Configuring policy scan
Steps
-
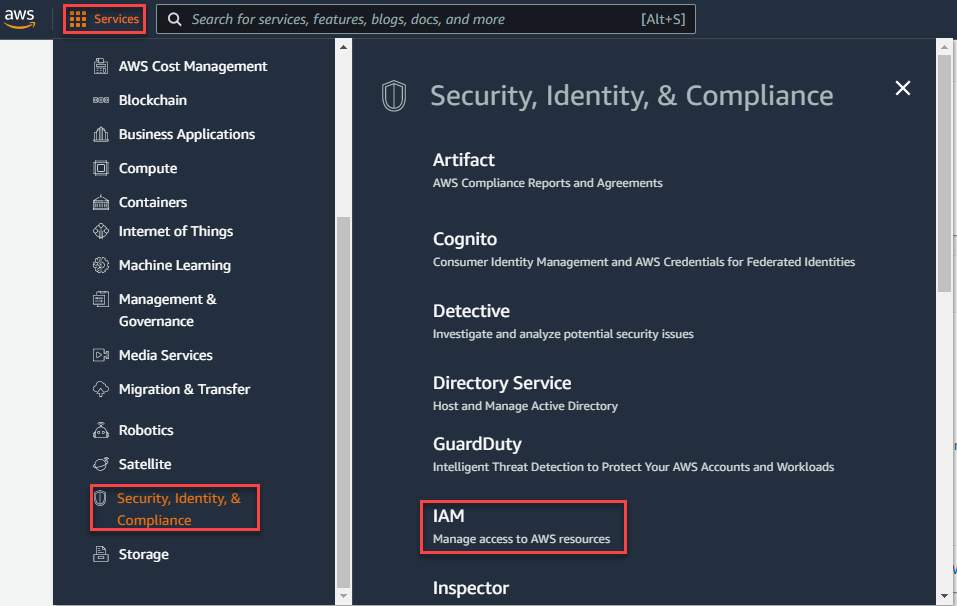
On the AWS console, navigate to Services > Security, Identity, & Compliance > IAM.
-
Select Policies from the left navigation pane under Access management and then click Create Policy to create a new policy.

-
Select the JSON tab and then enter the following JSON sample script replacing items in <> with your particular bucket (do not include the <> brackets). You can also use the wildcard "*" (asterisk) to include all buckets in the scan instead of only specific buckets. Once done, click Next
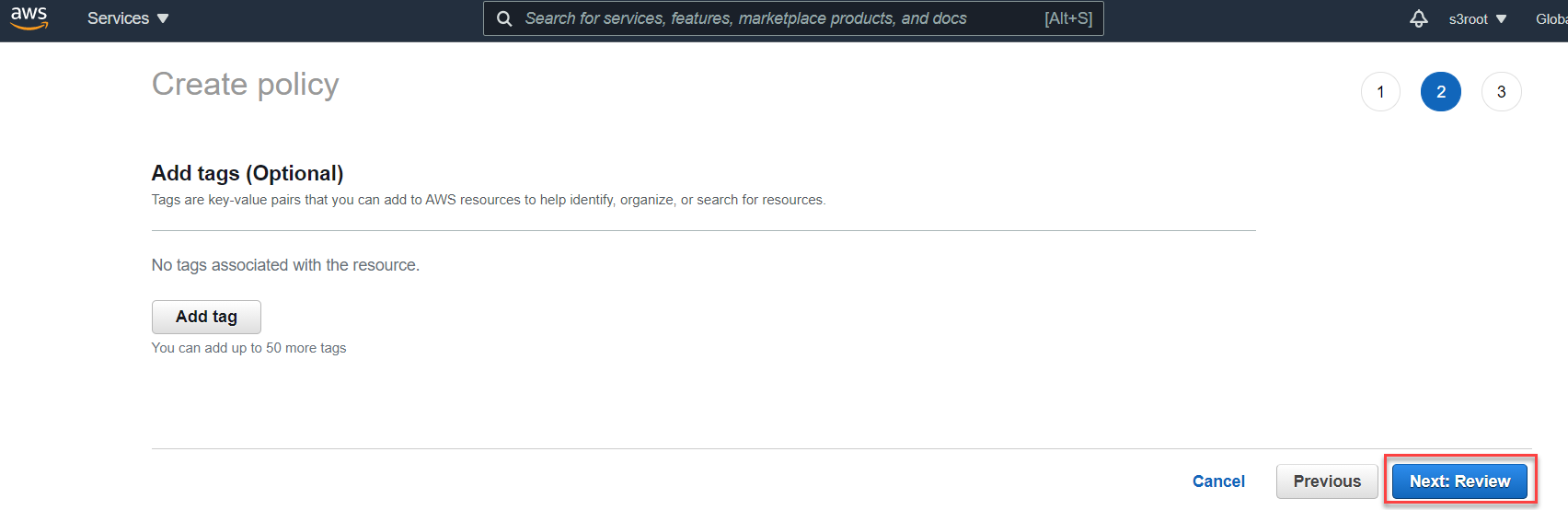
Tags at the bottom.
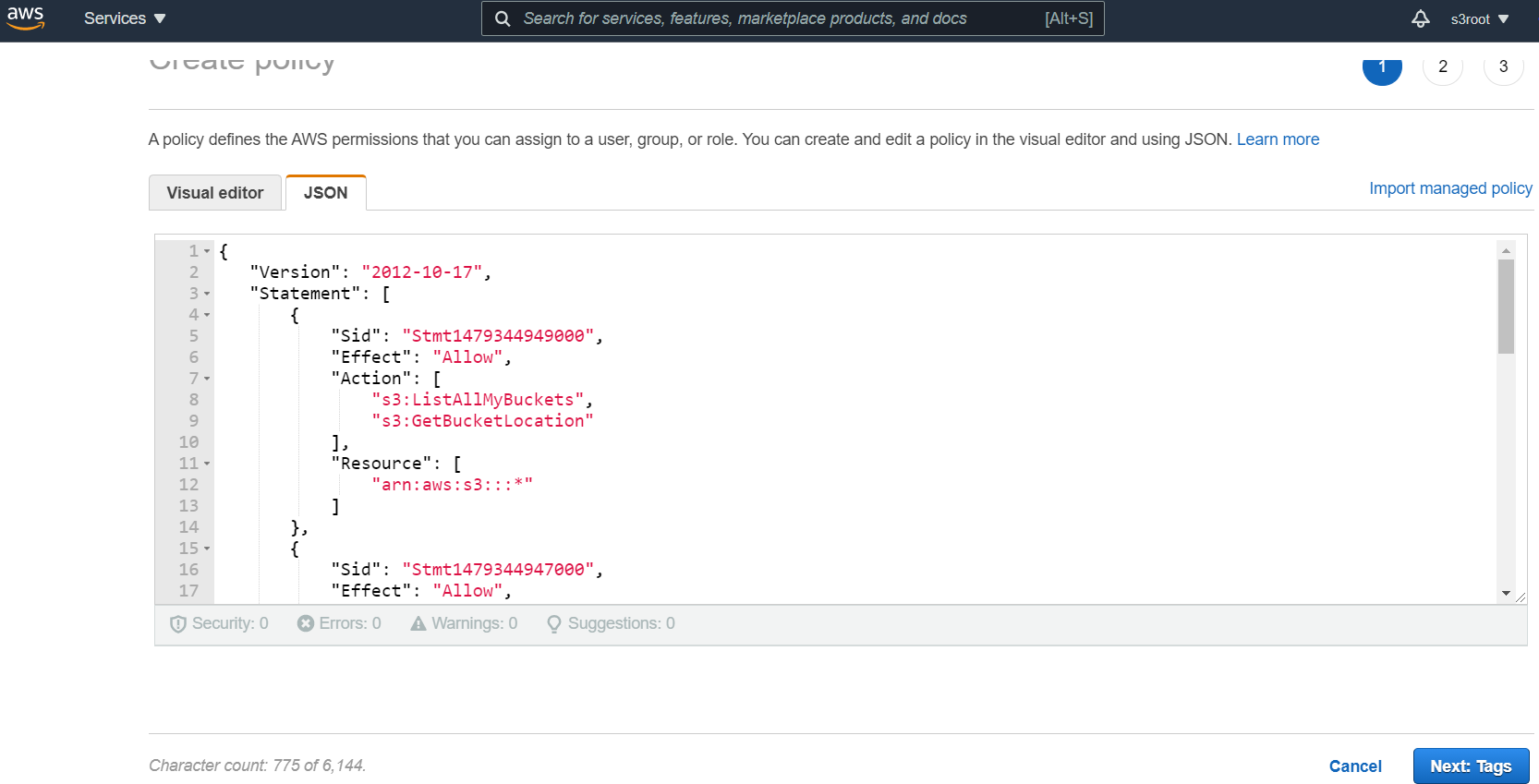
{ "Version": "2012-10-17", "Statement": [ { "Sid": "Stmt1479344949000", "Effect": "Allow", "Action": [ "s3:ListAllMyBuckets", "s3:GetBucketLocation" ], "Resource": [ "arn:aws:s3:::*" ] }, { "Sid": "Stmt1479344947000", "Effect": "Allow", "Action": [ "s3:ListBucket", "s3:GetBucketLocation", "s3:GetBucketAcl", "s3:GetBucketPolicy", "s3:GetBucketNotification", "s3:PutBucketNotification" ], "Resource": [ "arn:aws:s3:::<bucket name here>" ] }, { "Sid": "Stmt1479344948000", "Effect": "Allow", "Action": [ "s3:GetObject", "s3:GetObjectACL", "s3:PutObject", "s3:DeleteObject" ], "Resource": [ "arn:aws:s3:::<bucket name here>/*" ] }, { "Sid": "Stmt1479344946000", "Effect": "Allow", "Action": [ "iam:GetPolicyVersion", "iam:GetPolicy", "iam:ListAttachedRolePolicies", "iam:ListRoles", "iam:ListRolePolicies", "iam:GetRolePolicy" ], "Resource": "*" } ] } -
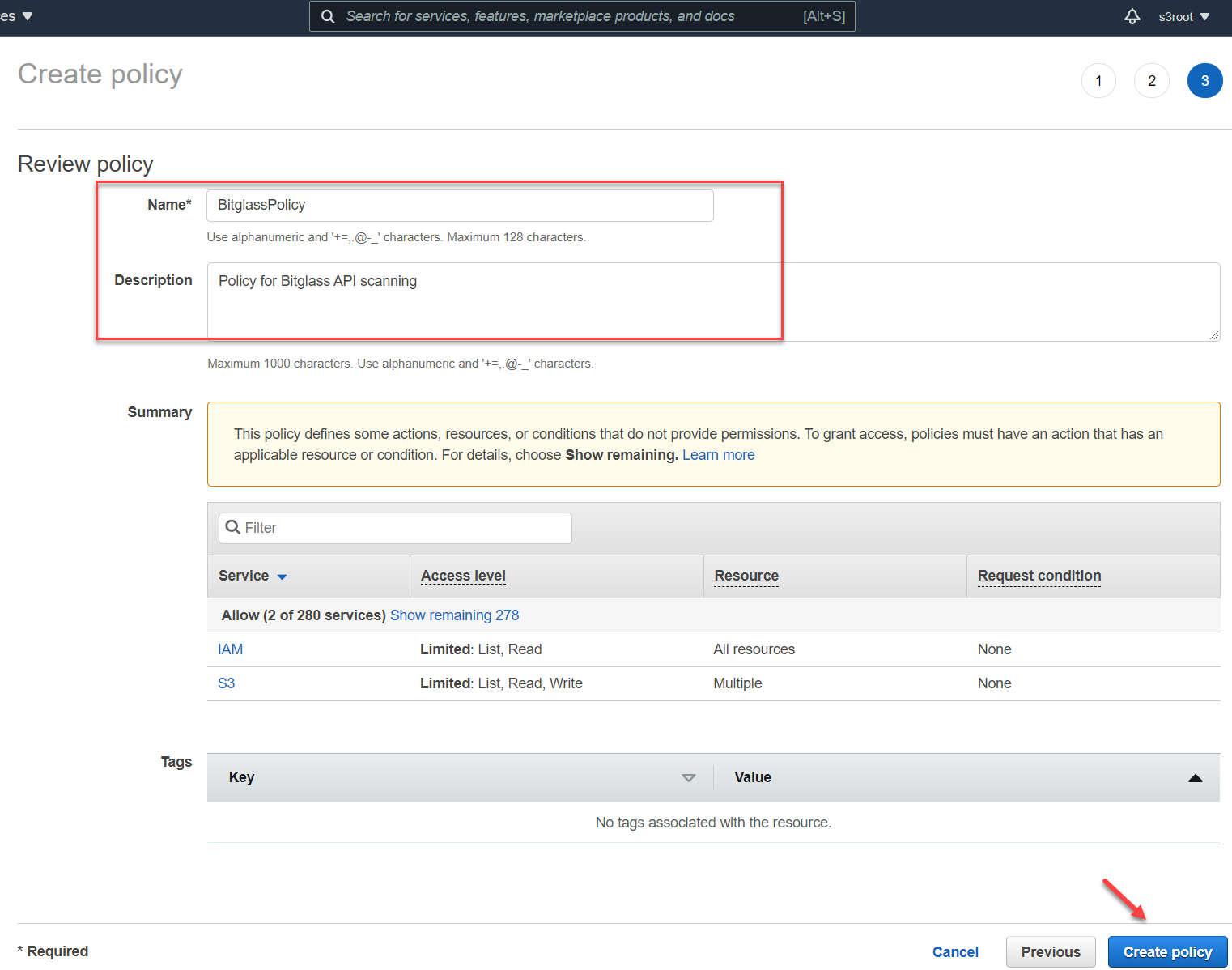
You can add tags to your policy here, otherwise click Next: Review at the bottom to proceed. Give the policy a name and provide a description and then click
Create Policy. Now you can assign this policy to existing user accounts or during a new user creation.