Policies
Policies enable monitoring and control of the flow of sensitive data throughout an organization. Administrators can set up policies to monitor information and ensure all communications are in line with applicable regulations and compliance laws.
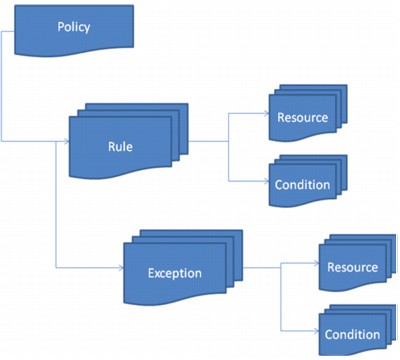
Policies contain rules, and rules can be associated with one or more exceptions. Rules and Exceptions describe the data we want to protect, the source and destination, and the action to take if the rule or exception is matched. Classifiers are used to identify the data. Multiple Classifiers can be grouped using Boolean expressions. Resources are used to identify the source, destination, and action to apply. Exceptions are only evaluated when their parent rules are matched. In this case if an exception matches after its parent rule has matched, then the exception action will be taken.
These components are the building blocks of a policy.
Forcepoint Data Security Cloud | DLP comes with a rich set of predefined policies that cover the data requirements for a wide variety of organizations and regions. Administrators can choose to use the predefined policies as needed, refine the predefined policies to meet specific needs, or define a policy from scratch.
| Element | Description |
|---|---|
| Rules | Provide the logic for the policy. These are the conditions that govern the behavior of the policy. When should something be blocked? Rules can apply to a single breach or to the accumulation of breaches over a period (drip DLP). Standard rules create incidents every time a rule is matched. Cumulative rules accumulate matches over time and create incidents when a threshold is met. |
| Exceptions | Define the conditions that should be exempt from the rules. An exception is part of a rule and checked only when its rule is triggered. You cannot add exceptions to cumulative rules, and exceptions themselves cannot be cumulative. |
| Classifiers | Describe the data to be protected. You can classify data by patterns and phrases, file labeling, or file properties. |
| Resources | Describe the source and destination of the data you want to protect, the endpoint device or application that may be in use, and the action to take when a violation is discovered. |