Creating a conditional access policy
You need to configure a conditional access policy to restrict users from directly accessing Microsoft 365 applications.
Steps
- If you are not already in Azure, sign into the Azure Portal with an Azure administrator account.
- Navigate to Microsoft Entra ID > Security > Conditional Access.
-
Click Create new policy.
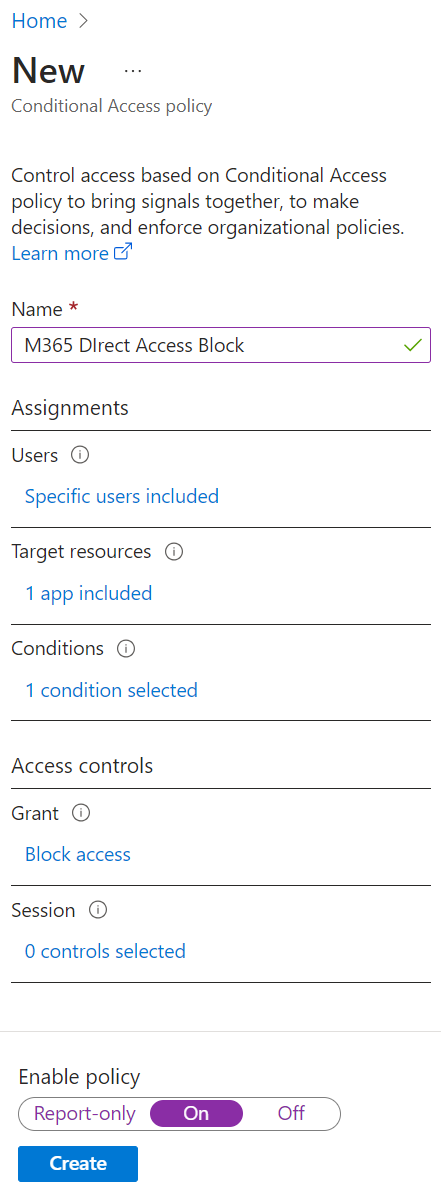
- On the New Conditional Access policy page, enter a Name for the policy.
-
Under Assignments, select the Users and groups to be blocked from direct access.
- Click Users.
- On the Include tab, select the Select users and groups option.
- Check the Users and groups checkbox and then select at least one user or group to be blocked. Ensure to exclude Admin user.
-
Under Assignments, select the Target resources to be blocked. The Microsoft cloud applications you select here will be blocked from
direct access.
- Click Target resources.
- Select Cloud apps from the Select what this policy applies to drop-down.
- Under Include, select Select apps to choose specific Microsoft cloud applications, such as Office 365, Outlook, or Teams to block. Choose all applications you wish to restrict direct access to.
-
Under Assignments, add a condition to exclude the Forcepoint Data Security Cloud | SSE IP ranges:
- Click Conditions.
- Click Locations.
- Under Configure, click Yes.
- Under Exclude, select the named location you created.
-
Under Access controls, click Grant and then select Block access.
This will block access to all locations, except for the excluded named locations selected above.
- Under Enable policy, click On.
-
Click Create.
Once you have created conditional access policy, you may need to wait around 15 minutes to allow policy sync across the internet. Based on the conditional access policy you created, direct access to Microsoft 365 applications is restricted.