Once you have determined the means through which you will determine a managed device, you can move on to creating policies to provide greater access to managed devices while restricting
access to unmanaged devices.
Forcepoint Data Security Cloud | SSE recommends for typical use cases to grant direct app
access on managed devices for both thick client applications and web while using secure app access on unmanaged devices for web and ActiveSync (blocking thick client application). The
following steps will walk you through how to create the policy.
Steps
-
Navigate to the page and locate the app in question you want to manage.
-
Choose to edit your current policies or create new ones. At a minimum you will need two policies. The policies will look something similar to below:
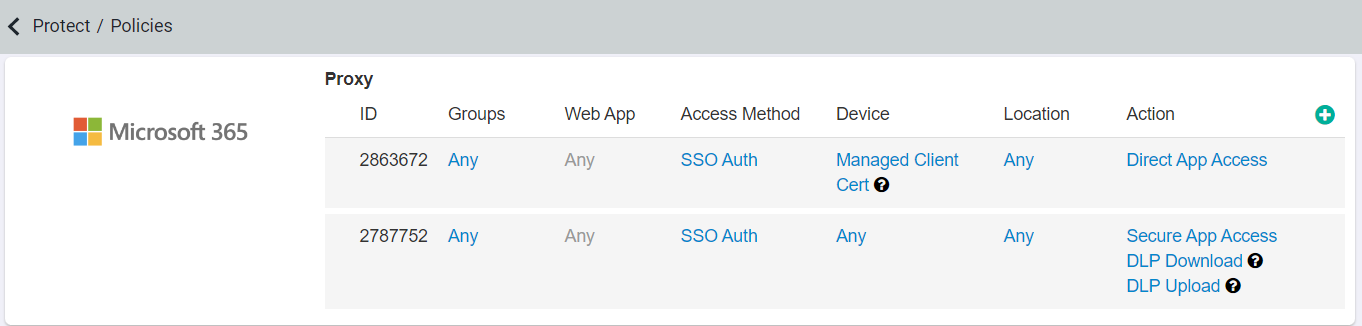
Note: Policies are applied in order from the top to the bottom. This means whichever policy is first on the page will be applied first before moving on to the next policy (if
applicable). There is also an implicit deny policy at the bottom for any criteria that wasn't specified.
In the example above the first action taken is to identify if a device is managed and, if they are managed, they are granted direct app access for web traffic. If the device
is not identified as a managed device, it moves to the second policy where it is granted secure access to the cloud application only on Web. You'll see additional policies to
specify allowing client app access (for both modern and legacy Office applications) only if the devices are managed devices.
Below you will go over how you can adjust
your policy lines as needed.
-
The first policy will provide Direct App Access on managed devices over Web Traffic.
-
Leave Groups set to Any.
-
Leave Web App untouched (should be grayed out).
-
Select SSO Auth for Access Method.
-
Under the Device column select either Managed Client Cert if you are using client certificates or select the
Device Profile(s) (for the Device Profiling Agent) you created for distinguishing a managed device.
-
Location can be left as Any.
-
Set the Action column to Direct App Access.
-
The second policy will have unmanaged devices accessing the cloud application via secure app access but denying access on client applications.
-
Leave Groups set to Any.
-
Leave Web App column set to Any.
-
Select SSO Auth or ActiveSync for Access Method.
-
Leave Device as Any.
-
Leave Location as Any.
-
Set the Action Column to Secure App Access and configure your DLP policies.