For customers with users deployed on Microsoft 365 as cloud only, users (without any Active Directory instances installed) will need to manually create the Immutable ID for the users
which is used as the Source Anchor that Microsoft uses to authenticate the user.
This unique ID will need to be attached to the user in the Microsoft 365 instance as well as within Forcepoint Data Security Cloud | SSE. This guide page will walk you through the steps in order to
setup SSO with Forcepoint Data Security Cloud | SSE in an Microsoft 365 cloud only
deployment.Note: You will not be able to set the users ObjectGUID if they are still in a federated domain. Ensure that you perform these steps before federating Microsoft 365 with
Forcepoint Data Security Cloud | SSE and make sure you unfederate if you are federated
to any other IdPs before performing this steps.
Steps
-
The majority of these steps will be performed inside of PowerShell. Make sure you are running the latest PowerShell and that you have installed/enabled the Microsoft
Azure Active Directory Module for Windows PowerShell (which include the Msol cmdlets). Refer to the Microsoft guide page for how to connect to Microsoft 365 Powershell for more
information.
-
Once installed the next step is to connect to your Microsoft 365 in PowerShell.
Use the connect-msol cmdlet. It will then prompt you to login, login with your Microsoft 365 admin account to connect.
-
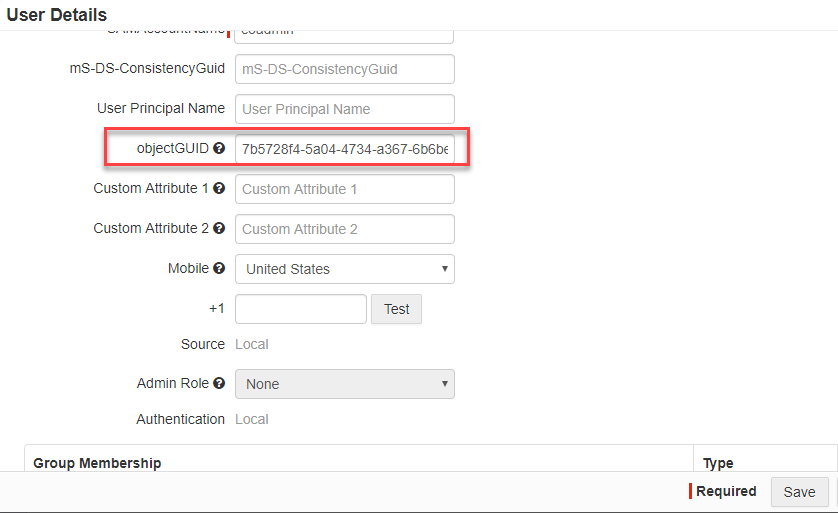
Now we can generate an ObjectGUID for the users which we will need to convert (base64) to an ImmutableID. You can create these unique IDs from a site such as https://www.guidgen.com/. It's best to create list to compile each user and their associated
ObjectGUID.
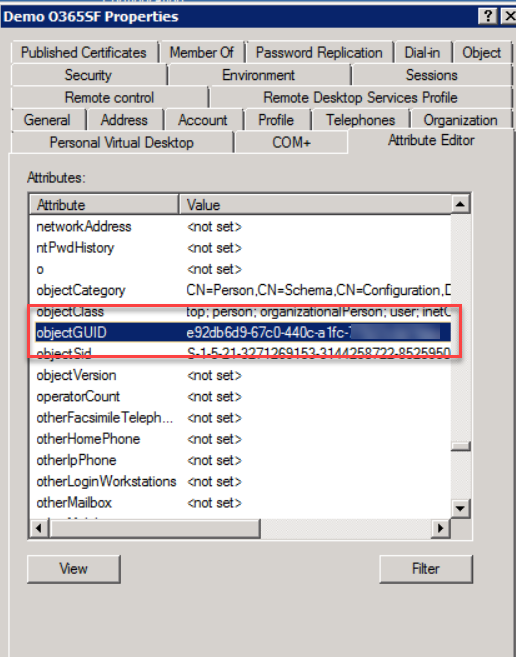
Note: For customers who have an Active Directory instance connected to their Microsoft 365 instance, but cannot setup the AD sync with
Forcepoint Data Security Cloud | SSE, you can locate the ObjectGUID within the users
"Attribute Editor" section in AD.
-
Now with the ObjectGUIDs in hand we will need to launch powershell to convert it to an ImmutableID.
First define a variable with the GUID you generated.
$oguid = 7b5728f4-5a04-4734-a367-6b6be0c7abd3
-
Run the following command to convert to Base64.
[system.convert]::ToBase64String(([GUID]($oguid)).tobytearray())
-
Copy the output and paste it to your list next to the user who you are performing these actions on.
In our example the output (which is the Immutable ID) is: 9ChXewRaNEejZ2tr4Mer0w==
-
Now we need to decode teh Base64 ImmutableID. Define a variable with the Base64 encoded ImmutableID.
$iid = "9ChXewRaNEejZ2tr4Mer0w=="
-
Set a variable that will transform the $iid variable back to GUID and echo the variable.
- $guid = [GUID]([system.convert]::FromBase64String($iid))
- $guid
-
Now we can update teh user record in Microsoft 365 with the ImmutableID.
Set-MsolUser -UserPrincipalName username@emaildomain.com -ImmutableId 9ChXewRaNEejZ2tr4Mer0w==
-
You can verify the user's ImmutableID has been set properly by piping the get-msoluser command with fl to show all of their attributes.
Get-MsolUser -UserPrincipalName username@emaildomain.com | fl
-
Finally go the Forcepoint Data Security Cloud | SSE admin portal under and find the users account, select it to edit it and add the ObjectGUID in the appropriate field.