Creating audit policy in AWS
Make sure you have followed the steps on the Amazon S3: Configuring API access guide page to create the IAM user or STS token that you are using to connect Forcepoint Data Security Cloud | SSE to AWS via API.
Steps
-
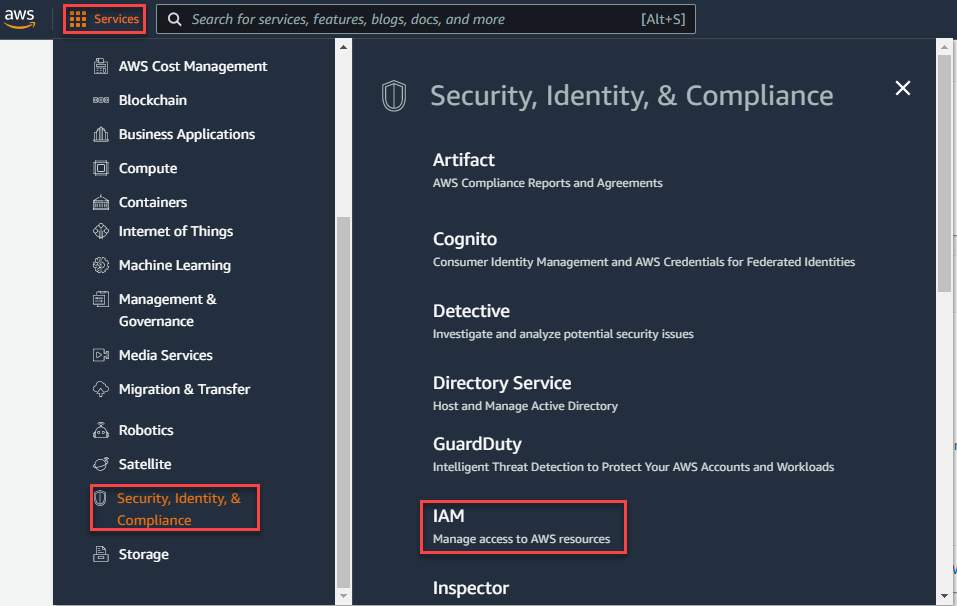
Login to the AWS console and navigate to Services > Security, Identity, & Compliance > IAM.
-
Select Policies from the left navigation pane under Access management and then click Create Policy to create a new policy.

-
On the JSON tab, paste the following permissions into the text field and then click Next: Tags at the bottom. You will likely need to
split the below permission into two separate policies.
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": [ "waf:ListWebACLs", "config:Get*", "iam:List*", "cloudtrail:GetTrailStatus", "storagegateway:DescribeGatewayInformation", "cloudfront:Get*", "logs:DescribeMetricFilters", "firehose:Describe*", "guardduty:List*", "codedeploy:List*", "batch:DescribeComputeEnvironments", "cloudwatch:Describe*", "config:Describe*", "kinesis:ListStreams", "serverlessrepo:GetApplicationPolicy", "elasticmapreduce:ListInstances", "datapipeline:EvaluateExpression", "storagegateway:List*", "iam:SimulateCustomPolicy", "ses:GetIdentityDkimAttributes", "rds:Describe*", "route53:Get*", "rds:DownloadDBLogFilePortion", "opsworks-cm:DescribeServers", "ssm:ListDocuments", "s3:GetBucket*", "kinesisanalytics:ListApplications", "codebuild:ListProjects", "cloudfront:List*", "config:Deliver*", "logs:DescribeDestinations", "snowball:ListJobs", "storagegateway:DescribeNFSFileShares", "waf-regional:ListWebACLs", "cloudtrail:LookupEvents", "cloudsearch:DescribeServiceAccessPolicies", "datapipeline:ListPipelines", "sns:ListSubscriptionsByTopic", "lambda:ListFunctions", "kms:Describe*", "codecommit:GetObjectIdentifier", "cloudhsm:ListLunaClients", "s3:GetReplicationConfiguration", "cloudtrail:DescribeTrails", "cloudformation:GetStackPolicy", "workspaces:Describe*", "iot:ListThings", "glacier:ListVaults", "iam:GenerateCredentialReport", "s3:GetLifecycleConfiguration", "tag:GetResources", "s3:GetInventoryConfiguration", "dynamodb:ListTables", "route53domains:ListTagsForDomain", "glacier:DescribeVault", "cognito-identity:ListIdentityPools", "sns:ListTopics", "datapipeline:ValidatePipelineDefinition", "route53domains:GetDomainDetail", "datapipeline:DescribePipelines", "gamelift:ListFleets", "iam:Get*", "route53domains:ListDomains", "storagegateway:DescribeWorkingStorage", "cloudsearch:DescribeDomains", "ses:ListIdentities", "sns:GetTopicAttributes", "ecs:Describe*", "datapipeline:QueryObjects", "guardduty:Get*", "codecommit:BatchGetRepositories", "elasticache:Describe*", "dynamodb:ListStreams", "iam:GetContextKeysForCustomPolicy", "ec2:Describe*", "directconnect:Describe*", "es:ListDomainNames", "codedeploy:Get*", "s3:ListAllMyBuckets", "rds:ListTagsForResource", "route53domains:ListOperations", "cloudtrail:ListPublicKeys", "codecommit:GetBranch", "storagegateway:DescribeUploadBuffer", "storagegateway:DescribeTapeArchives", "states:ListStateMachines", "kms:List*", "glacier:GetVaultAccessPolicy", "clouddirectory:ListDirectories", "kms:Get*", "firehose:List*", "storagegateway:DescribeCachediSCSIVolumes", "iot:DescribeEndpoint", "s3:GetObjectAcl", "iam:SimulatePrincipalPolicy", "codedeploy:Batch*", "codepipeline:ListPipelines", "cloudtrail:ListTags", "s3:GetObjectVersionAcl", "route53:List*", "events:ListRules", "elasticloadbalancing:Describe*", "gamelift:ListBuilds", "cloudformation:ListStack*", "iam:GetAccountAuthorizationDetails", "trustedadvisor:Describe*", "cloudhsm:ListHsms", "es:Describe*", "sdb:DomainMetadata", "cloudhsm:ListHapgs", "sqs:GetQueueAttributes", "ses:GetIdentityVerificationAttributes", "elasticbeanstalk:Describe*", "cognito-idp:ListUserPools", "storagegateway:DescribeBandwidthRateLimit", "route53domains:GetOperationDetail", "events:DescribeEventBus", "acm:DescribeCertificate", "organizations:Describe*", "codecommit:GetRepository", "redshift:Describe*", "storagegateway:DescribeCache", "cloudformation:GetTemplate", "storagegateway:DescribeVTLDevices", "storagegateway:DescribeTapes", "batch:DescribeJobDefinitions", "s3:GetAnalyticsConfiguration", "codecommit:List*", "organizations:List*", "mediastore:GetContainerPolicy", "serverlessrepo:ListApplications", "autoscaling:Describe*", "s3:GetAccelerateConfiguration", "lambda:GetAccountSettings", "cloudtrail:GetEventSelectors", "machinelearning:DescribeMLModels", "tag:GetTagKeys", "iam:GetContextKeysForPrincipalPolicy", "s3:GetEncryptionConfiguration", "snowball:ListClusters", "elasticmapreduce:ListClusters", "acm:ListCertificates", "ecr:DescribeRepositories", "s3:GetMetricsConfiguration", "elasticfilesystem:DescribeFileSystems", "ecs:List*", "logs:DescribeResourcePolicies", "storagegateway:DescribeTapeRecoveryPoints", "sqs:ListQueues", "storagegateway:DescribeMaintenanceStartTime", "application-autoscaling:Describe*", "logs:DescribeLogGroups", "mediastore:ListContainers", "datapipeline:DescribeObjects", "datapipeline:GetPipelineDefinition", "sdb:ListDomains", "storagegateway:DescribeStorediSCSIVolumes", "cloudformation:DescribeStack*", "storagegateway:DescribeSnapshotSchedule", "ssm:Describe*", "ds:DescribeDirectories", "elasticmapreduce:DescribeJobFlows", "lambda:GetPolicy", "ecr:GetRepositoryPolicy", "apigateway:GET", "appmesh:ListMeshes", "athena:BatchGetNamedQuery", "athena:ListNamedQueries", "backup:ListBackupVaults", "batch:DescribeJobQueues", "cloudfront:ListCloudFrontOriginAccessIdentities", "cloudsearch:DescribeDomains", "cloudsearch:ListDomainNames", "config:DescribeConfigurationRecorders", "datapipeline:ListPipelines", "directconnect:DescribeConnections", "ec2:DescribeFlowLogs", "ec2:DescribeInstances", "ec2:DescribeSecurityGroups", "ec2:DescribeVpcs", "ecr:DescribeRepositories", "ecs:ListClusters", "eks:ListClusters", "eks:DescribeCluster", "elasticbeanstalk:DescribeApplications", "elasticfilesystem:DescribeFileSystems", "elasticloadbalancing:DescribeLoadBalancers", "elasticmapreduce:ListClusters", "es:DescribeElasticsearchDomains", "es:ListDomainNames", "fsx:DescribeFileSystems", "glacier:ListVaults", "glue:GetCrawlers", "iam:GenerateCredentialReport", "iam:GetAccountPasswordPolicy", "iam:GetCredentialReport", "iam:GetGroup", "iam:GetGroupPolicy", "iam:GetPolicy", "iam:GetRole", "iam:GetUser", "iam:GetUserPolicy", "iam:ListAttachedGroupPolicies", "iam:ListAttachedRolePolicies", "iam:ListAttachedUserPolicies", "iam:ListGroups", "iam:ListGroupPolicies", "iam:ListPolicies", "iam:ListRoles", "iam:ListSAMLProviders", "iam:ListUsers", "iam:ListUserPolicies", "iam:ListVirtualMFADevices", "kinesis:DescribeStream", "kinesis:ListStreams", "kms:DescribeCustomKeyStores", "kms:DescribeKey", "kms:GetKeyRotationStatus", "kms:ListKeys", "lakeformation:ListResources", "lambda:ListFunctions", "lightsail:GetInstances", "route53:ListHostedZones", "rds:DescribeDBInstances", "s3:GetBucketAcl", "s3:GetBucketLocation", "s3:GetBucketLogging", "s3:GetBucketPolicy", "s3:ListAllMyBuckets", "s3:ListBucket", "serverlessrepo:ListApplications", "storagegateway:ListGateways" ], "Resource": "*" } ] }
Note:If you wish to allow for Forcepoint Data Security Cloud | SSE auto remediation for the policies that are supported, you will need to add the following policy lines to the above JSON script: The first two will cover policies for ensuring CloudTrail logs and the S3 bucket are not publicly accessible:
- s3:PutBucketAcl
- s3:PutBucketPolicy
The following policy line will cover policies for ensuring no security groups allow ingress to ports 22 (SSH) or 3389 (RDP):
- ec2:RevokeSecurityGroupIngress
-
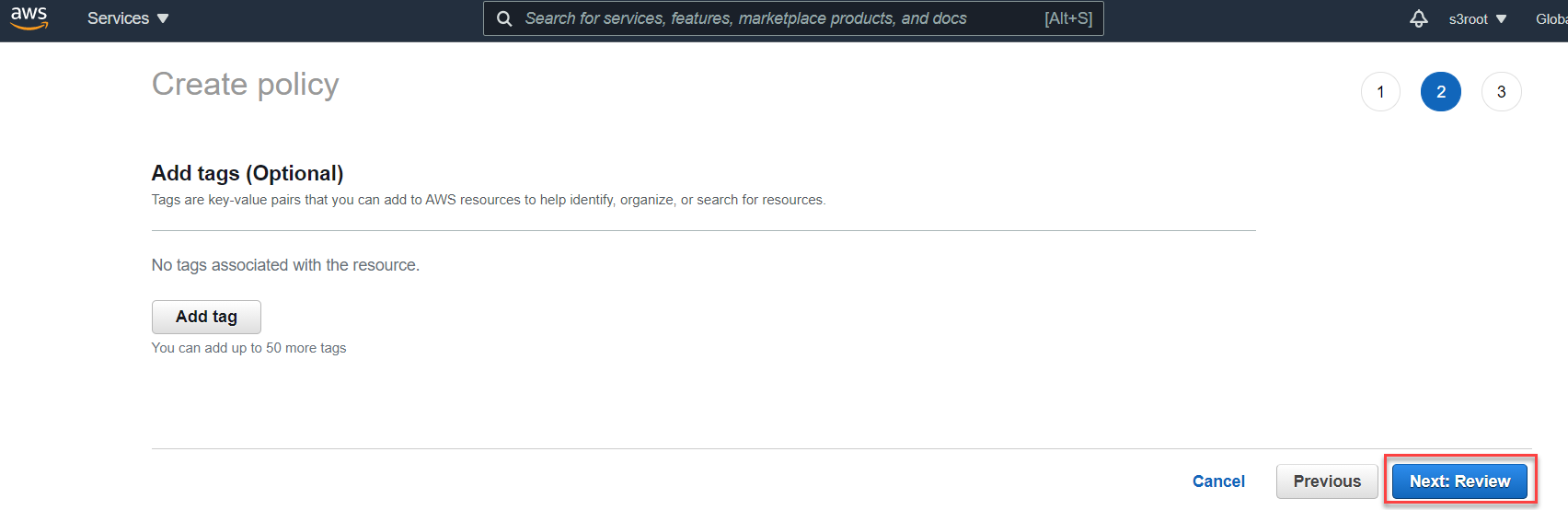
You can add tags to your policy here, otherwise click Next: Review at the bottom to proceed. On the next page, enter a name and description to your policy
and then scroll down to the bottom and click Create Policy. It's recommended you name it something clear and concise and provide a description of what the
policy is doing.
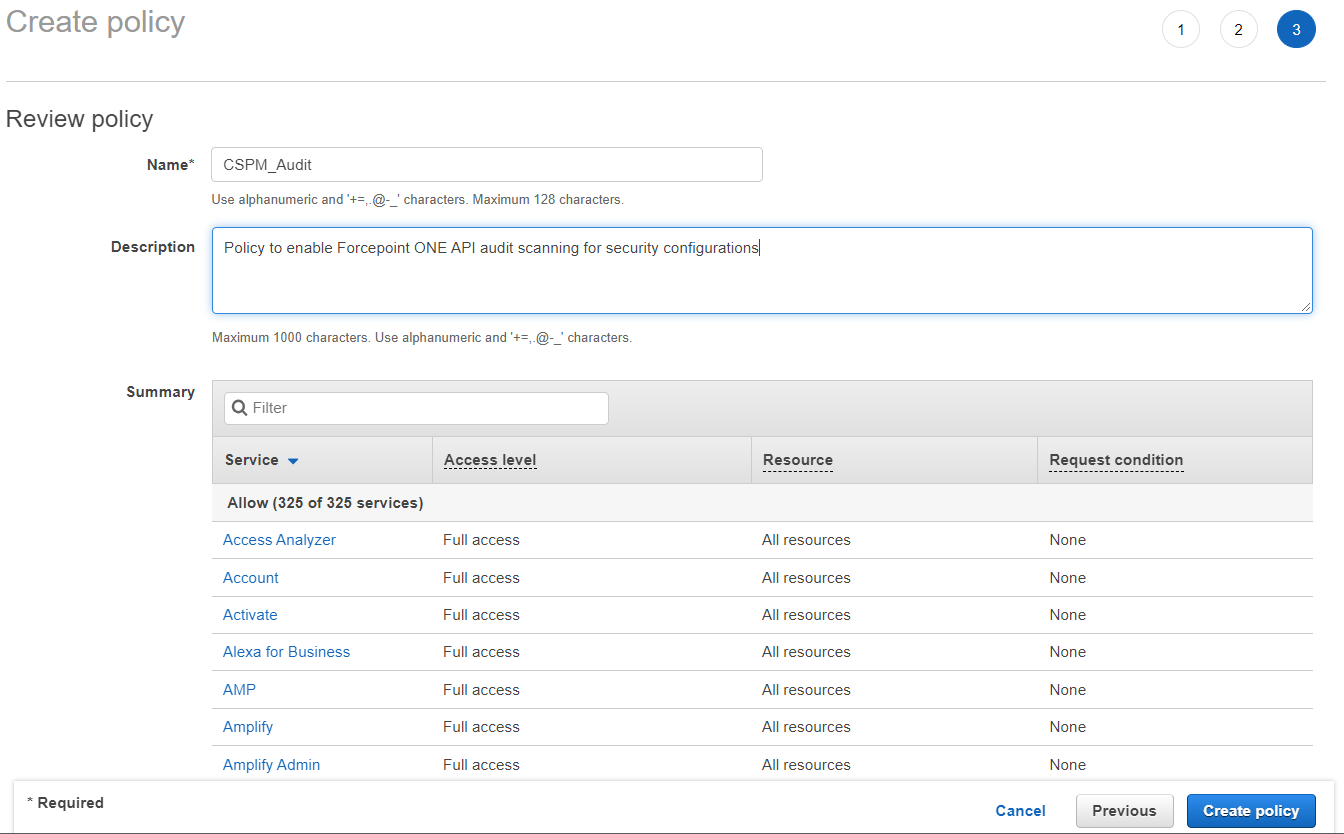 Now you can assign the policy to the IAM User or STS token that you have created or are using for the API connection. Once you are done, move on to the next section to enable auditing inside the Forcepoint Data Security Cloud | SSE.
Now you can assign the policy to the IAM User or STS token that you have created or are using for the API connection. Once you are done, move on to the next section to enable auditing inside the Forcepoint Data Security Cloud | SSE.