Configuring an LDAP/LDAPS profile for an agent-based approach
Integrate Active Directory either through an LDAP or LDAPS connection via agent.
Steps
- Sign in to Forcepoint Data Security Cloud.
- From the application waffle, select Admin.
-
From the left Navigation Pane, click the LDAP
 icon.
icon.
The following page opens displaying existing LDAPs.
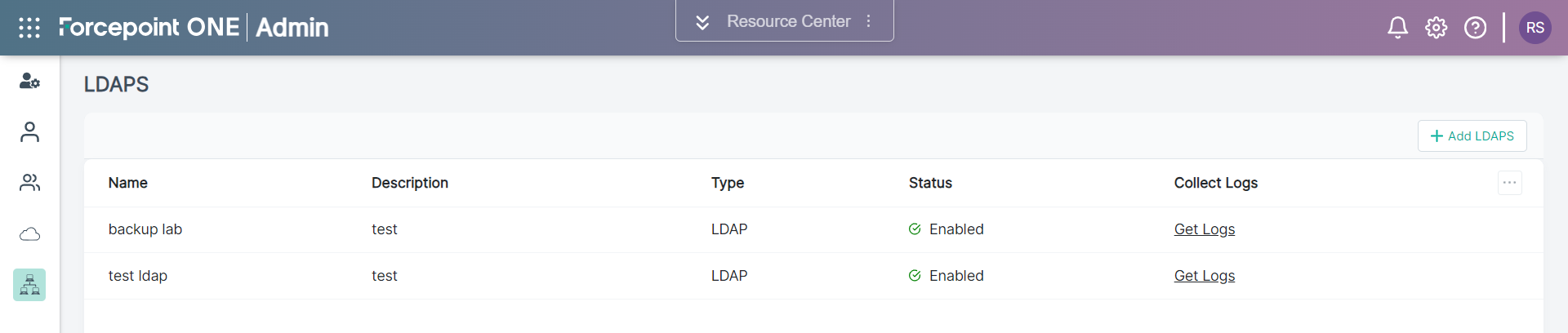
-
To add a new LDAPS, click +Add LDAPS.
The Add LDAPS opens on the right pane.
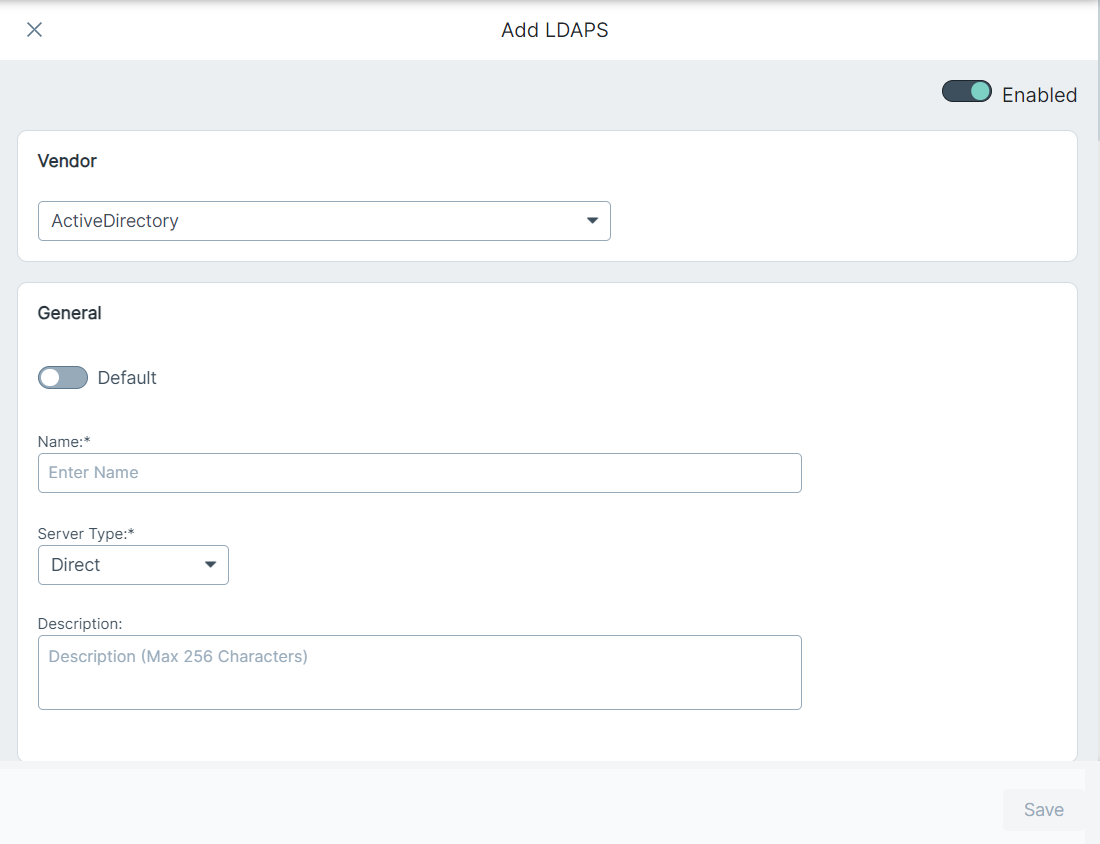
- Click the toggle switch to enable the LDAP or LDAPS configuration.
-
From the Vendor drop-down, select the applicable vendor for which you want to create LDAP or LDAPS.
By default, ActiveDirectory is selected.
-
Under the General section, enter values for the following fields:
Parameter Description Default Toggle switch to make configuration as default one. Name Enter the name of configuration Server Type Select the server type: - Direct - Select this option to configure LDAP or LDAPS via an agentless approach.
- Agent - Select this option to configure LDAP or LDAPS using AD agent.
Description Brief description on the configuration -
Under the Server Settings, enter values for the following fields:
Parameter Values Description Bind DN For example: cn=Administrator, cn=Users, DC=pnq, DC=aps Required parameter. The usernames that will be used for searching and requesting authentication. Bind Password Password used by the LDAP user specified in the Bind DN. Connection URL For example: ldaps://domain.pnq.aps Required parameter. The hostname or IP address of the Active Directory server. Note: LDAP connection is not available for cloud tenants.Certificate Upload the CA client certificate (.crt or .pem) for LDAPS. Note: This is not applicable for LDAP connection.Sync Interval The default value is 1 hour Required parameter. The time in hours to wait between directory updates. Server Connection Timeout The default value is 30 seconds. Required parameter. The duration in seconds that Forcepoint Data Security Cloud waits before considering the Active Directory server is unreachable. -
Under the LDAPS Schema section, enter values for the following fields:
Parameter Values Description Base DN For example: dc=example,dc=com Required parameter. Proper base for the Active Directory where Forcepoint Data Security Cloud starts searching the directory structure. Starting point to look for a user. User Base DN For example: cn=users,dc=example,dc=com Starting point to look for user. Group Base DN For example: cn=groups,dc=example,dc=com Starting point to look for a group. Organization Unit DN For example: dc=rbi,dc=qa,dc=forcepoint,dc=fpoptest Starting point to look for Organization Unit. -
Under the User Schema section, enter values for the following fields:
Parameter Values Description First Name givenName The user attribute whose value is a first name. Last Name sn The user attribute whose value is a last name. NTLM Identity NTLM Identity should meet the following criteria: - Each attribute should be having single % as prefix and suffix.
- Use only positive numbers (zero is included) as index value for DN and DC attributes.
- Only DN[n] and DC[n] are allowed. Any other prefixes like AZ[n] are prohibited to use.
- Do not use any special character other than % [ ] . - / \
Manager Long Name displayName The user attribute whose value is a manager long name. Contact Number Attribute mobile Contact number of the user. Display Name Attribute cn Required parameter. The user attribute whose value is the display name. Email Attribute mail Required parameter. The user attribute whose value is the email address. Filter (&(objectCategory=person)(objectClass=user)) Required parameter. Select the users that match the filter. This can be used to limit the number of users with access to Forcepoint Data Security Cloud. Fixed ID Attribute objectGUID Required parameter. This is a fixed attribute in LDAP. It is used to search user/group in the database and based on the availability of a match, the user or user groups are updated or created. Group Member Attribute memberOf Required parameter. This attribute defines the members of users in the user group. User Attribute sAMAccountName or userPrincipalName Required parameter. The attribute whose values match with the username part of the credential entered by the users when logging into Forcepoint Data Security Cloud. User Principal Name Attribute userPrincipalName ObjectSID Attribute objectSid ObjectGUID Attribute objectGUID MS DS ConsistencyGUID Attribute mS-DS-ConsistencyGuid SAM Account Name sAMAccountName -
Under the Group Schema section, enter values for the following fields:
Parameter Values Description Filter (objectCategory=group) Required parameter. Criteria to filter or limit the number of groups that are imported to Forcepoint Data Security Cloud. Fixed ID Attribute cn for OpenLDAP, name for AD Required parameter. This is a fixed attribute in LDAP. It is used to search user groups in the database and based on the availability of a match, the user groups are updated or created. Name Attribute cn for OpenLDAP, name for AD Required parameter. Select the groups that match the filter. Group Email Required parameter. The attribute holding the email of a group. -
Under the Organization Unit Schema section, enter value for the following field:
Parameter Values Description Filter (objectClass=organizationalUnit) Required parameter. Criteria to filter or limit the number of Organization Units that are imported to Forcepoint Data Security Cloud. - Click Save to save the Active Directory settings.