Configuring API settings
Once Forcepoint Data Security Cloud | SSE has been authorized to access Microsoft 365 you will be able to setup the API settings. This section will walk you through the specific Microsoft 365 API settings that you can adjust.
To learn how to create API policies, refer to Configuring API policies. Start on the API setup page for Microsoft 365.
The Microsoft 365 API setup page allows you to choose whether you want to scan One Drive, Sharepoint, or both and to determine what is included or excluded in those scans (users or sites). This is also the page where you will add the DLP Patterns that will appear when creating and managing your cloud policy actions.
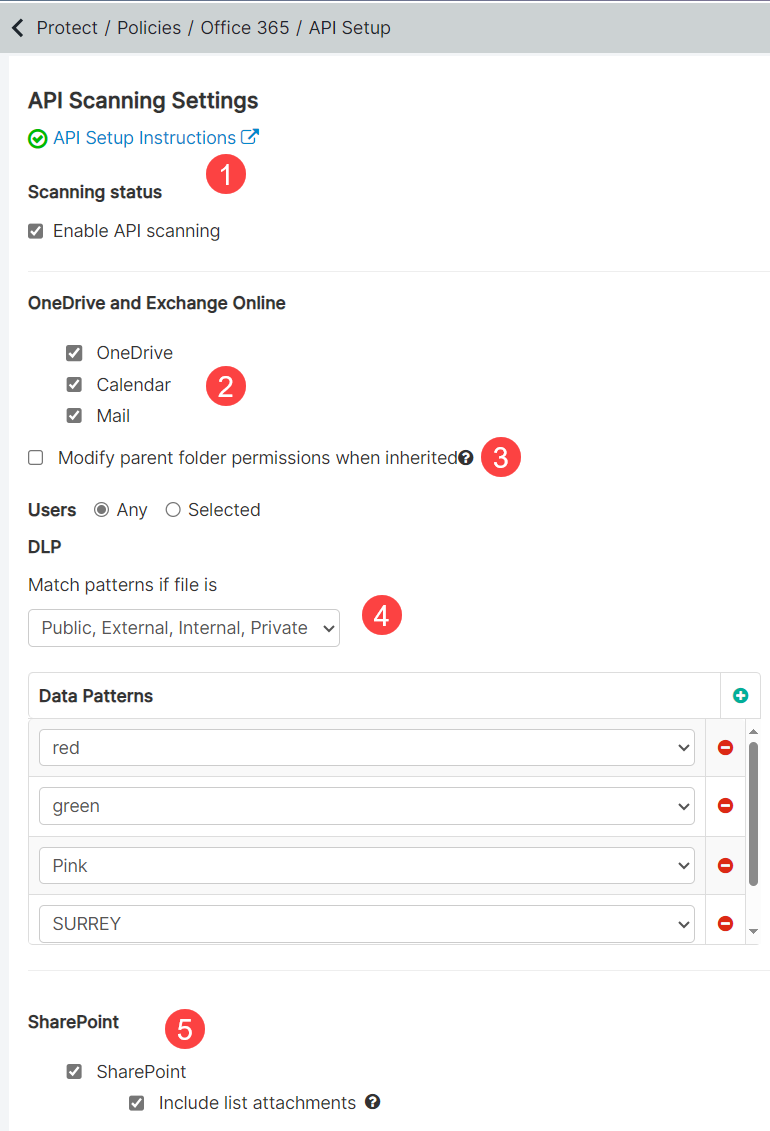
- The top section indicates whether the API is successfully setup. A green check mark indicates that the API has been successfully authenticated and you can proceed with configuring your scanning settings. A red x would indicate setup is not complete or authorization failed.
- This section is all about configuring your scanning settings for OneDrive and Exchange Online. Here you can choose which repositories you are scanning (OneDrive, Calendar, Mail) and who is included or excluded in the scans.
- Select the Modify parent folder permissions when inherited checkbox to remove the share permissions of the parent folder if a file matches a remove sharing policy and the share is inherited from a parent folder. To understand the behavior of unshared file in different situations, refer to M365 Remove Sharing Behavior.
- Here you can configure what you are looking for in your scans. You can look for the specific sharing status of a file as well as add the DLP data patterns that you want to
identify.Note: To configure API policies with the Forcepoint DLP data pattern, refer to Configuring FSM controlled policies for CASB and SWG channels.
- You can configure scanning of Sharepoint sites separately down here.
- Check the box and then select one of the following options to enter the sites you want to include in the scans:
- All: Select this option to include all the sites in the scan
- Selected: Select this option to include only specific sites
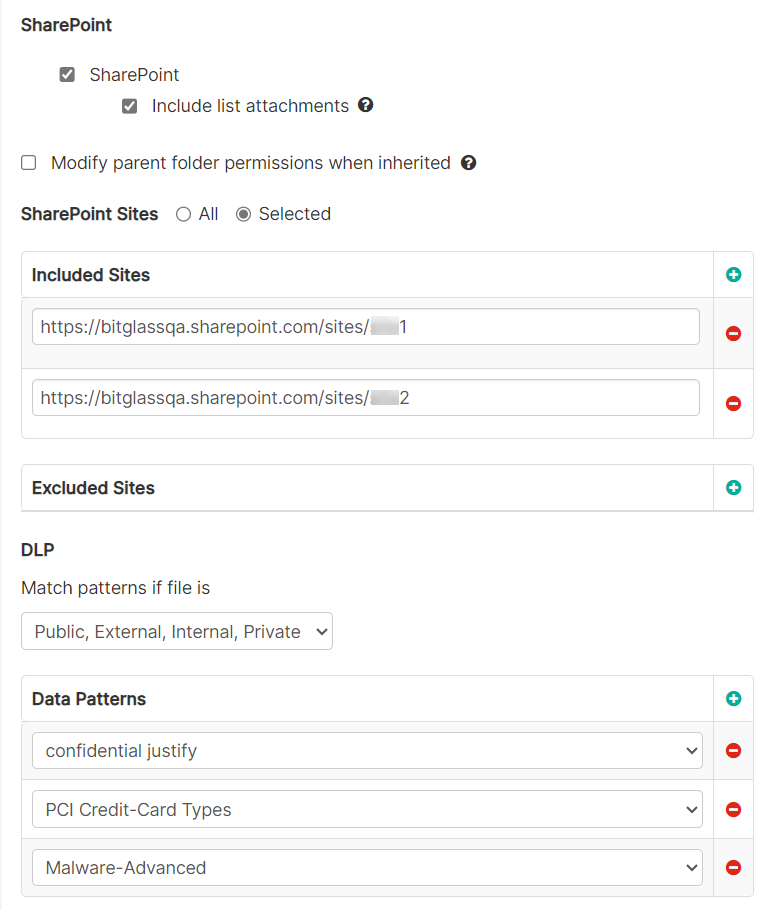
Sharepoint scan can detect and scan multiple root sites that are associated with a single M365 account. You an either select All or select Selected and then select the specific site(s) to enable the scan on multiple root sites and underlying subsets for a specific tenant.
- Select the Modify parent folder permissions when inherited checkbox to remove the share permissions of the parent folder if a file matches a remove sharing policy and the share is inherited from a parent folder. To understand the behavior of unshared file in different situations, refer to M365 Remove Sharing Behavior.
Note:OneDrive and Sharepoint files may be shared by Links Giving Access or Direct Access.
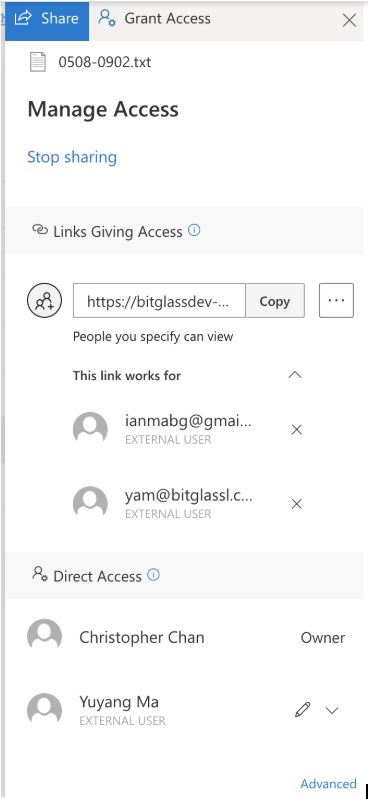
During DLP API scans, Microsoft 365 Graph API returns a definitive list of all direct shares. However, Graph API is not definitive with respect to link shares as follows:
- Limitation 1: When a file is shared by link with a specific set of users, Graph API does not return the list of users. As a result Forcepoint Data Security Cloud | SSE deems the file externally shared. We make a best effort to identify the list of recipients by scanning the logs of the file owner spanning a window of one hour.
- Limitation 2: When a user deletes a link share, Graph API does not notify that the file properties have changed. Therefore, API scan results will be out-of-date until the file is scanned again for other reasons.
- Check the box and then select one of the following options to enter the sites you want to include in the scans:
- You can configure scanning of Copilot by following these steps:

- Check the box to activate Copilot scanning for the selected sites.
- Choose user scan scope:
- All: Includes all users in the M365 tenant.
- Selected: Allows you to specify user groups to include.
- You can limit scanning to specific user groups:
- Included Groups: Only users in these groups will be scanned.
- Excluded Groups: Users in these groups will be excluded from scanning.
- You can limit scanning to specific user groups:
- Here you can add the DLP data patterns that you want to identify.Note: To configure API policies with the Forcepoint DLP data pattern, refer to Configuring FSM controlled policies for CASB and SWG channels.
M365 Remove Sharing Behavior
The behavior of remove sharing for file(s) with inherited permissions from parent folder stored in OneDrive and Sharepoint depends on the Modify parent folder permissions when inherited checkbox configuration as described below. Files with no inherited permissions are unaffected by this configuration checkbox. There are separate configuration checkboxes for OneDrive and Sharepoint.
- When Modify parent folder permissions when inherited is unchecked, then sharing permissions inherited from the parent folder are not removed. Only uninherited permissions are modified.
- When Modify parent folder permissions when inherited is checked, then sharing permissions that are inherited from parent folder will be attempted to be
removed as described below:
- For situations if a file is placed under nested folders:
For example, Folder A > Folder B > File X
When the removal of share permissions for file X is attempted, Forcepoint Data Security Cloud | SSE would not remove permissions for folder B since its permissions are inherited from its parent directory (Folder A). This behavior avoids inherited permission removal for other files that could be present under Folder A. In this scenario, file X permissions will not be modified.
- For situations with no nested inheritance:
For example, Folder A > File X
File X inherits permissions directly from those set only for Folder A, the requisite Folder A sharing permissions will be removed.
- For situations of multiple files under a same folder:
For example, Folder A > File X, File Y, and File Z
When the removal of permissions for file Y is attempted, Forcepoint Data Security Cloud | SSE removes permissions for Folder A, thereby removing permissions for Files X and Z.
- Inherited Permissions are only removed if relevant.
Forcepoint Data Security Cloud | SSE will not remove all inherited permissions and will only remove the permission targeted by the action.
For example, the Folder A is externally shared to test@example.com and File Z is publicly shared:- If you remove public sharing for file Z, then Forcepoint Data Security Cloud | SSE just removes the permission of file Z.
- If you remove external sharing for file Z, then Forcepoint Data Security Cloud | SSE removes the folder level permissions.
- For situations if a file is placed under nested folders:
When does inherited sharing removal generate logs?
- When folder level sharing is removed, then an API audit log is generated for that folder stating the permission (public/external/internal sharing) that was removed.
- Admin logs are generated when:
- Removal of file level sharing is not possible due to inherited permissions when the Modify parent folder permissions when inherited checkbox on the M365 API Setup page is not selected.
- Permissions for a folder cannot be removed due to inherited permissions being inherited from its parent folder (nested inheritance).