Configuring Okta to support custom Forcepoint Data Security Cloud | SSE as SAML SP
You can configure Okta to support custom Forcepoint Data Security Cloud | SSE as a SAML Service Provider. If Okta is not the first IdP you are configuring in Forcepoint Data Security Cloud | SSE, you should create custom Forcepoint Data Security Cloud | SSE as an application inside of Okta and then configure Okta as the external IdP inside of Forcepoint Data Security Cloud | SSE.
Before you begin
Steps
- Sign-in to Okta as an administrator.
-
In the Admin Console, navigate to Applications > Applications and then click Create App Integration.
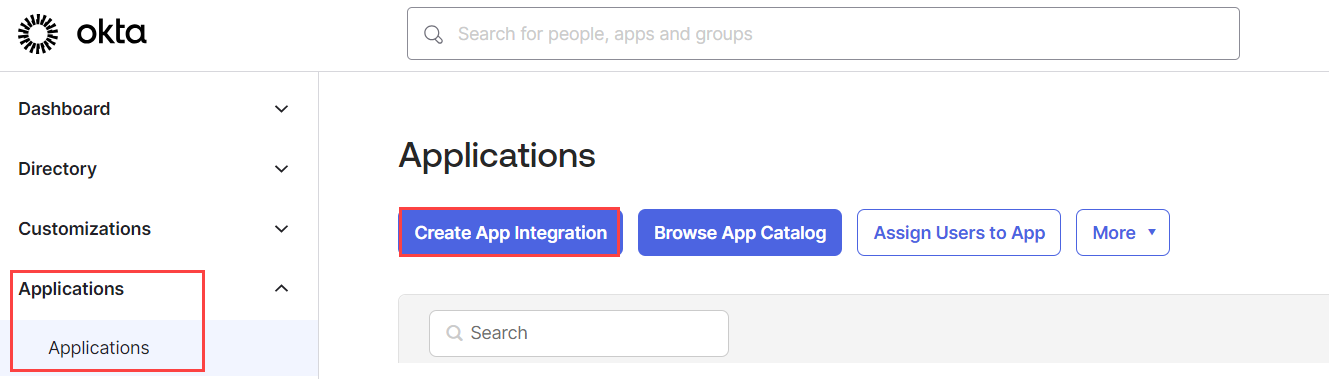
Create a new app integration pop-up opens displaying the available sign-in methods.
-
Select SAML 2.0 as the Sign-in Method for the Forcepoint Data Security Cloud | SSE application and click
Next.
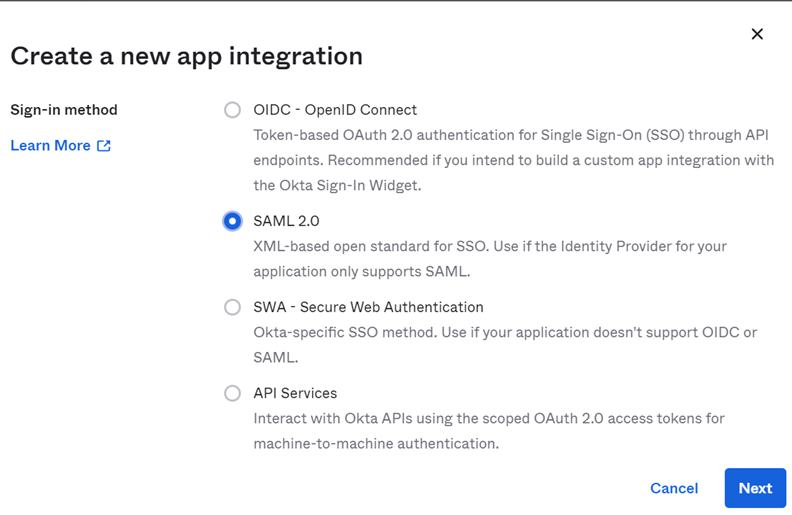
The Create SAML Integration page opens.
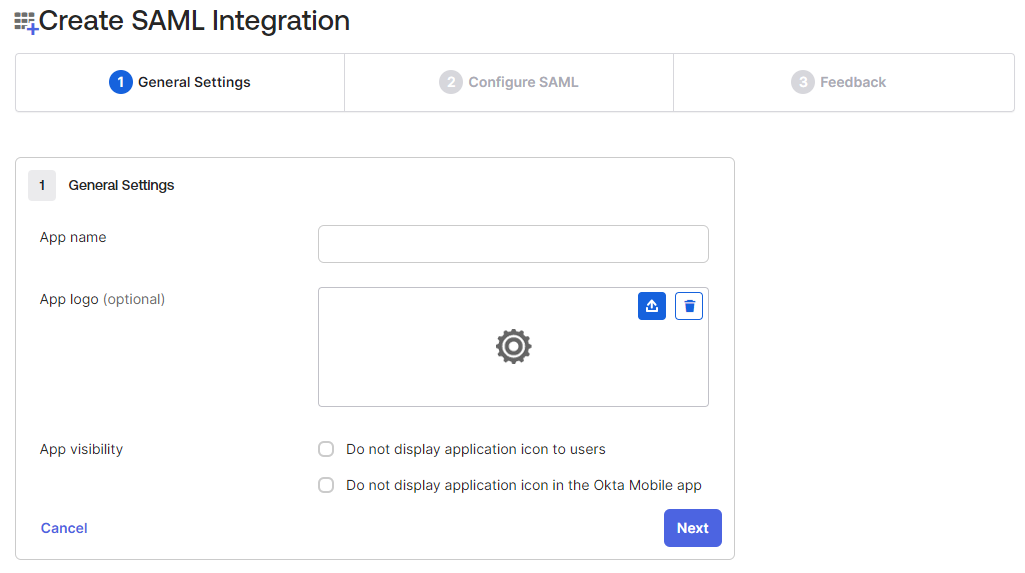
- On the General Settings tab, enter the App name to distinguish the application, upload an App logo if required and then click Next to enter SAML settings.
-
Enter the following SAML Settings for the Forcepoint Data Security Cloud | SSE production environment:
- Single Sign on URL: https://portal.bitglass.com/sso/acs
Make sure Use this for Recipient URL and Destination URL checkbox is checked as the same URL is used as recipient URL and destination URL.
- Audience URI (SP Entity ID): https://sso.bitglass.com
If Okta is not the first IdP that you are adding to Forcepoint Data Security Cloud | SSE, then you will need to change the Audience URI (SP Entity ID) field to https://saml.bitglass.com/<string> that you find on Forcepoint Data Security Cloud | SSE's SAML Authentication page.
- Default Relay State: bg_portal_login
Note: You may also specify a continue URL in the Default Relay State if you wish to direct the SSO users directly into an app after clicking the Forcepoint Data Security Cloud | SSE button in Okta. The Forcepoint Data Security Cloud | SSE icon can be changed to the app icon in Okta and can used for a single app. To learn about setting up the Default Relay State, refer to the Advanced IdP Settings.
- Name ID Format: EmailAddress
- Application username: Okta username
- Update Application Username on: Create and update
Note: To view following settings, click the Show Advanced Settings checkbox.
- Response: Unsigned
- Assertion Signature: Signed
- Signature Algorithm: RSA_SHA256
- Digest Algorithm: SHA256
- Assertion Encryption: Unencrypted
- Enable Single Logout: Leave Unchecked
- Authentication context class: PasswordProtectedTransport
- Honor Force Authentication: No
- SAML Issuer ID: http://www.okta.com/${org.externalKey}
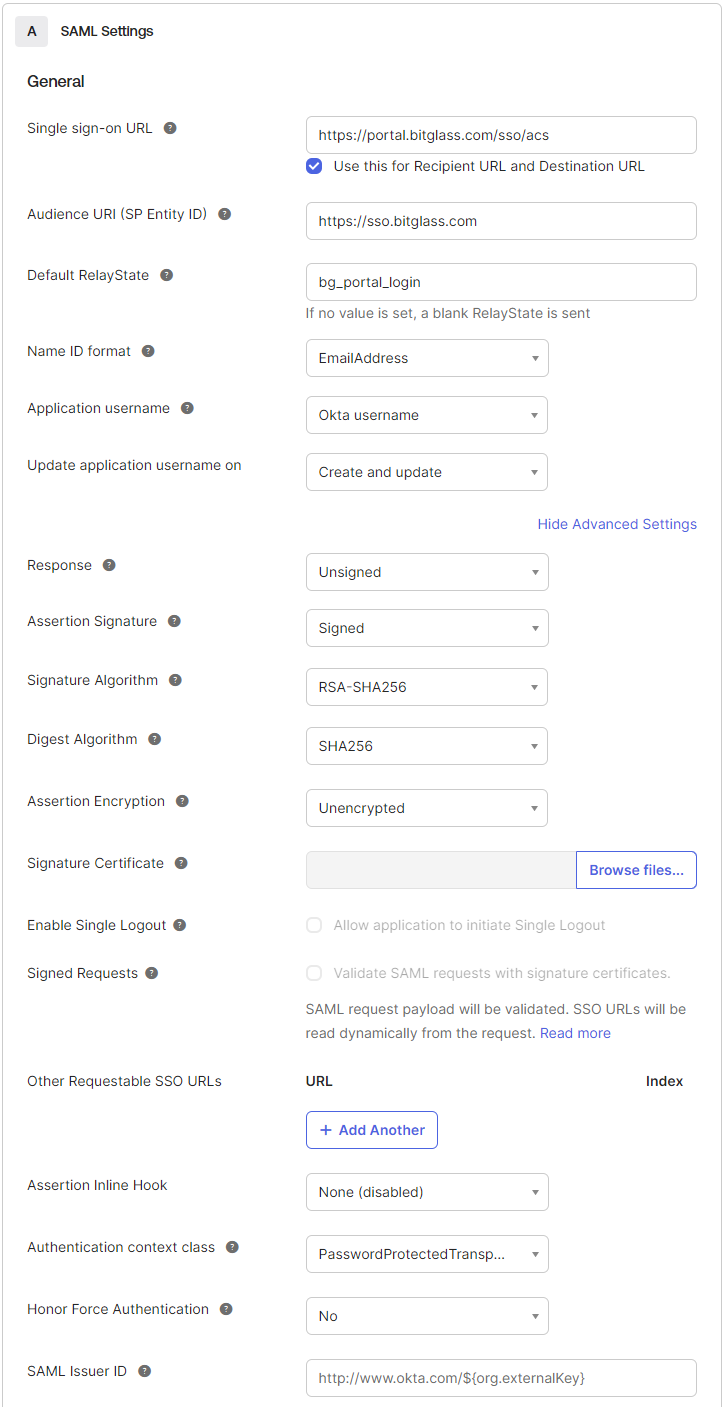
- Single Sign on URL: https://portal.bitglass.com/sso/acs
-
On the Feedback tab, select I'm an Okta customer adding an internal app radio option and then select This is an internal app
that we have created checkbox as App Type.
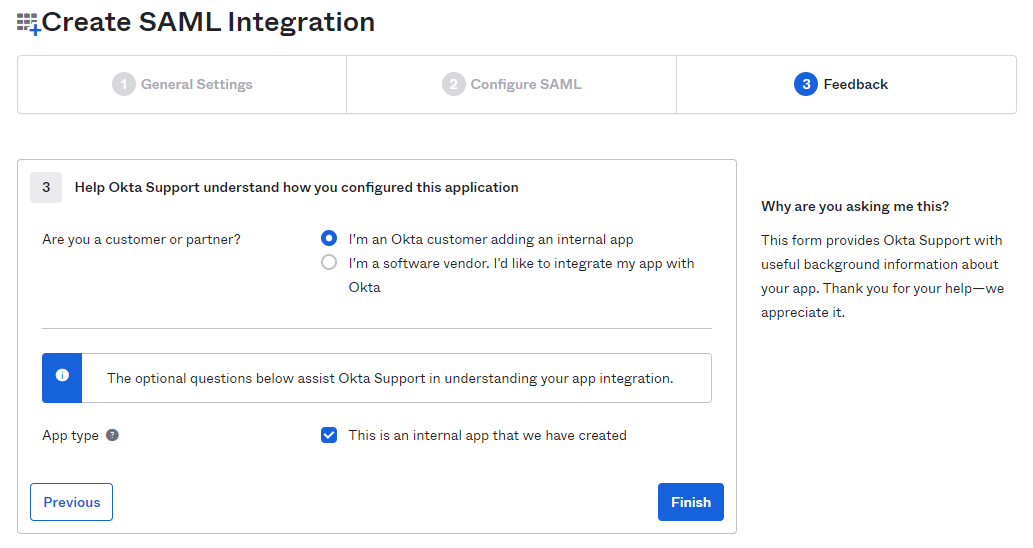
-
Click Finish to create the custom application.
The Custom application opens displaying Sign On tab.
-
On the Assignments tab, click Assign > Assign to People or Assign to Groups to assign the application to the appropriate users or groups.
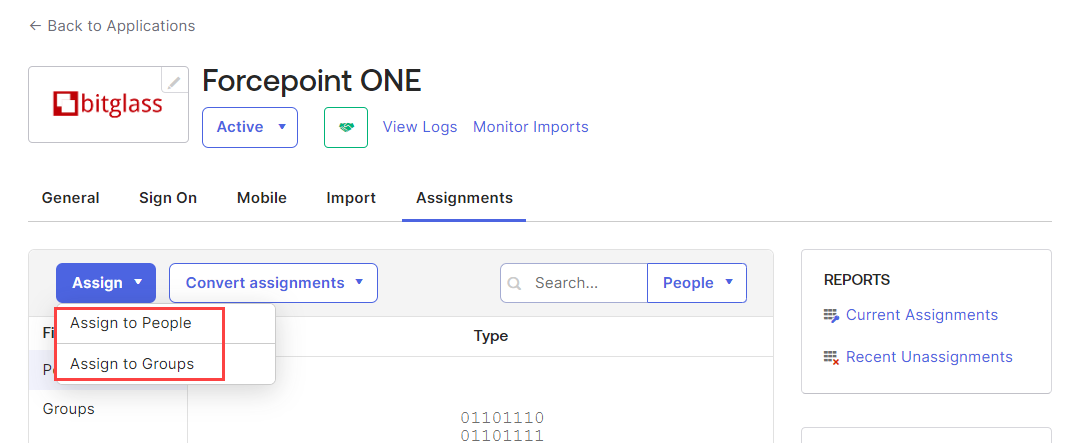
-
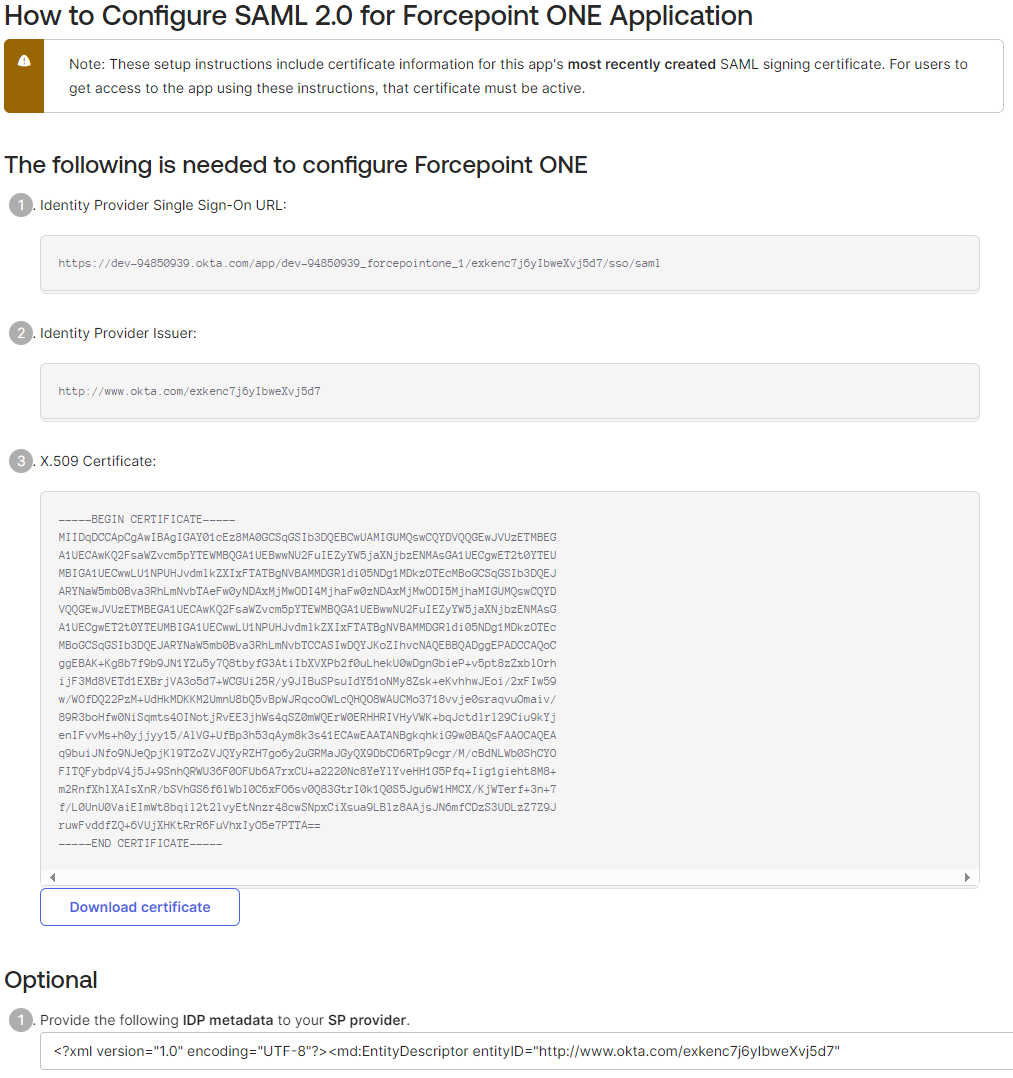
In the Admin Console, navigate to Applications > Applications > Forcepoint ONE > Sign On and then click View SAML Setup Instructions.
A new browser window opens displaying the SAML settings, which are used in Forcepoint Data Security Cloud | SSE setup later.
-
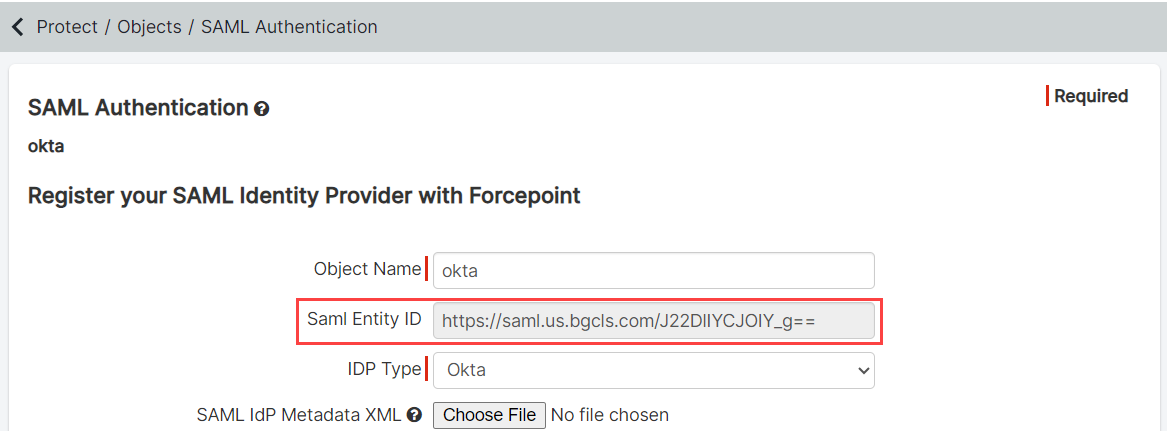
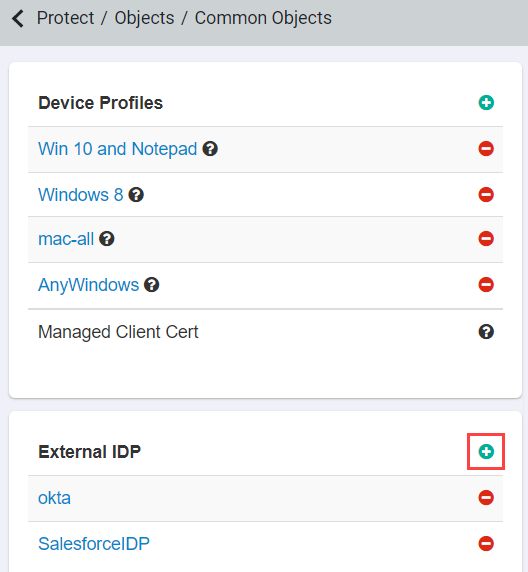
Log into the Forcepoint Data Security Cloud | SSE portal as an admin, navigate to Protect > Objects > Common Objects and scroll down. Locate the External IdP card and click the green plus icon to add a new IdP.
-
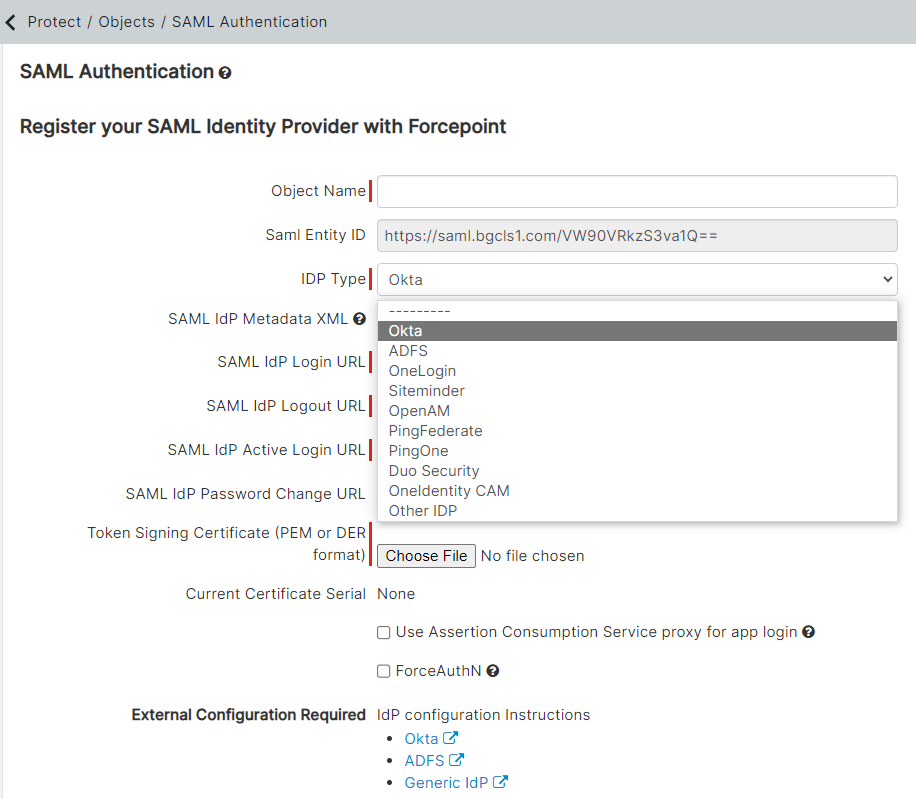
On the SAML Authentication page, enter an Object Name to recognize the IdP and then select Okta as the
IDP Type.
-
Copy the following details from the Okta Setup Instructions (Step 9) and paste those details into the respective Forcepoint Data Security Cloud | SSE fields.
- Copy the SAML IDP Login URL details from OKTA setup page and paste it in the Forcepoint Data Security Cloud | SSE portal under the SAML IDP Login URL field.
- Copy the SAML Logout URL details, that is your Okta domain and then /login/signout, from OKTA setup page and paste it in the Forcepoint Data Security Cloud | SSE portal under the SAML IDP Logout URL field. For example, it is https://bitglass3.okta.com/login/signout.
-
Download the Token Signing Certificate by clicking the Token Signing Certificate link from Okta setup page and then upload the
token signing certificate to the Forcepoint Data Security Cloud | SSE portal under the Token Signing Certificate field.
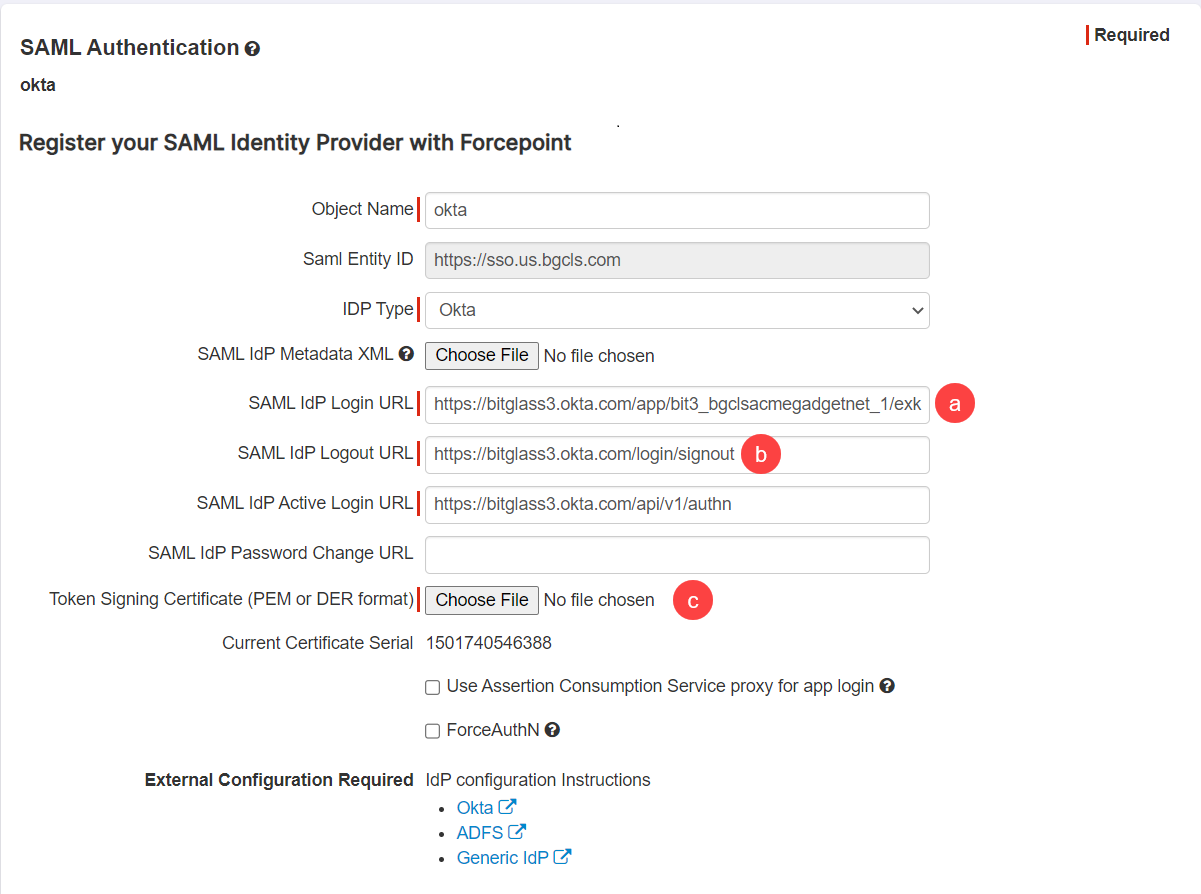
-
Once you are done, click Save at the top to save the new IdP object.
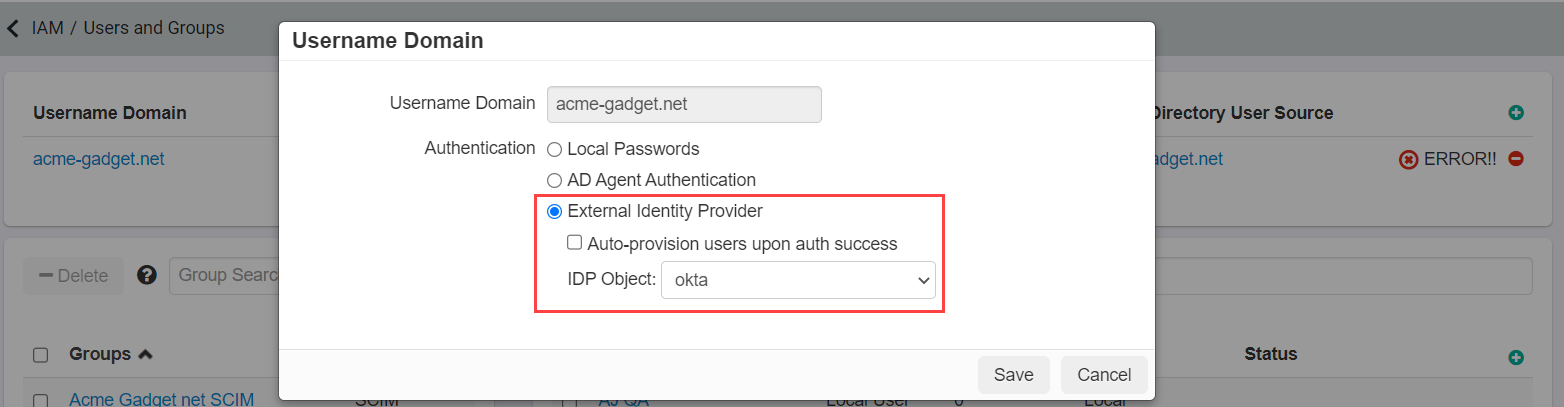
If you only have one IdP object configured, that object will be used by default for your domain on the Users and Groups page. If you have more than one IdP, you will need to choose which one is used by default under the domain options or by app instance.
- To setup the default IdP for the domain, navigate to the IAM > Users and Groups page and select your email domain to open up the options dialog. Make sure that External Identity Provider is selected and then select
your IDP object you just created from the drop-down.
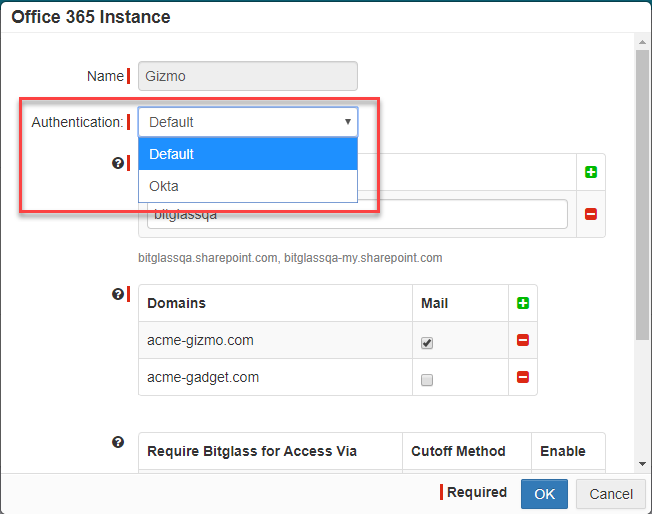
- If you wish to configure IdP individually per app instance, navigate to the Protect > Policies page and select your application that you wish to make changes to. On the application's settings page, select the app instance and in the new dialog select
the IdP you just created from the Authentication drop-down.
- To setup the default IdP for the domain, navigate to the IAM > Users and Groups page and select your email domain to open up the options dialog. Make sure that External Identity Provider is selected and then select
your IDP object you just created from the drop-down.
-
Test the configuration by opening a new browser window (or incognito window) and attempt to login to https://portal.bitglass.com as one of the Okta
assigned users. You should be redirected to the Okta login page where you need to enter credentials before being redirected back to the Forcepoint Data Security Cloud | SSE.