Step10: Configure DLP policies for cloud applications in the Forcepoint Data Security Cloud | SSE
Describes how to configure DLP policies in Forcepoint Data Security Cloud | SSE.
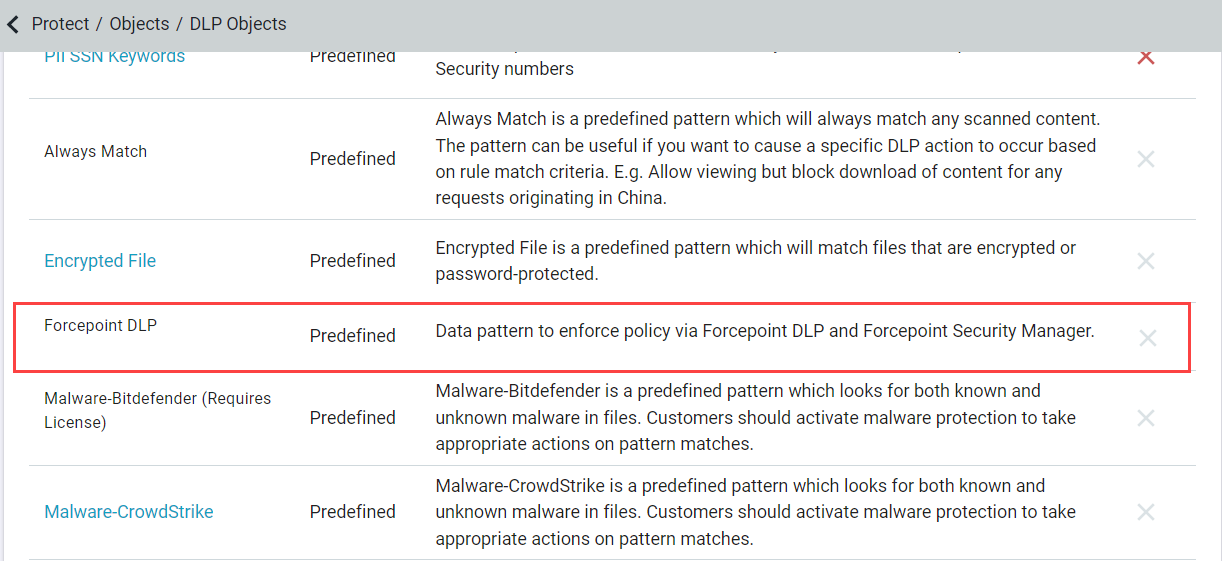
A new predefined data pattern named Forcepoint DLP is available under page once a valid DPS license is uploaded to Forcepoint Data Security Cloud | SSE.
After uploading and validating DPS license in Forcepoint Data Security Cloud | SSE, you can now use Forcepoint DLP data pattern in Secure App Access policy action modals as a Data pattern in all your CASB policies.
Forcepoint DLP Data Pattern in CASB Policies
After uploading and validating JSON license file, you can use the Forcepoint DLP data pattern while configuring CASB policies. Refer to Configuring contextual access control and Configuring proxy policy actions to create or edit existing policy.
While creating CASB policies, if you select Forcepoint DLP as the data pattern in any of the Actions dialog for Secure App Access, then:
- The FSM Enforced option gets populated in Action field as the action is configured on the FSM. The FSM Enforced is the only
option available for selection.
If an action other than Allow that is not supported by the application is returned when using Forcepoint DLP data pattern, Forcepoint Data Security Cloud | SSE translates it as a Deny.
To send notifications when the Forcepoint DLP returns an action other than Allow, click Notify.
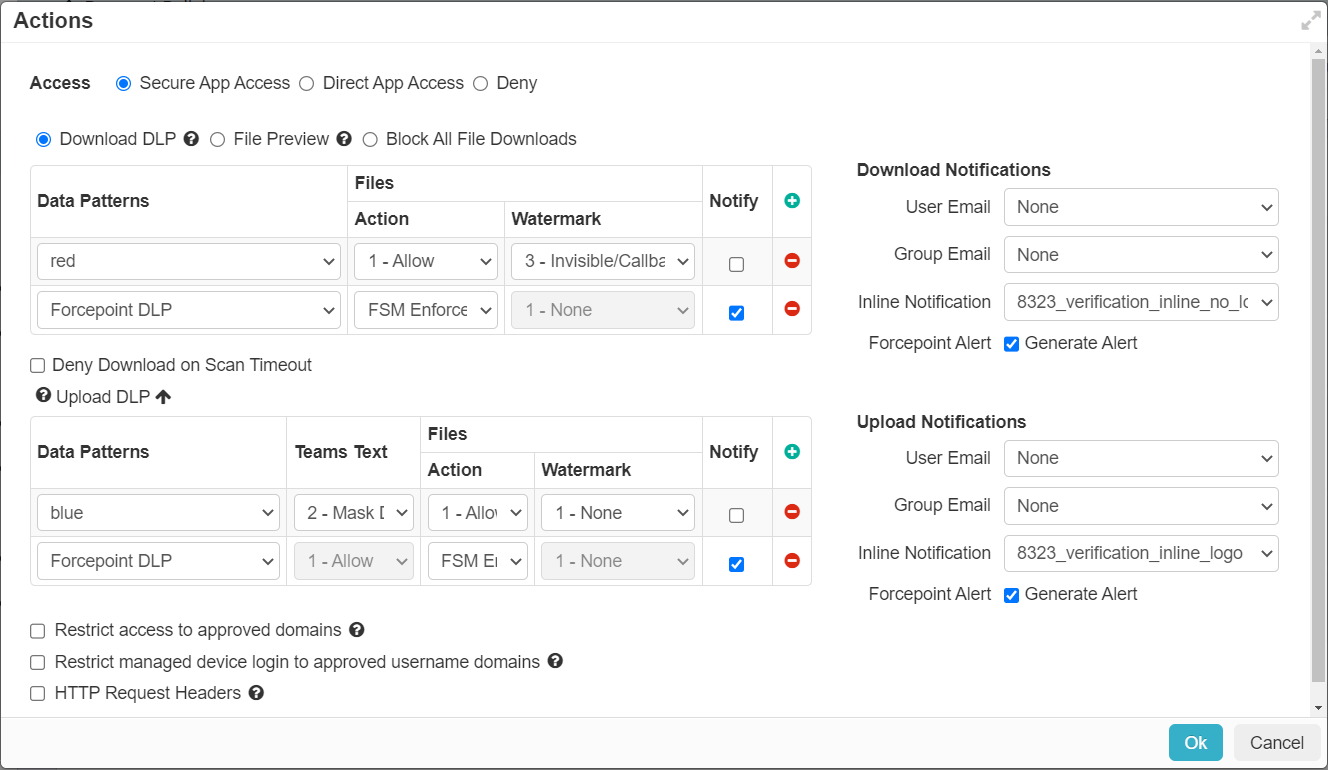
- All other fields in the upload or download DLP table are set to their default value and greyed out and are not supported with Forcepoint DLP.
While configuring the CASB Inline policy, you can select only Anti-malware data patterns that you have purchased as part of Forcepoint Data Security Cloud | SSE subscription along with the Forcepoint DLP data pattern. None of the other Forcepoint Data Security Cloud | SSE data patterns available in the page are supported with the Forcepoint DLP data pattern.
For all the FSM-based policies, Forcepoint Data Security Cloud | SSE executes the action returned by Forcepoint DLP.
If an action is returned by both the FSM-based policy (with Forcepoint DLP data pattern) and another CASB Inline policy (with Anti-malware data pattern) in Forcepoint Data Security Cloud | SSE, the most severe action is enforced. The Deny action is the most severe and the Allow action is the least severe.
Using FSM-based policy with Forcepoint Data Security Cloud | SSE' CASB Inline policy with Anti-malware data pattern together might result in FSM incidents displaying incorrect action details. To determine the actual action implemented, refer to the Forcepoint Data Security Cloud | SSE's Reviewing Proxy logs.
Forcepoint DLP Data Pattern in API Setup
After uploading and validating DPS license, you can select the Forcepoint DLP data pattern from the Data Patterns section while configuring API scanning of files for any of the following supported applications. To enable API scanning for cloud applications, refer to Protecting data at rest.
- Microsoft 365
- Google Workspace
- Salesforce
- ServiceNow
- Box
- Dropbox
- AWS S3
- Cisco Webex
Forcepoint DLP currently supports scanning of File objects for API Scanning.
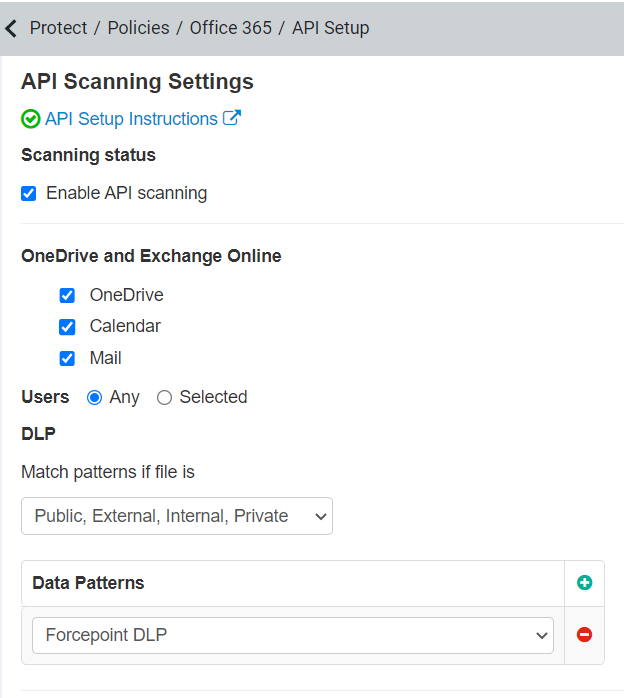
While configuring the application, you can select only Anti-malware data patterns that you have purchased as part of Forcepoint Data Security Cloud | SSE subscription along with the Forcepoint DLP data pattern. You can find the Anti-malware data patterns in the page.
For all the FSM-based policies, Forcepoint Data Security Cloud | SSE executes the action returned by Forcepoint DLP.
Forcepoint Data Security Cloud | SSE recommends you to create the following API policies if alerts and Policy ID in API Audit logs are needed for FSM-based policy:
- A policy with Anti-malware data pattern with any actions and alerting
- Another policy with the Forcepoint DLP data pattern set to Allow action placed at bottom of all configured policies
If an action is returned by both the FSM-based policy (with Forcepoint DLP data pattern) and another API policy (with Anti-malware data pattern) in Forcepoint Data Security Cloud | SSE, the most severe action is enforced. The actions are prioritized from most severe to least severe, with the most severe at the top of the list:
- Quarantine
- Remove All Sharing
- Remove Public+External Sharing
- Remove Public Sharing
- Encrypt
- CreateCopy
- Allow/Alert
For more information about the supported DPS actions for each application, see the API Support page.
Using FSM-based policy with Forcepoint Data Security Cloud | SSE API policy together might result in FSM incidents displaying incorrect action details. To determine the actual action implemented, refer to the Forcepoint Data Security Cloud | SSE API logs.