Multiple Node Installation (High Availability)
This section describes steps for installing a multi-node cluster via the Airgap installation Method.
Prerequisites
| Protocol | Port | Description |
|---|---|---|
| TCP | 6443 | Kubernetes API Server |
| UDP | 8472 | Required for Flannel VXLAN |
| TCP | 2379-2380 | embedded etcd |
| TCP | 10250 | metrics-server for HPA |
| TCP | 9796 | Prometheus node exporter |
| TCP | 80 | Private Docker Registry |
- Domain Name Service (DNS) configured
- Network Time Protocol (NTP) configured
- Fixed private IPv4 address
- Globally unique node name (use
--node-namewhen installing K3s in a VM to set a static node name)
Firewall Rules for External Communication
| Protocol | Port | Description |
|---|---|---|
| TCP | 443 | FDC backend |
The user must not access the K3s nodes directly, instead, there should be a load balancer sitting between the end user and all the K3s nodes (master and worker nodes):
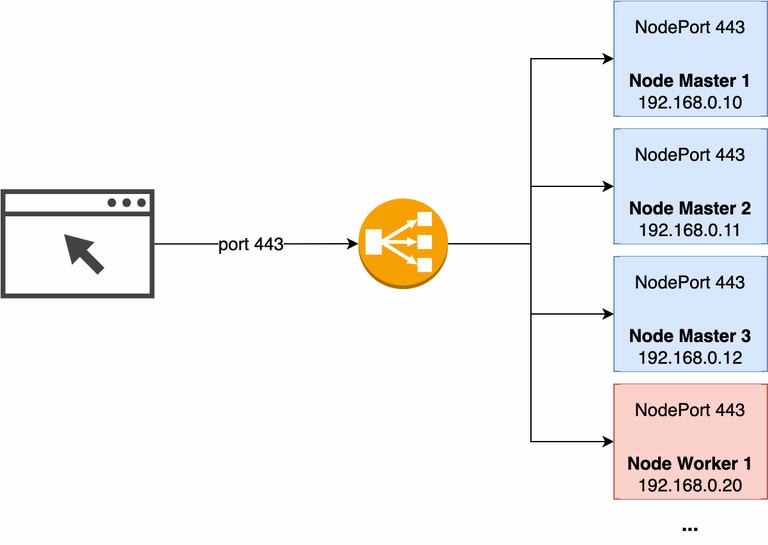
The load balancer must operate at Layer 4 of the OSI model and listen for connections on port 443. After the load balancer receives a connection request, it selects a target from the target group (which can be any of the master or worker nodes in the cluster) and then attempts to open a TCP connection to the selected target (node) on port 443.
The load balancer must have health checks enabled which are used to monitor the health of the registered targets (nodes in the cluster) so that the load balancer can send requests to healthy nodes only.
- Timeout: 10 seconds
- Healthy threshold: 3 consecutive health check successes
- Unhealthy threshold: 3 consecutive health check failures
- Interval: 30 seconds
- Balance mode: round-robin
VM Count
At least 4 machines are required to provide high availability of the Forcepoint platform. The HA setup supports a single-node failure.