Introduction
Forcepoint Data Security Cloud | DLP secures your data everywhere. The Data Loss Prevention (DLP) application prevents sensitive data exfiltration across cloud, web, email, and endpoint. Policies and incidents are managed from a single platform hosted in the cloud.
The solution combines Data Loss Prevention, Device Control, User activity monitoring, and Endpoint management in a single cloud delivered service that is easy to deploy and use. The service includes an endpoint agent that runs on Windows and macOS.
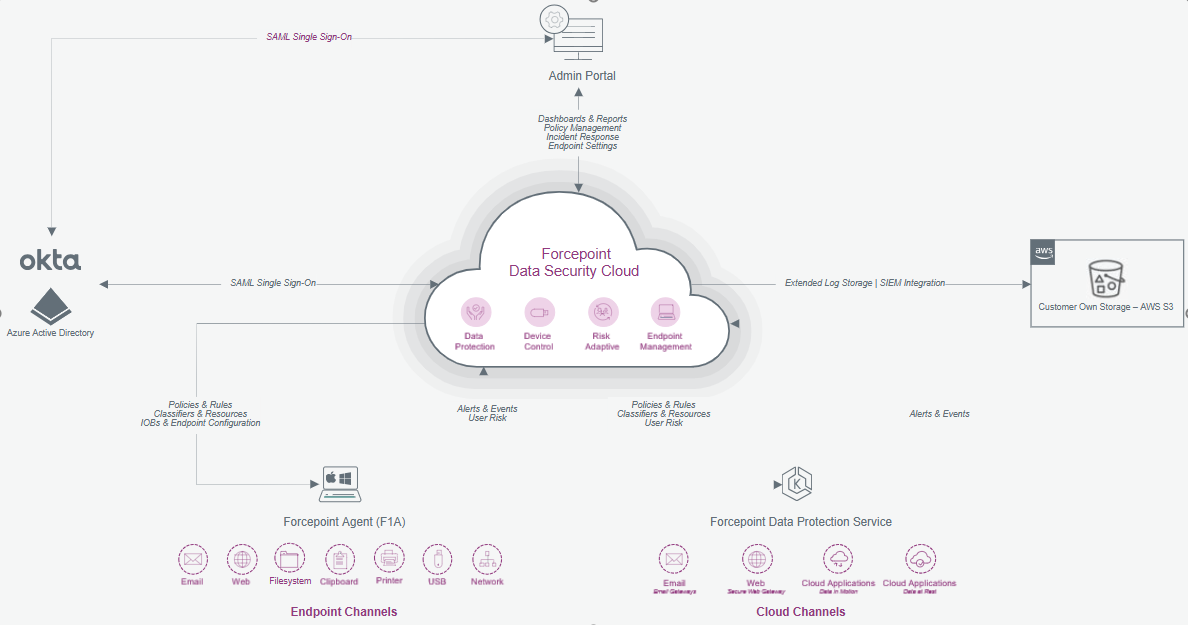
It enables a user centric approach to Data Security and allows organizations to easily extend Data Security across user endpoints, whether online or offline as well as user activities via the organization network on unmanaged devices.
Endpoints are managed using a policy that is applied locally without compromising performance or user experience and does not depend on an active network connection. This ensures that an organizations data security policies are always consistently applied regardless of how that device is connecting to the network or being used. User experience is also optimal as policy decisions and enforcement are not dependent on the cloud and do not add any additional network latency.
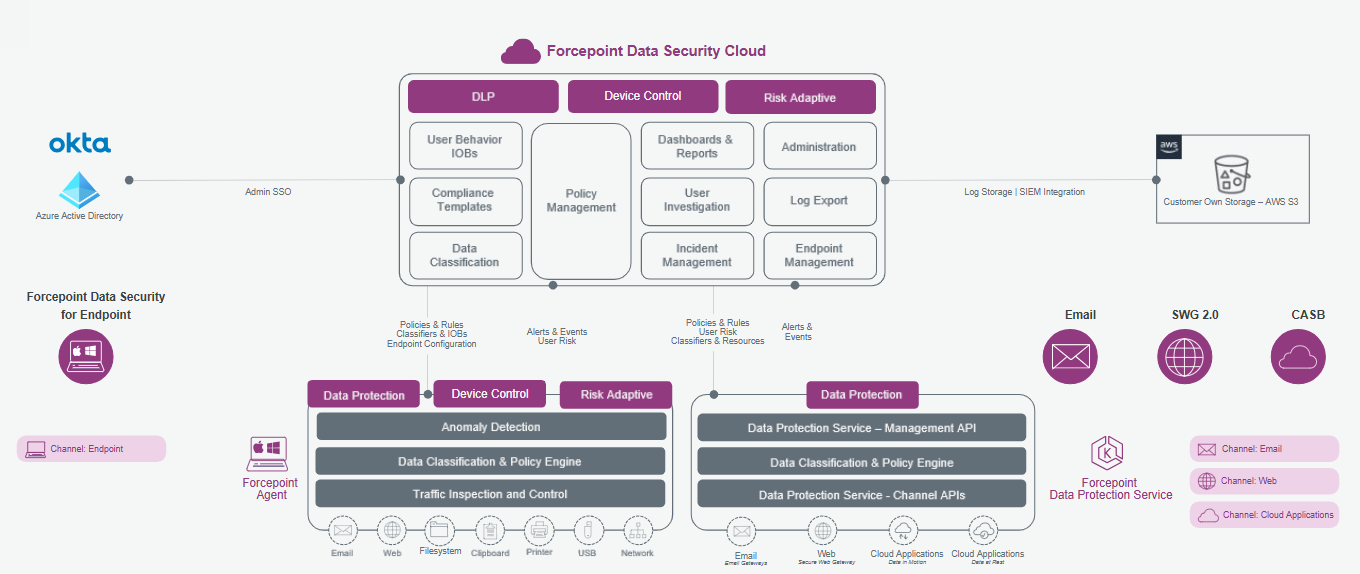
The following modules are supported:
- Data protection: Enables organizations to protect sensitive data from unauthorized access, use, and disclosure. It uses a combination of content inspection and context analysis to
identify and protect sensitive data across a range of data types. It covers the following channels:
- Endpoint channel: File system, Applications, Printers, Network, and removable storage devices.
- Email – Cloud Email, Endpoint Email.
- WEB – Online WEB, Endpoint WEB.
- Cloud – CASB - Inline, API.
- Device control: Allows organizations to manage the use of removable storage devices by adopting a zero-trust approach. Organizations can limit the use of devices to certain manufacturers, removable devices models, or even individual removable devices. Rules can be specified globally or for specific groups or individual users. Granular controls enable organizations to set read-only or read-write policies and monitor any files transferred to and from removable devices. This helps to enhance security by preventing unauthorized access or data theft through removable devices.
- User Activity Monitoring (Risk Adaptive Protection): Extends your Data Security solution with User Activity Monitoring. It continuously monitors user behavior and calculates a risk score using Forcepoint Indicator of Behavior (IOB) analytic models. No additional configuration is required. The necessary context is applied to each event, and if Indicators of Behavior are detected, then the alerts are generated, and the user's risk score is raised accordingly. Continuous monitoring and risk calculations enable a risk adaptive approach to Data Security as the policy dynamically adjusts based on this risk score and proactively tailors’ security to stop data theft before it happens.
- Endpoint management: Enables granular visibility and control of your Forcepoint Endpoint Agent estate. It provides centralized visibility into deployed endpoints, including information on software versions, logged-in users, and enabled features. With this level of visibility, administrators can easily manage their Forcepoint endpoints and enforce data security policies from a single cloud portal, streamlining user and device compliance with organizational policies and standards. This helps to improve the security and efficiency of the organization's endpoint management while reducing the administrative burden on IT teams.