Device Profiling Proxy
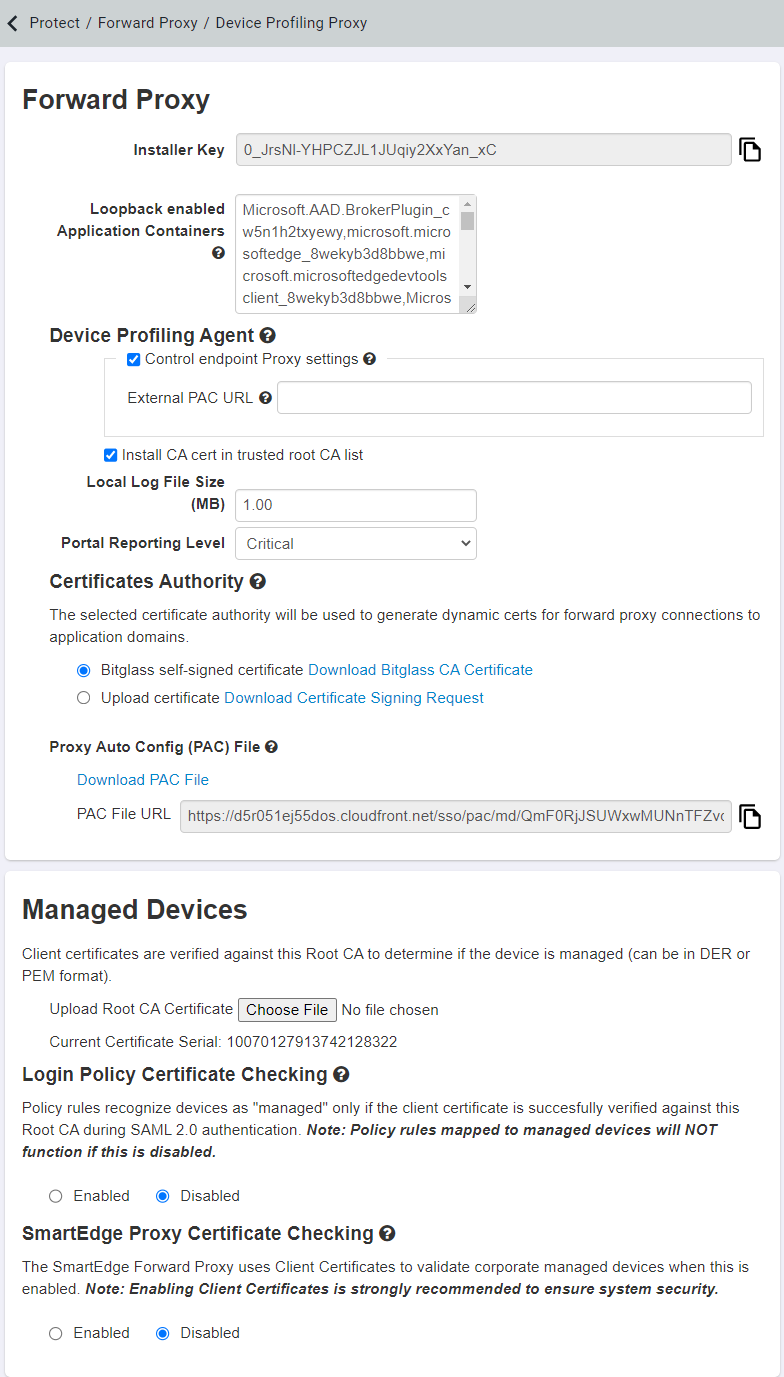
The Device Profiling Proxy page will allow you to both configure the means to distinguish between a managed and an unmanaged device as well as implement a forward proxy deployment for applying inline policy actions.
Device identification can be performed in 2 distinct ways: The first is to install a discreet Device Profiling Agent on the managed device that allows Forcepoint Data Security Cloud | SSE to identify it based on configured profiles in the Forcepoint Data Security Cloud | SSE portal. The other method is to install client certificates on the device that are checked against a Root CA certificate that you upload into the Forcepoint Data Security Cloud | SSE portal. Once a method has been chosen to identify managed devices, you can then configure policies to grant greater access to managed devices while restricting or limiting access to unmanaged devices. To learn more about how to configure the managed devices and policies, refer to Configuring managed device identification.
This page will also allow you to configure a forward proxy deployment for managed devices. Forward proxy deployments are good for proxying traffic to managed applications without URL rewriting. This is helpful for businesses that use SaaS applications with 3rd party extensions or 3rd party connections. A forward proxy deployment also supports controlling ShadowIT unsanctioned applications allowing admins to prevent possible data leakage to applications they do not directly manage or maintain.