Forcepoint Data Security Cloud | SSE supports auto remediation as well as automated email
alerts for a number of configuration settings.
To enable auto remediation, you must include the additional policy lines included in the note at the bottom of the Create Audit Policy Section above. When
viewing your AWS CSPM report, click on the third category Remediation.
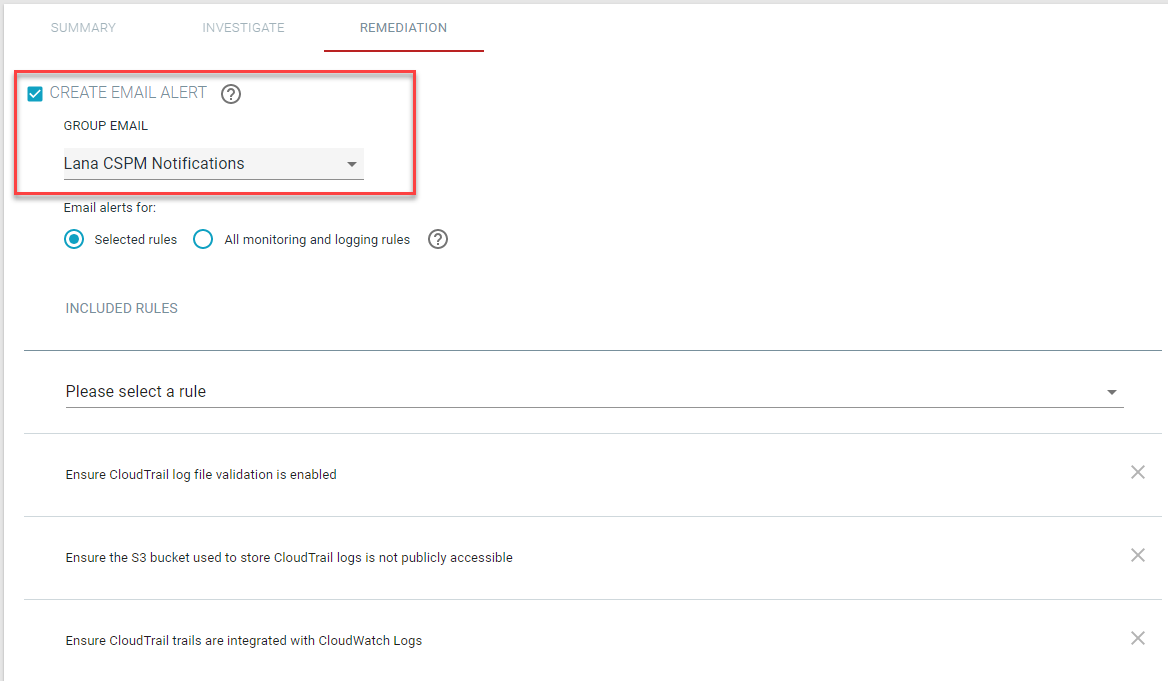
The top section will allow you to generate an automatic email notification when a configuration rule you selected is misconfigured. The message that is sent is configured on the
Notifications page. Forcepoint Data Security Cloud | SSE can
send alerts on the rules related to monitoring and logging within AWS.
Steps
-
Begin by selecting the checkbox to enable Create Email Alert and then select your email notification group from the drop-down that you would have created on
the page.
-
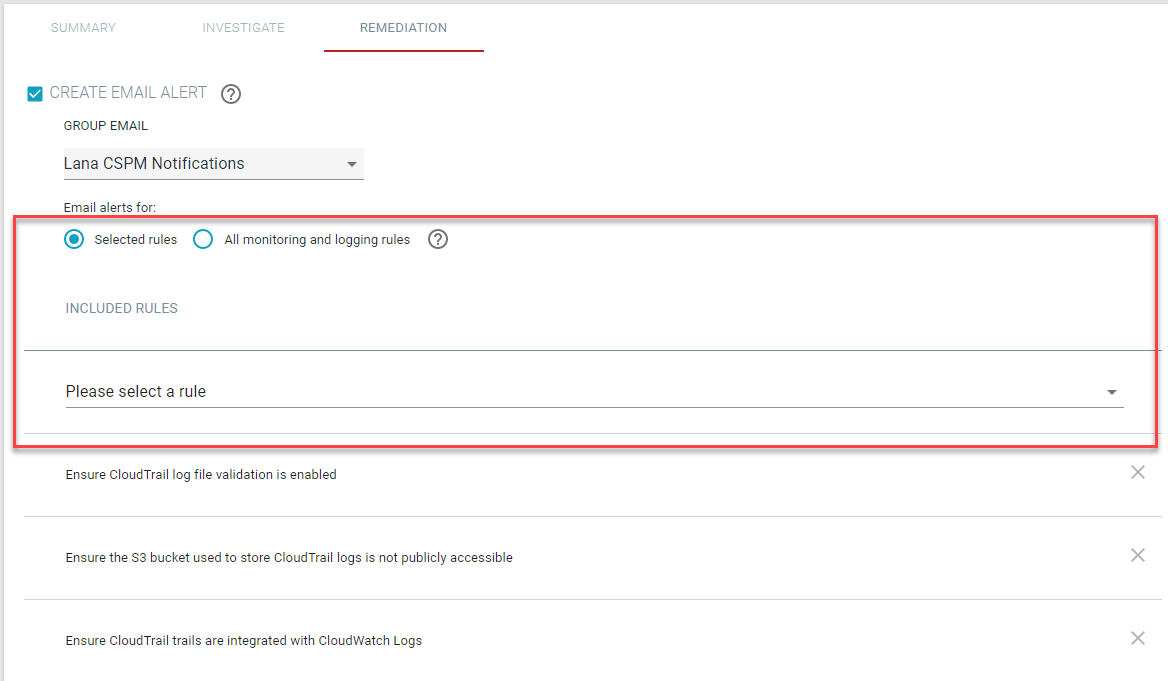
Next you can select which rules you want to send an email alert on, specific ones you choose or all monitoring/logging rules. If you choose specific ones you will then get a
drop-down where you can select the rule you wish to be alerted on. The bottom section will allow you to select which rules you wish to auto remediate.
-
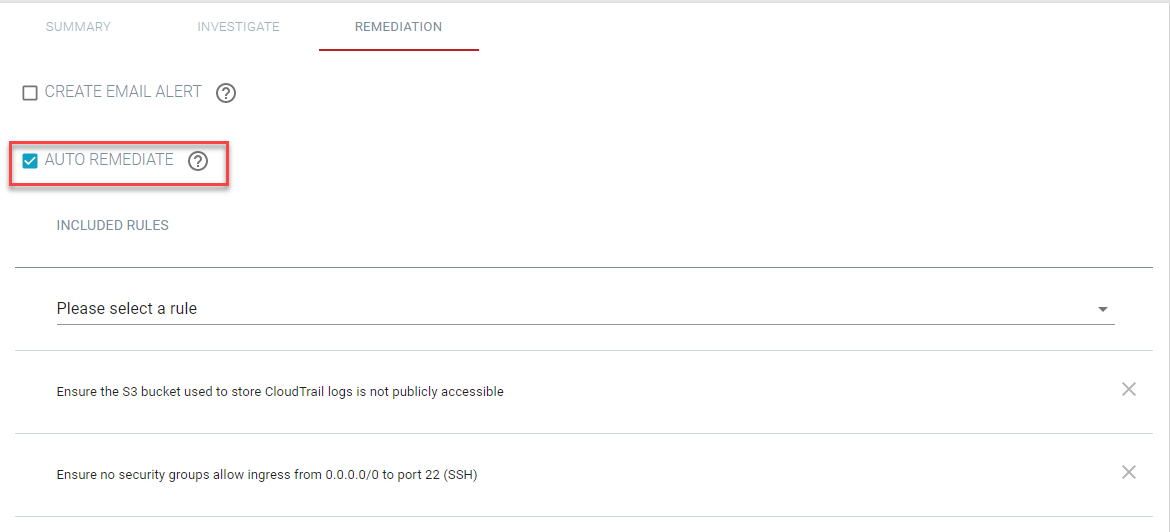
Begin by checking the box to enable auto remediate.
-
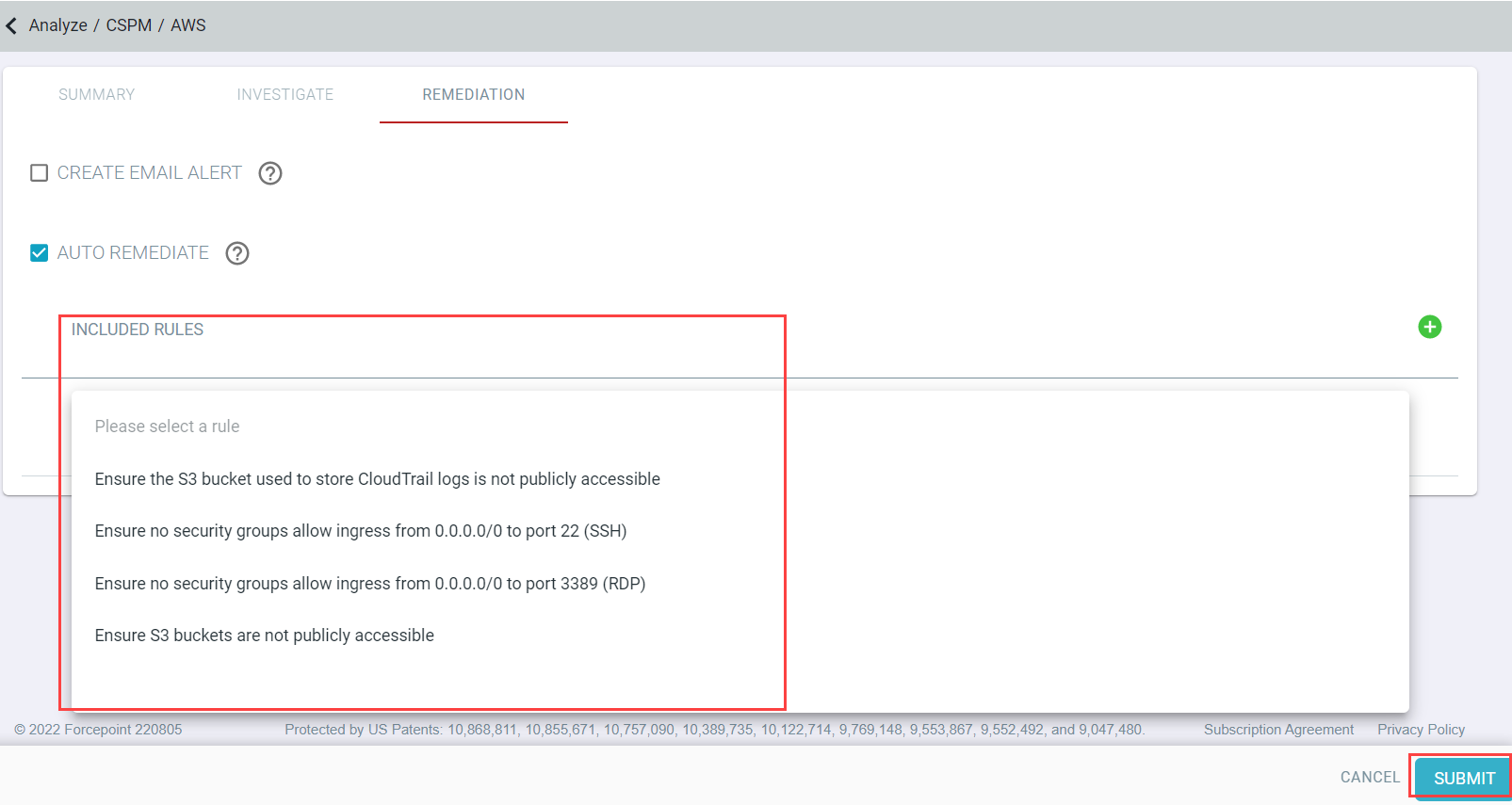
Now you can select the rules you wish to have auto remediated from the drop-down. Once you have selected the rules you can clickSubmit at the bottom.
Note:
The only rules available for auto remediation are rules that Forcepoint Data Security Cloud | SSE will have permission to change on your
behalf
- Ensure the S3 bucket used to store CloudTrail logs is not publicly accessible
- Ensure no security groups allow ingress from 0.0.0.0/0 to port 22 (SSH)
- Ensure S3 buckets are not publicly accessible
- Ensure no security groups allow ingress from 0.0.0.0/0 to port 3389 (RDP)