What's new
This section lists the new features and enhancements for the Forcepoint DSPM solution included in the current release.
Improved Credential Validation During Scan Execution
This update enhances the reliability of scan execution by improving how credential issues are detected and communicated.
Previously, credential validation occurred only during initial setup and when a scan configuration was created or started. If credentials became invalid during an active scan, the system did not detect the issue, leaving the scan in an In Progress state without notifying the user.
- The system now detects invalid credentials during active scans.
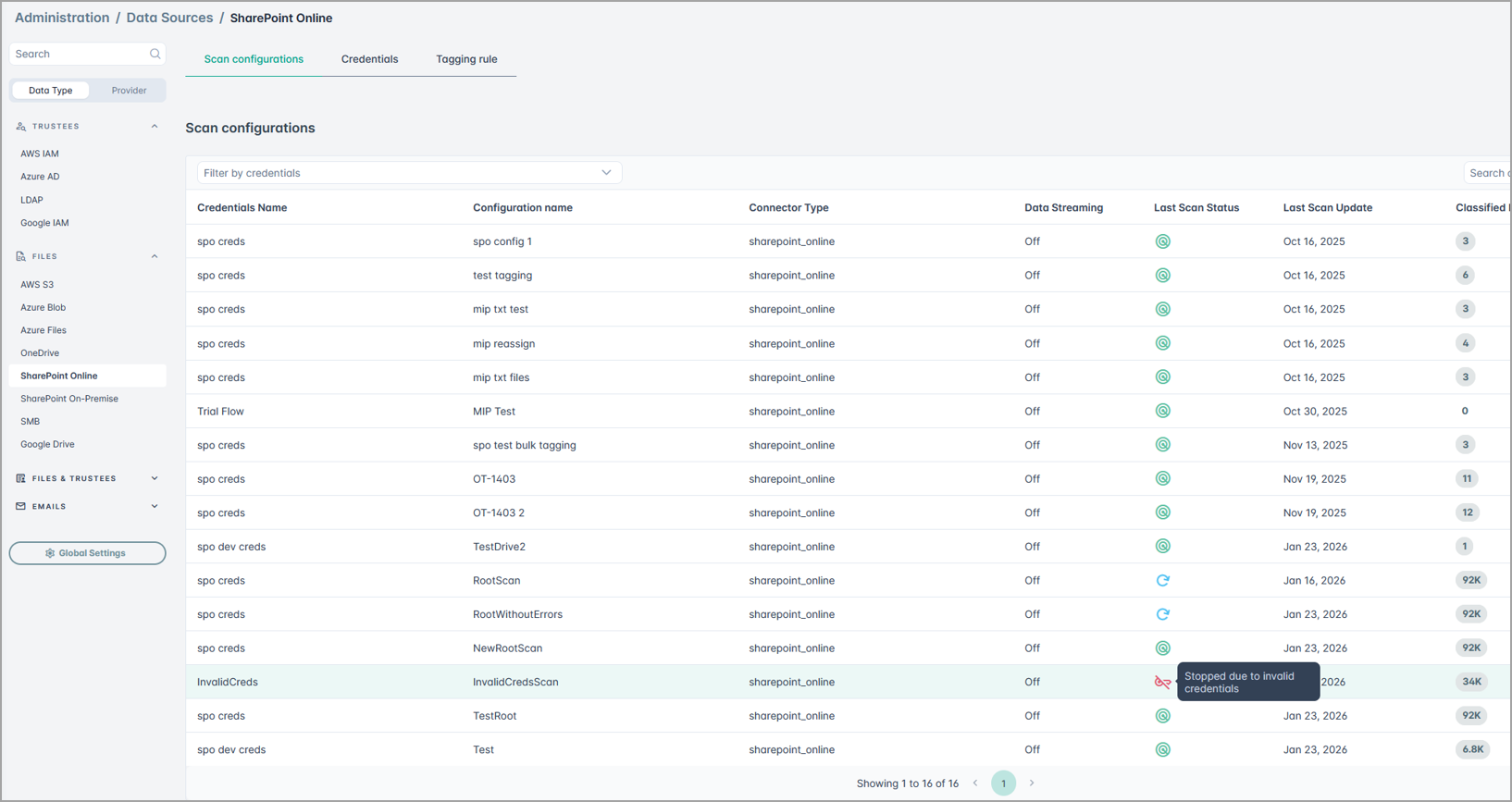
- Scans will no longer remain indefinitely in the In Progress state.
- Users are notified with clear error messages when credential failures occur.
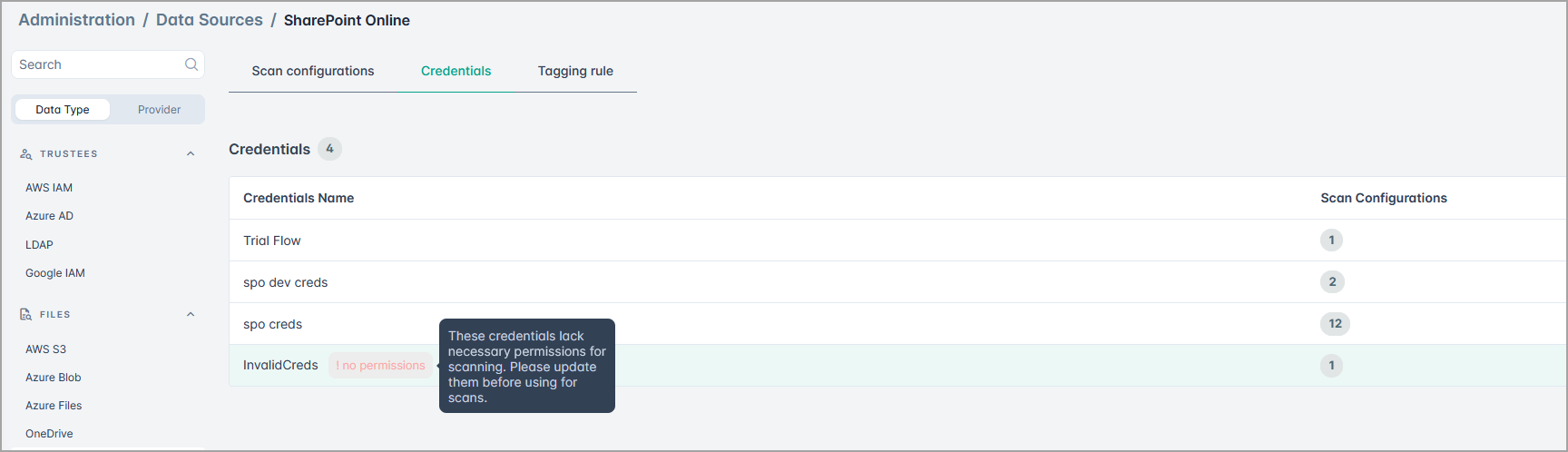
- Additionally, the system now restores the status and resumes the scan when the credentials become valid again.
These enhancements prevent unnecessary resource consumption, reduce stalled scans, and improve overall user experience and troubleshooting efficiency.
Extraction of user and permission details from structured data sources
We are introducing access governance for structured data, giving administrators a clear picture of which users and what type of permissions they have on a database. Administrators can easily view how many users have access, which schemas those users can reach, and which sensitive tables or columns are exposed.
When paired with data discovery and classification, this becomes even more powerful. If certain database accounts have access to sensitive information, administrators can quickly identify and investigate them. We also provide detailed insights into the specific permissions each user holds for every table. This makes it simpler to detect excessive privileges and take corrective action to maintain a least-privilege access model.
While creating a New Scan Configuration for structured data, you can now enable Fetch Permissions to collect access permission details for schemas, tables, and any shared settings before initiating the database scan or trustee scan either for the entire data source or for a specific path.
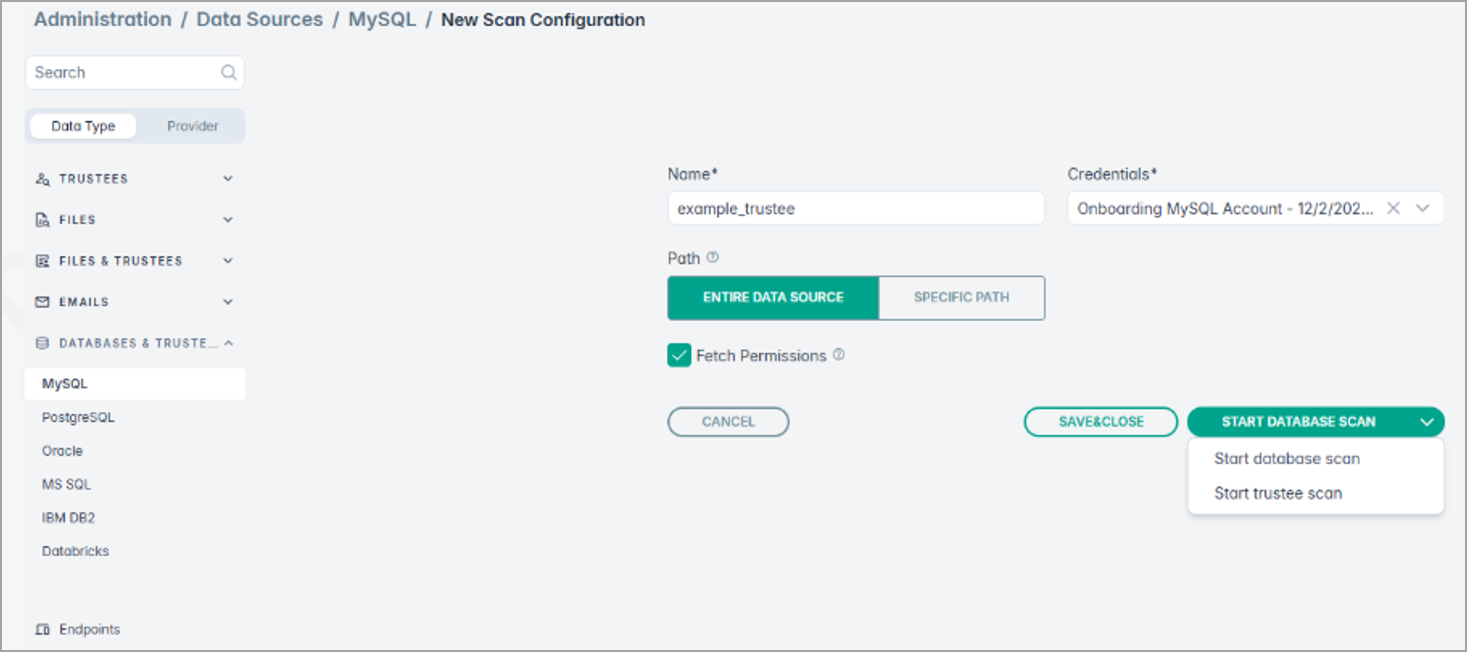
For detailed information, refer to Creating and Starting MySQL Scan Configuration section.