Forward Proxy Device Profiling Agent
The Forward Proxy Device Profiling Agent can be installed on Windows or Mac machines for a few different functions.
- The Device Profiling Agent can be used to identify whether a machine is managed or not by profiling the machine for attributes defined in the Device Profile objects
section on the page.
- To learn more about how to create and manage device profiles, refer to Configuring device profiles.
- To learn how to deploy the Forward Proxy Agent to distinguish managed device, refer to Configuring managed device identification.
- The Device Profiling Agent can be used as a full forward proxy allowing admins to control access to unmanaged (ShadowIT, unsanctioned, etc) applications as well as
a proxy for your applications protected by Forcepoint Data Security Cloud | SSE when policies are configured for secure web access. Note: The forward proxy agent will proxy traffic to managed applications protected by Forcepoint Data Security Cloud | SSE without doing a URL rewrite. This means that if you have a policy configured for secure web access and the user has the forward proxy agent installed, they will not need to go through our reverse proxy and have the URL's rewritten. Instead the user will be forward proxied by the agent allowing for DLP policies and other controls to be applied as normal.
Inventory
Once a the device profiling agent has been installed, it will send a ping to the Forcepoint Data Security Cloud servers and populate information about that device under .
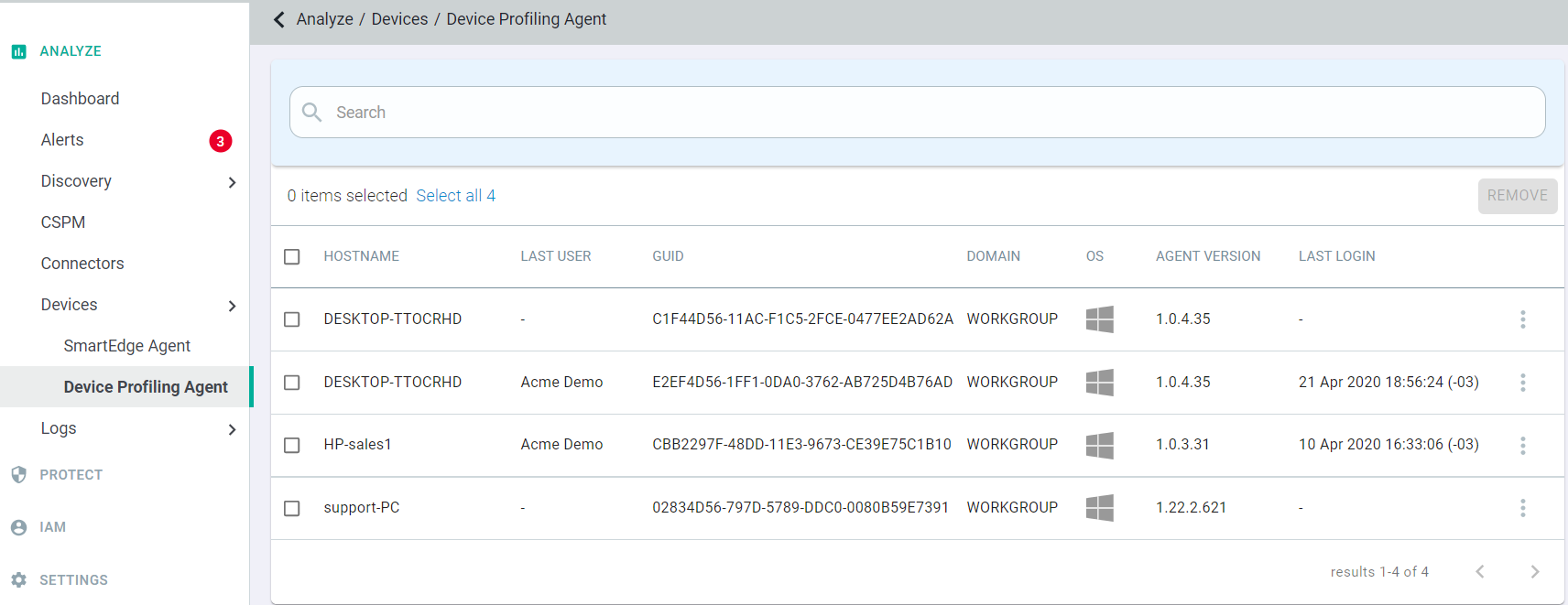
However, the device will not be attached to a user until that user logs into a cloud application forcing authentication via the agent. Once done, the device will also appear under the users User/Device History page.
Settings
- Control Endpoint Proxy Settings checkbox
- Should be checked, unless managed machines are already configured for forward proxy from another vendor (e.g. Bluecoat, Zscalar)
- Contact your Sales/SE team for how to proceed whenever this settings is unchecked
- Should be checked, unless managed machines are already configured for forward proxy from another vendor (e.g. Bluecoat, Zscalar)
- Install CA cert in trusted root CA list checkbox
- Should be checked unless the managed device already has a customer specific root CA installed. Make sure to upload an intermediate CA cert signed by the root CA in the certificates section so the Forcepoint Data Security Cloud | SSE can forward proxy the protected applications (e.g. Google App, Office 365, Box)
- Local Log File Size (MB) setting
- Default DPA log file size which is auto-rotated and can be used for debugging purpose
- When the DPA is put into debug mode the size automatically increases to 10MB
- Recommend default of 1MB
- Default DPA log file size which is auto-rotated and can be used for debugging purpose
- Portal Reporting Level dropdown
- Forwarded DPA logs will be visible on the page and will be tagged with Endpoint in the logs activity column.
- Options include Critical and Error related messages
- Setting the option to Error will forward error and higher level logs (e.g. Critical) Note: The DPA logs at the Info and above level on each endpoint into a local log file for more default verbosity than what is forwarded to the Forcepoint Data Security Cloud | SSE cloud. Forcepoint Data Security Cloud | SSE support may put the DPA into a debug mode to log at a higher verbosity in order to assist a customer's user that is having agent related difficulties.
- Certificates
- Setting the option to Error will forward error and higher level logs (e.g. Critical)
Windows Loopback Exceptions
Universal Windows Platform (UWP) apps often times run inside of a container and as such are not allowed to make connections to other local running processes and thus do not allow the Forward Proxy Device Profiling Agent to forward proxy the traffic from the applications. These applications can include commonly used applications such as Outlook 2016. In order to avoid this, admins must configure a loopback exception inside of the Forcepoint Data Security Cloud | SSE portal on the Endpoints page where you download the Device Profiling Agent and configure it's settings. To learn more about UWP apps, refer to the Microsoft guide page here.
- Login to the Forcepoint Data Security Cloud | SSE portal as an admin and navigate to , you will see a text field box titled Loopback enabled Application Containers under the Forward Proxy section.
- In this text field, you will need to enter the Windows store application/package names of the applications you wish to forward proxy for protection.
These names can be found in the C:\windows\SystemApps and C:\program files\WindowsApps folder. For further information
and reference, refer to the Microsoft guide page on UWP loopback.
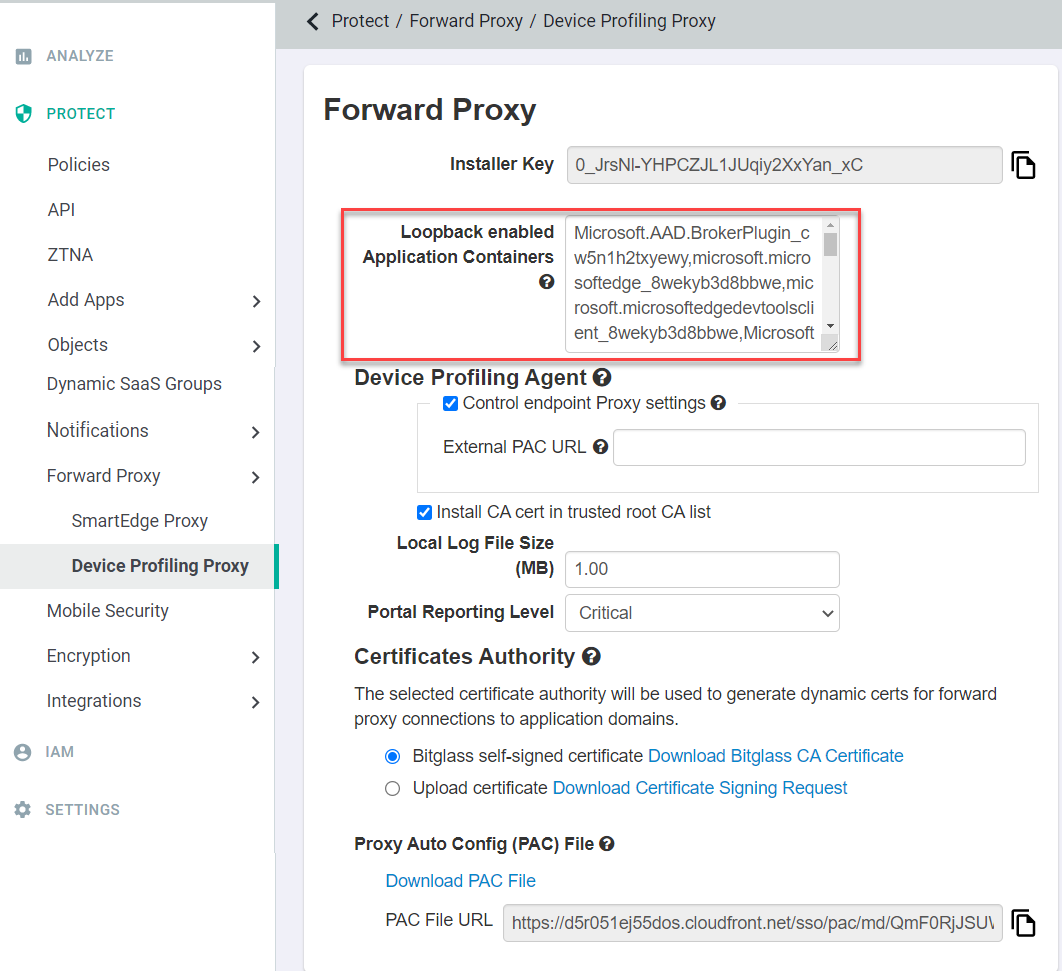
- Once you are done, save your changes. This will disable the loopback restriction that prevents the application from communicating with the Forward Proxy Device Profiling Agent thus allowing Forcepoint Data Security Cloud | SSE to forward proxy the traffic.
Certificates
The Forcepoint Data Security Cloud | SSE forward-proxy uses a CA certificate to generate app domain specific certificates necessary to inspect and protect client app traffic. Two options exist to control which CA certificate is used:
- Forcepoint Data Security Cloud | SSE self-signed certificate
- Default option for ease-of-use when testing the behavior (e.g. during a Forcepoint Data Security Cloud | SSE trial)
- Upload certificate - Customer specific forward-proxy certificate
- Recommended for production deployments requiring inspection of client app traffic
- Refer to the Policy section below which describes configuring application policy rules with Access Method set to SSO Auth and Action set to Secure App Access.
- Configuration steps
- Click the Download Certificate Signing Request link to download a CSR.
- Provide the CSR to your internal PKI certificate management team or use a public CA to generate an associated intermediate CA
certificate public key. Note: The intermediate CAs private key remains in the Forcepoint Data Security Cloud cloud, is encrypted, never shared with their Forcepoint Data Security Cloud | SSE tenants, and never exposed outside Forcepoint Data Security Cloud | SSE’s cloud infrastructure.
- Upload certificate
- The certs must be in a single file with the full chain of root CAs and any intermediate CAs public key down to the generated intermediate CA in PKCS#7 format. Once uploaded, the root CA certificate is automatically installed on endpoint machines in the trusted root CA list when the Install CA cert in trusted root CA list checkbox is enabled.
- Recommended for production deployments requiring inspection of client app traffic