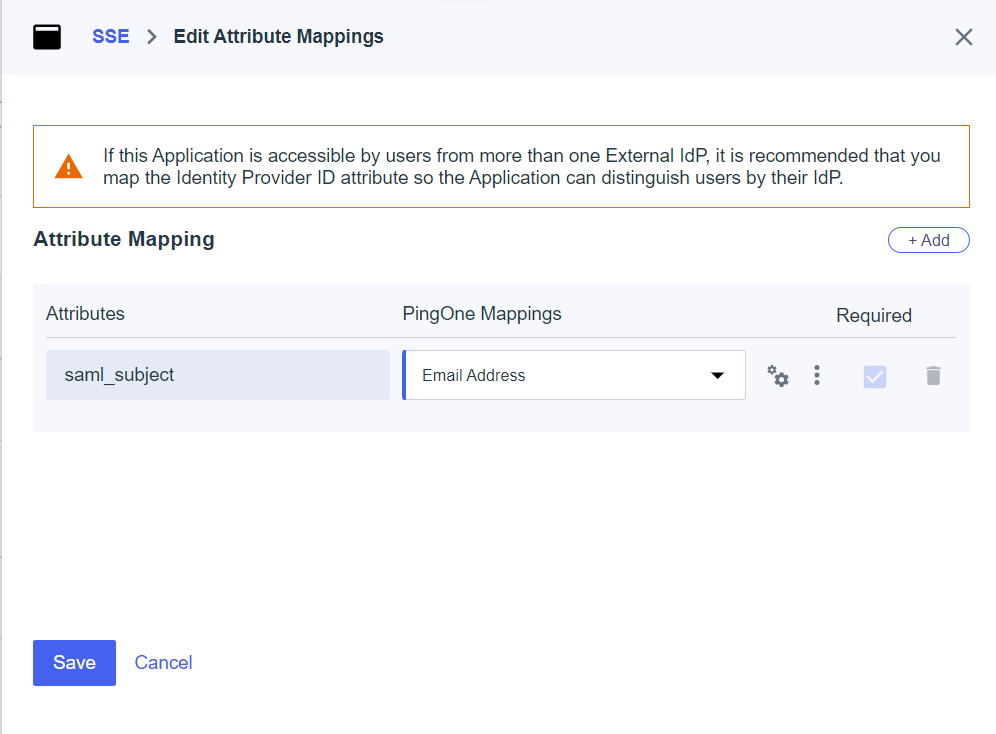
- Click Save.
-
On the Configuration tab:
- On the upper-right corner of the page, click the edit icon.
- From the Subject NameID Format drop-down, select urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress.
- Click Save.
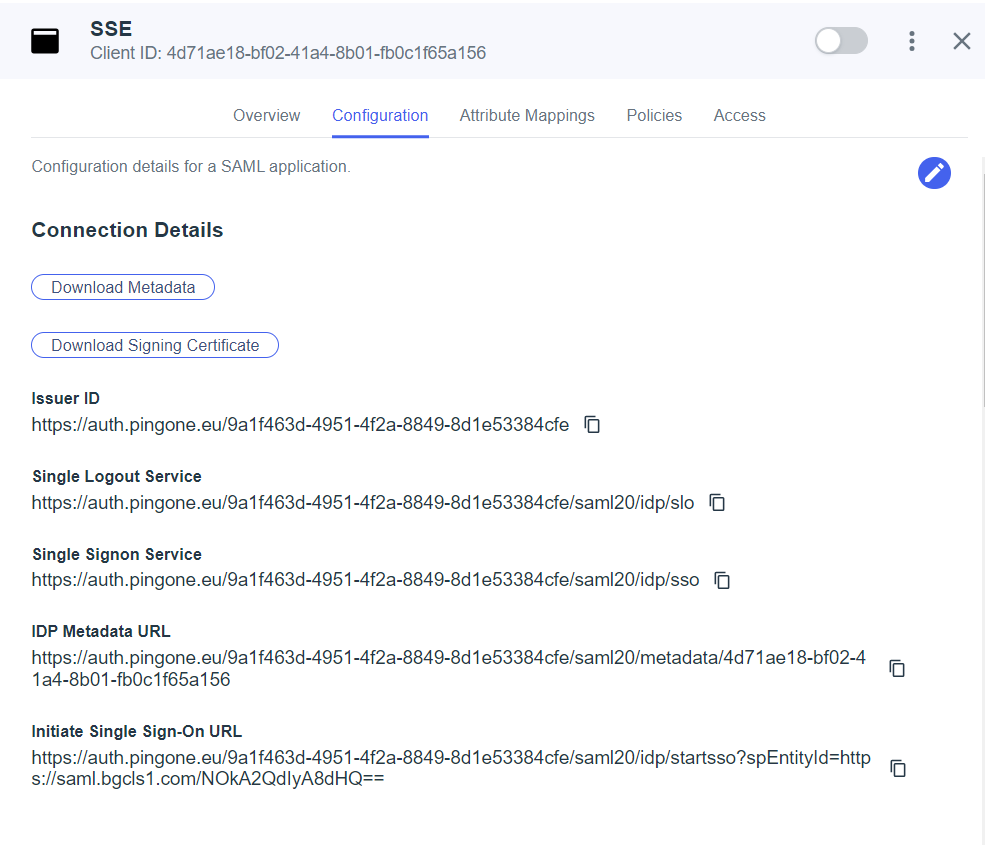
- Click Download Metadata to download the metadata file.
- Click Download Signing Certificate and select X509 PEM (.crt) option to download the certificate in PEM or DER format.
-
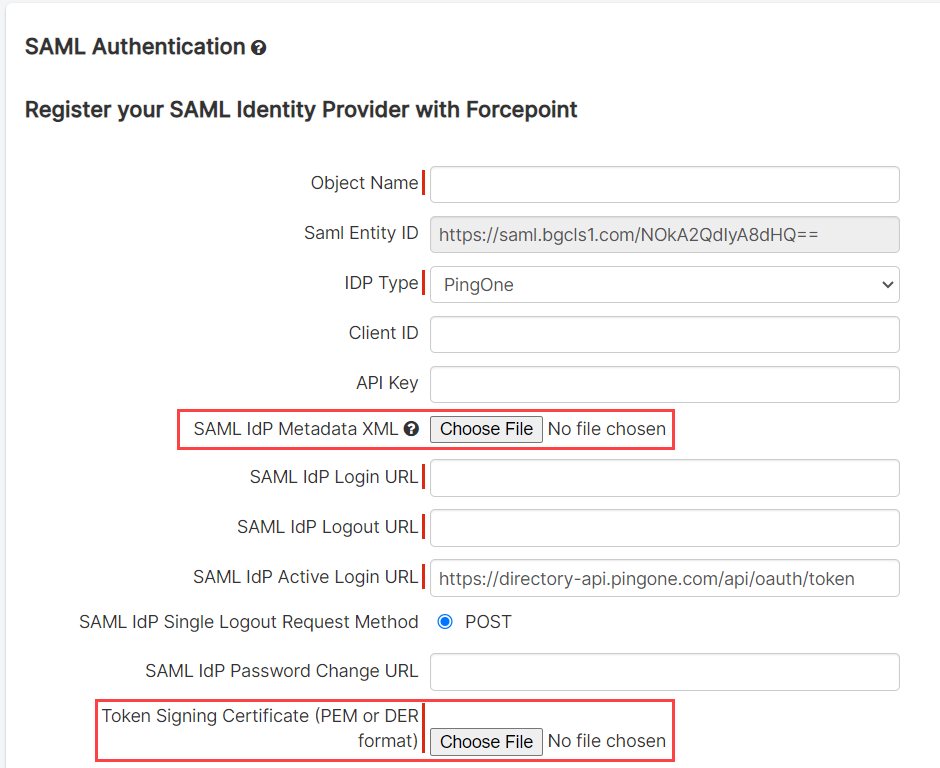
Back on Forcepoint Data Security Cloud | SSE browser tab that is still open, upload the following:
- Upload the metadata file you just downloaded to the SAML IdP Metadata XML field. It should populate both the Login and Logout URLs.
-
Upload the Token Signing Certificate that you just downloaded.
Note: Refer to the PingOne guide page as there are different logout behaviors depending on the SLO URL you choose to use. -
Use the object to apply to your entire domain on the Users and Groups page or per individual application/app instance.
Note: Changes to the SAML application settings on PingOne will take effect only after the updated metadata file is uploaded to Forcepoint Data Security Cloud | SSE after saving the configuration changes on the PingOne console.