Adding SCIM application in Okta
After generating a SCIM access token, you should create the SCIM application in Okta so that admins can provision/deprovision users directly in Okta and have those users automatically created, attributes edited, or disabled within Forcepoint Data Security Cloud.
Steps
- Sign in to Forcepoint Data Security Cloud.
- From the application waffle, select Admin.
-
From the left Navigation Pane, click the SAML
 icon.
icon.
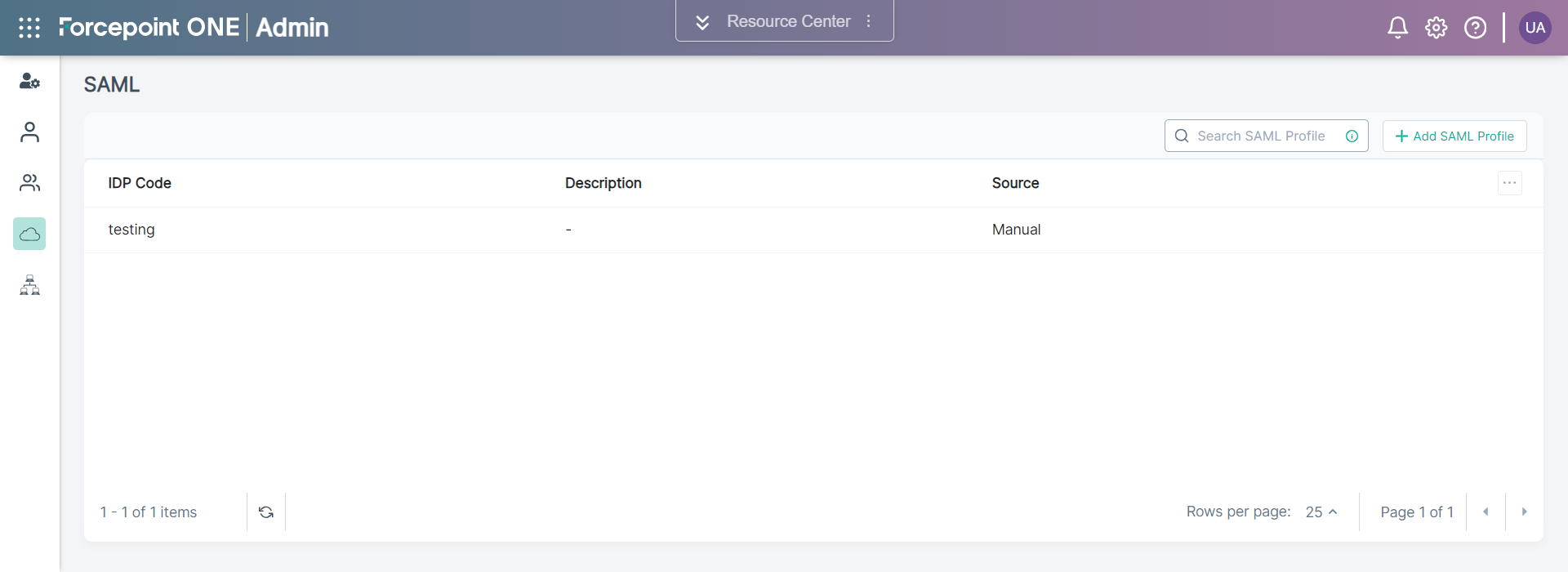
The following page opens displaying existing SAML Profiles.
-
To add a new SAML Profile, click +Add SAML Profile.
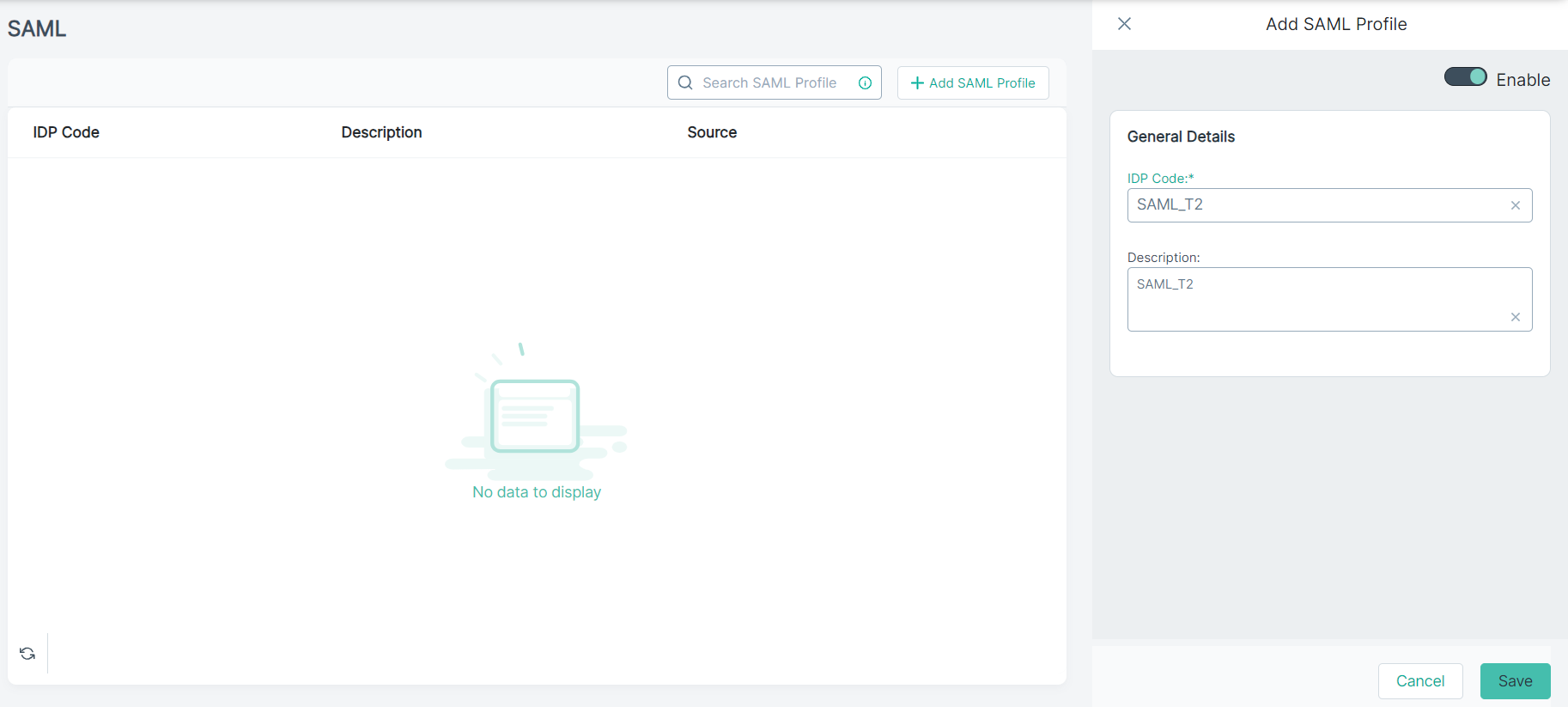
The Add SAML Profile opens on the right pane.
-
Under the General Details section:
-
Enter an unique IDP Code and Description.
Note: The IDP Code is required. The profile cannot be saved without a code.
-
To save the SAML Profile, click Save.
The SAML profile gets created.
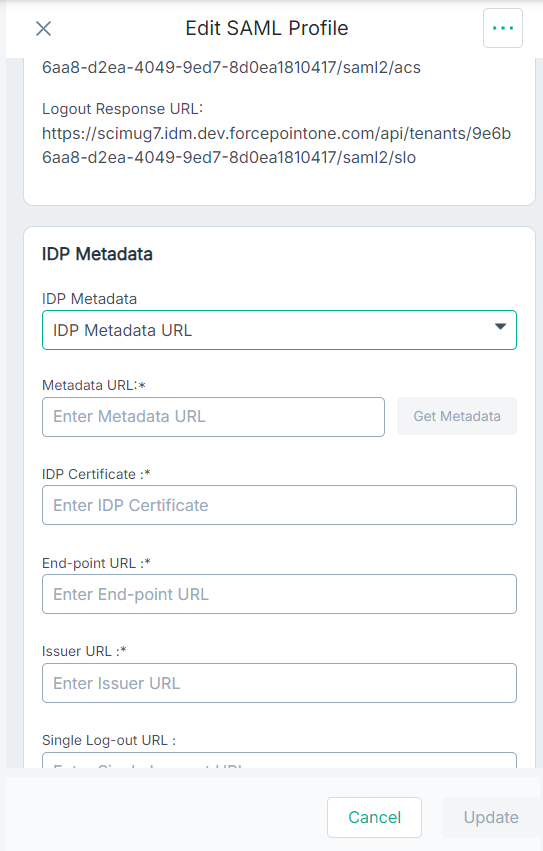
The Add SAML Profile pane also displays ACS URL, and Logout Response URL read-only fields under the General Details section along with an additional section, IDP Metadata.
- ACS URL - The URL location where the SAML assertion is sent with an HTTP POST.
- Logout Response URL - The URL location on the service provider where the identity provider sends its sign out response.
-
Enter an unique IDP Code and Description.
- Open a new browser window/tab and login to your Okta admin portal.
-
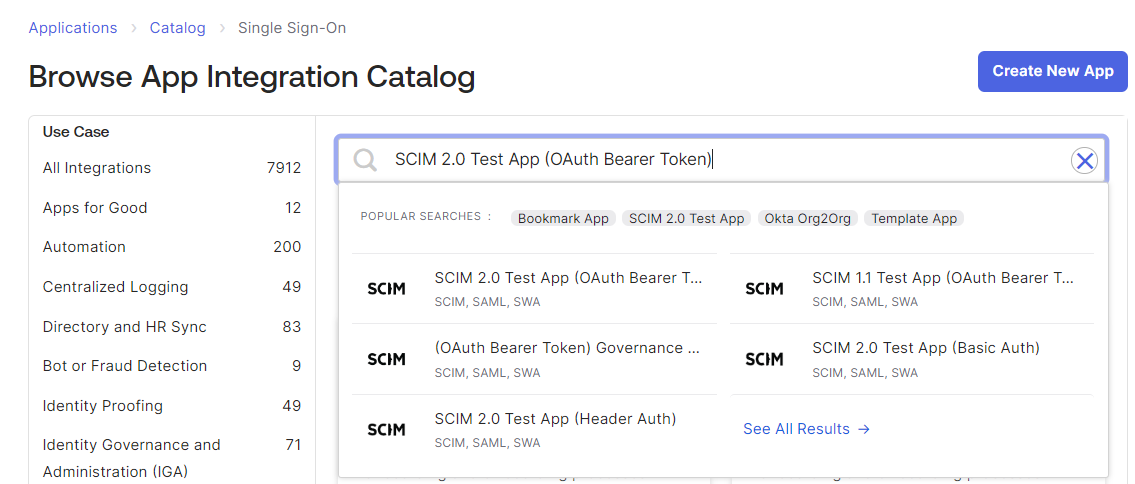
Navigate to Application > Application > Browse App Catalog and then search for SCIM 2.0 Test App (OAuth Bearer Token).
-
Click the SCIM 2.0 Test App (OAuth Bearer Token) instance and then click Add Integration.
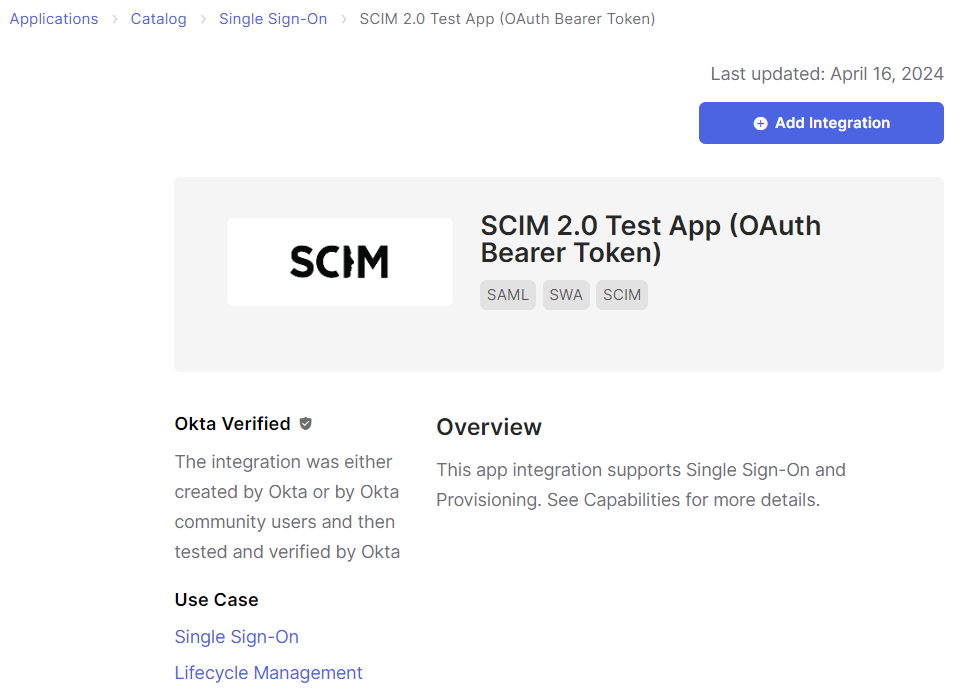
The Add SCIM 2.0 Test App (OAuth Bearer Token) page opens.
-
On the General Settings tab:
-
Rename the Application Label so it is recognizable.
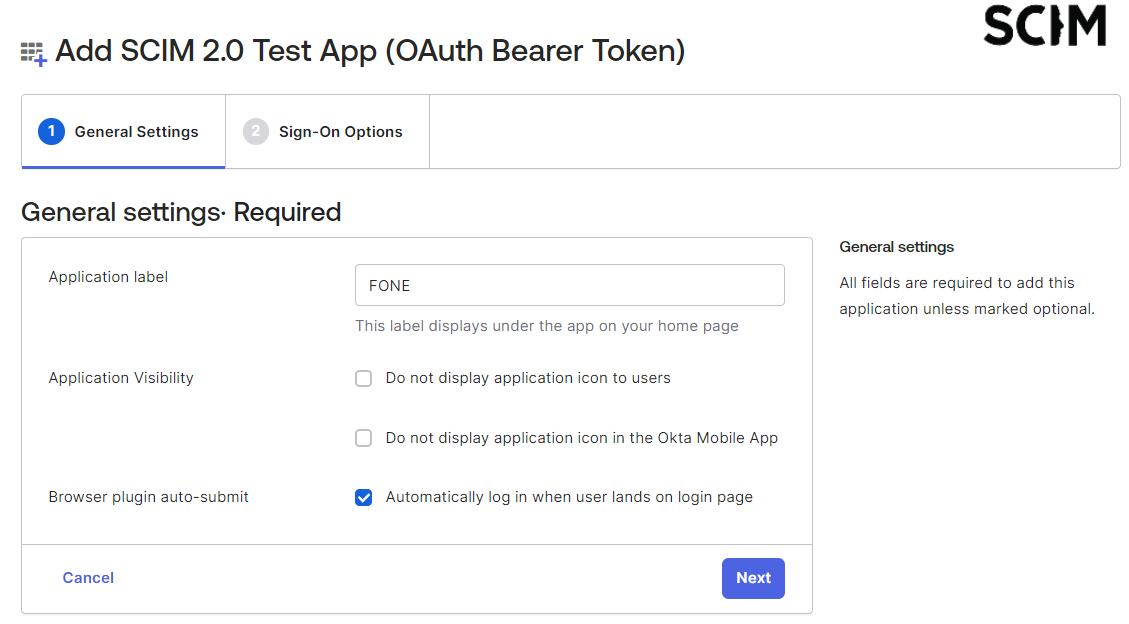
- Click Next.
-
Rename the Application Label so it is recognizable.
-
On the Sign-On Options tab, follow the steps below after copying the Metadata URL from the Metadata details
section of Okta:
- Back on the Forcepoint Data Security Cloud browser window/tab, select the specific SAML profile from the list which you want to edit. This opens the editor.
- On the IdP Metadata section, select the IDP Metadata URL option from the IdP Metadata drop-down to pull metadata details from Okta.
- Paste the Metadata URL that you copied from Okta in the Metadata URL field.
-
To pull the metadata based on url, click Get Metadata.
After clicking Get Metadata, other fields are auto-populated.
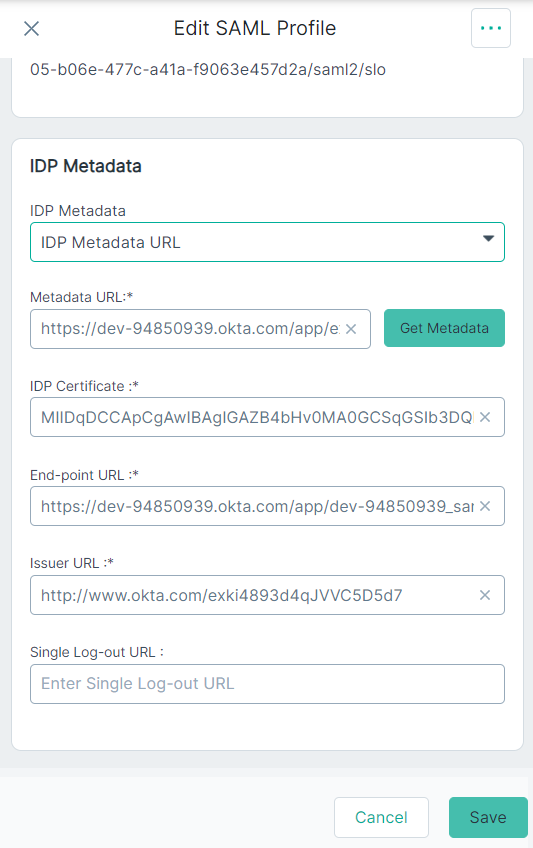
- Click Update to save the changes.
-
Copy the ACS URL from Forcepoint Data Security Cloud browser window/tab and paste it in the ACS URL
field of the Sign-On Options tab on Okta browser window/tab.
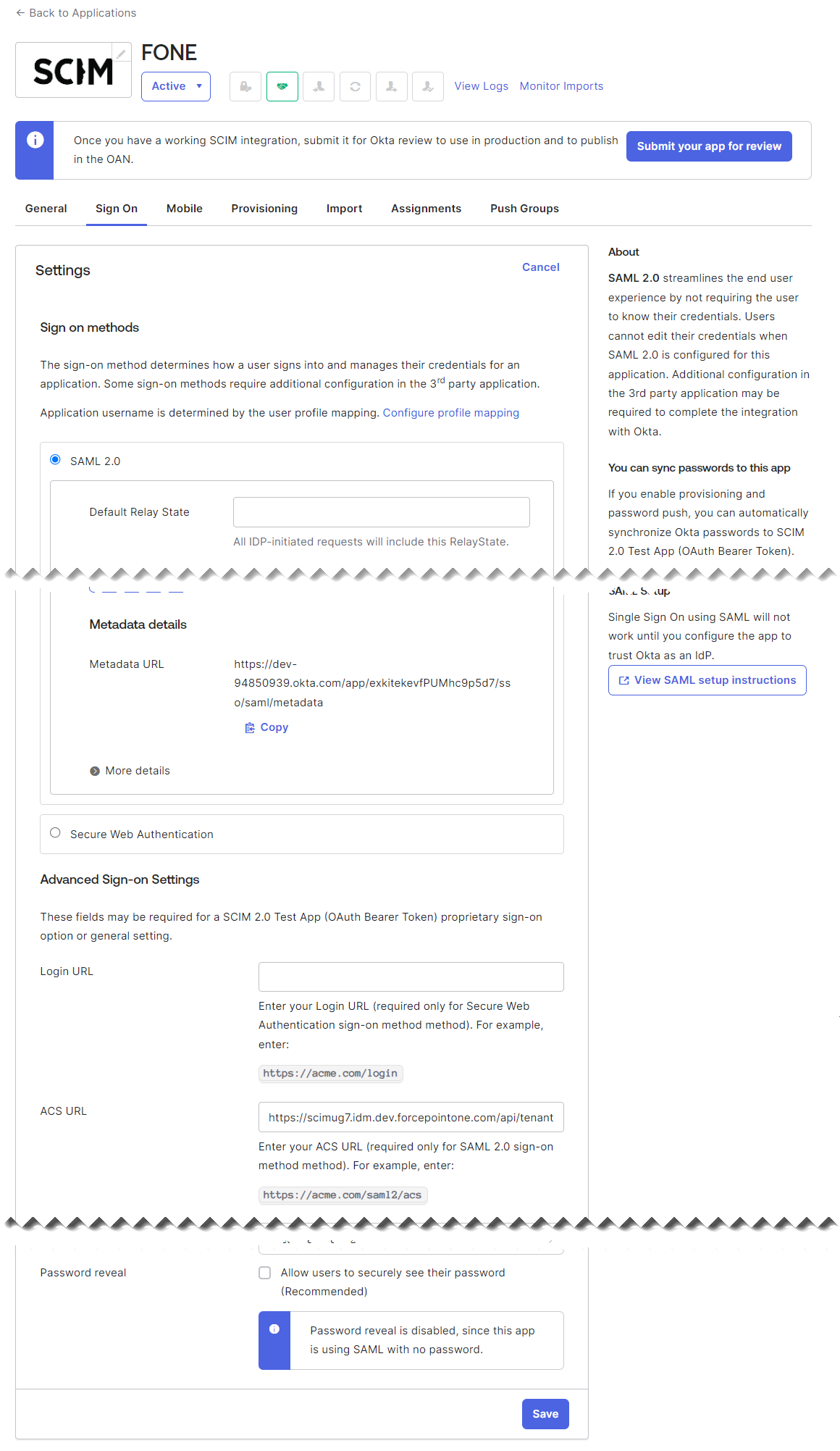
- Copy the IDP Code from Forcepoint Data Security Cloud browser window/tab and paste it in the ACS URL field of the Sign-On Options tab on Okta browser window/tab.
-
Click Done to create SCIM app instance.
The SCIM application opens displaying the Assignments tab.
-
On the Provisioning tab, click Configure API Integration.
-
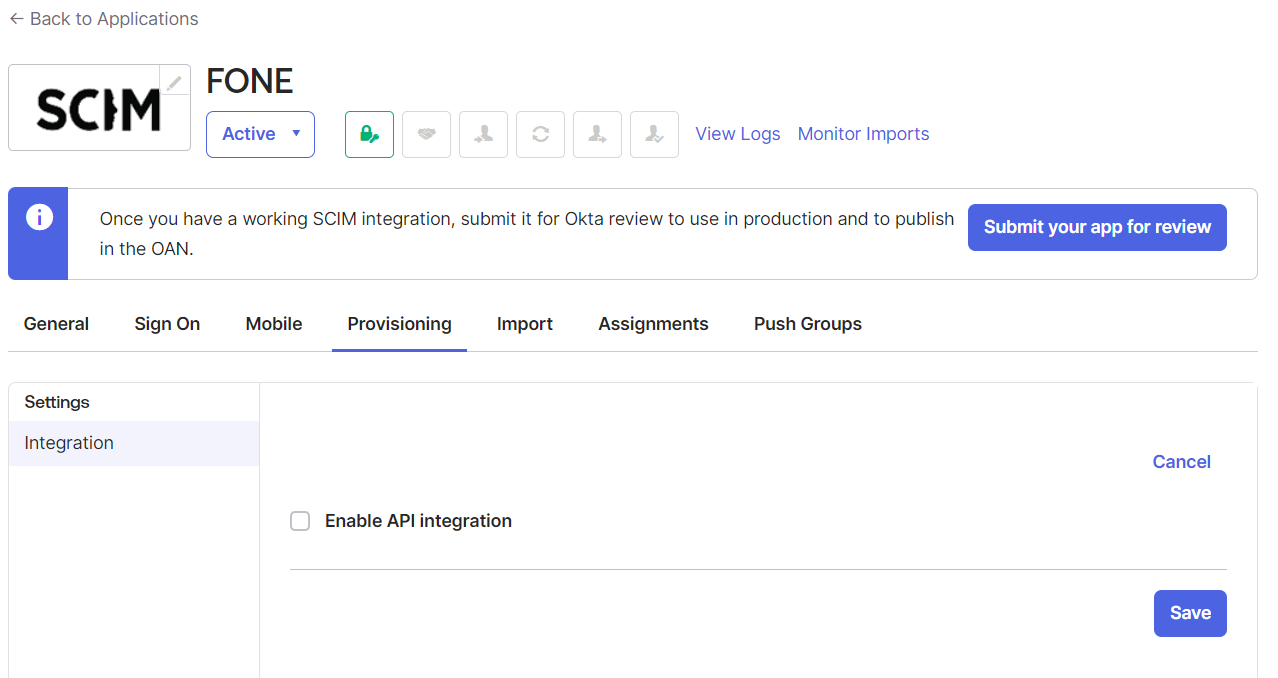
Select the Enable API integration checkbox to display additional options.
-
Copy the Base URL from the Admin > SCIM page in Forcepoint Data Security Cloud and paste it in the Base URL field.
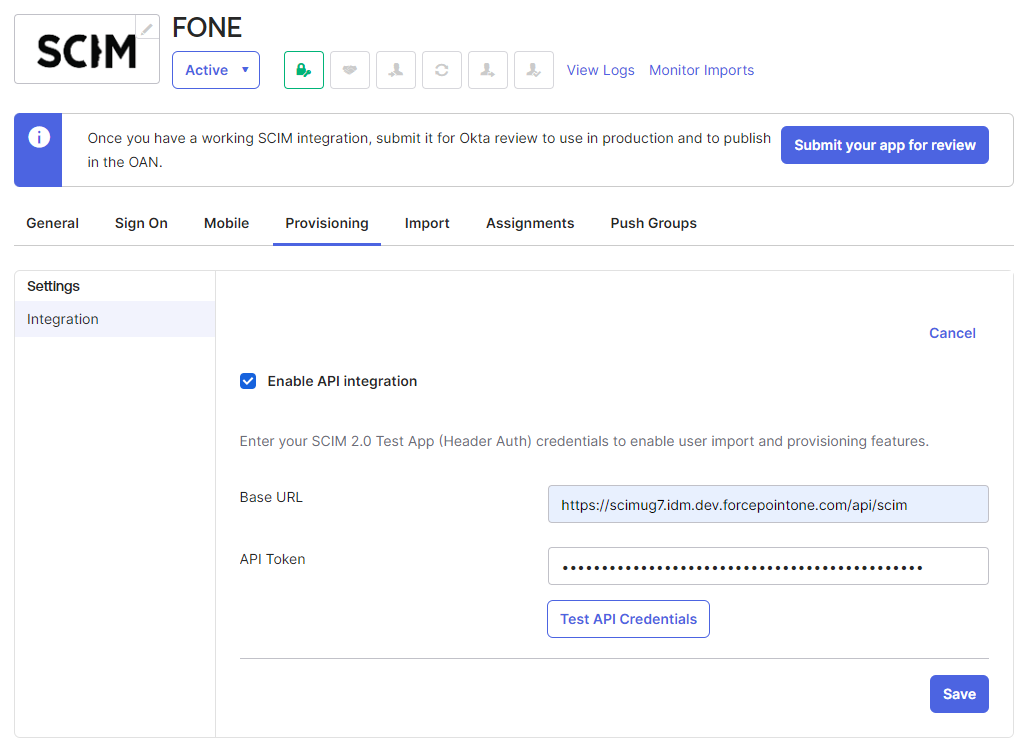
- In API Token, paste the SCIM access Token that you generated during the SCIM token generation.
-
Click Test API Credentials and then click Save if API credentials are validated successfully.
Once you have successfully enabled the API integration, you will see options for what is being provisioned to the App.
-
Copy the Base URL from the Admin > SCIM page in Forcepoint Data Security Cloud and paste it in the Base URL field.
-
On the To App tab of the Settings column on the left:
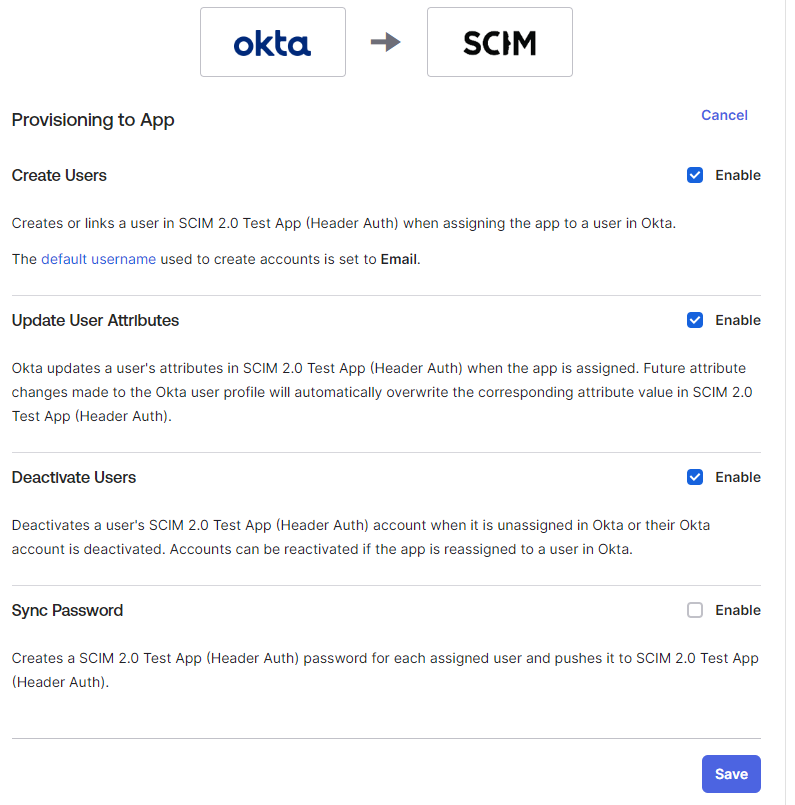
Note: Forcepoint Data Security Cloud currently does not support Sync Password.- Click the Edit button adjacent to the Provisioning to App section.
- Select the Create Users, Update User Attributes, and Deactivate Users checkboxes.
- After selecting the checkboxes, click Save.
-
Under the Attribute Mappings section, click Go to Profile Editor.
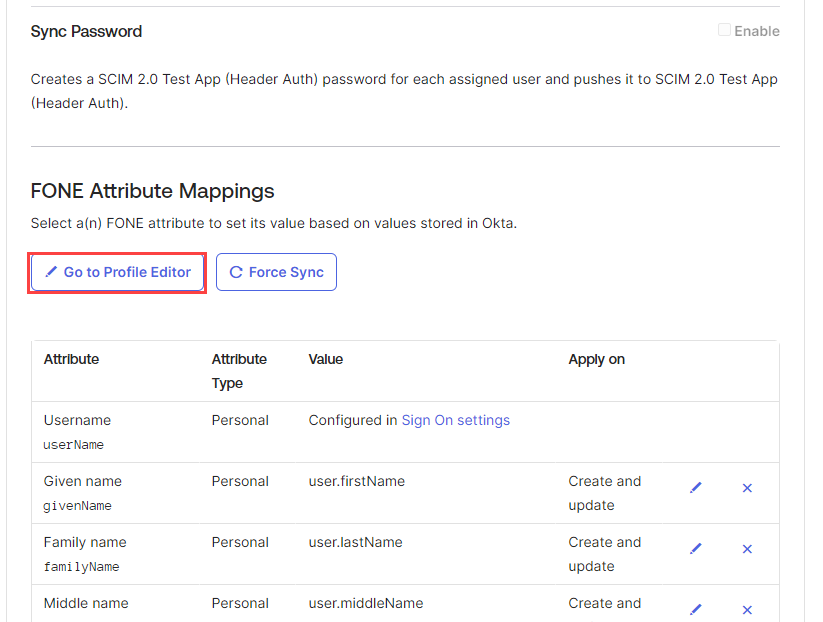
You will be redirected to the Profile Editor page under Directory.
-
On the Profile Editor page:
-
Add the attributes to the list. Click Add Attribute and then fill out the new dialog window with the information below for each of the attributes
you wish to add.
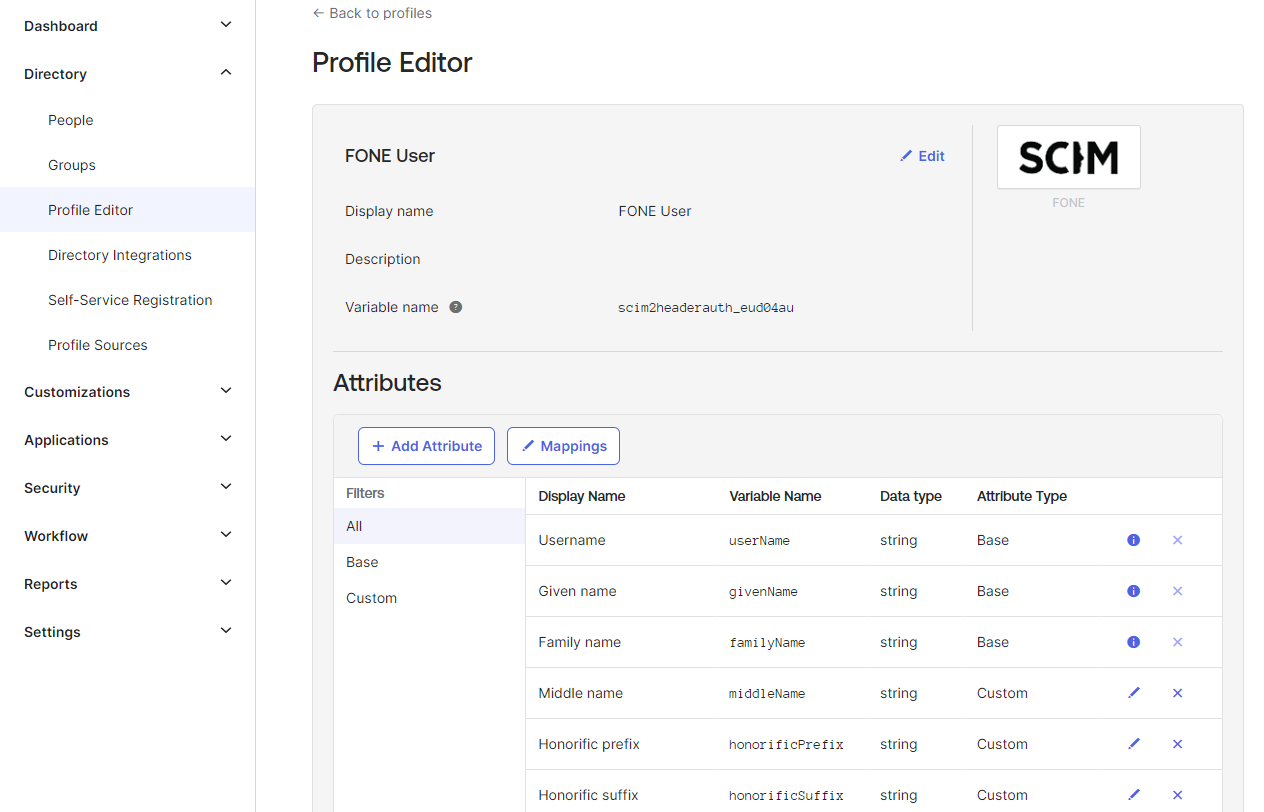
- To add an attribute, click + Add Attribute.
-
On the Add Attribute dialog, add the following:
Table 1. Secondary Email Variable Value Data type string Display name Secondary Email Variable Name secondaryEmail External name emails.^[primary==false].value External namespace urn:ietf:params:scim:schemas:core:2.0:User Attribute length Set the length of attribute to Less than 128 Table 2. Secondary Email Type Variable Value Data type string Display name Secondary Email Variable Name secondaryEmailType External name emails.^[primary==false].type External namespace urn:ietf:params:scim:schemas:core:2.0:User Attribute length Set the length of attribute to Less than 128 Table 3. Secondary Phone Variable Value Data type string Display name Secondary Phone Variable Name mobilePhone External name phoneNumbers.^[primary==false].value External namespace urn:ietf:params:scim:schemas:core:2.0:User Attribute length Set the length of attribute to Less than 128 Table 4. Secondary Phone Type Variable Value Data type string Display name Secondary Phone Type Variable Name secondaryPhoneType External name phoneNumbers.^[primary==false].type External namespace urn:ietf:params:scim:schemas:core:2.0:User Attribute length Set the length of attribute to Less than 128 -
Once you have added all the attributes, click on the Mappings button.
The (Name of your SCIM app) User Profile Mappings dialog opens displaying existing mappings.
- Click the Okta User to (Name of your SCIM app) tab.
-
Remove the mapping for all the attributes, that are not needed, honorificPrefix, honorificSuffix, nickName, profileUrl, entitlements, roles, employeeNumber, costCenter,
organization, division, department, managerValue, and managerDisplayName.
-
Scroll to the bottom and you should see blank fields representing the number of attributes you added but have not been mapped yet.
Select each attribute from the drop-down.
- Enter user.secondEmail against secondaryEmail.
- Enter (user.secondEmail != null && user.secondEmail != '') ? 'home' : '' against secondaryEmailType.
- Enter user.mobilePhone against mobilePhone.
- Enter (user.mobilePhone != null && user.mobilePhone != '') ? 'home' : '' against secondaryPhoneType.
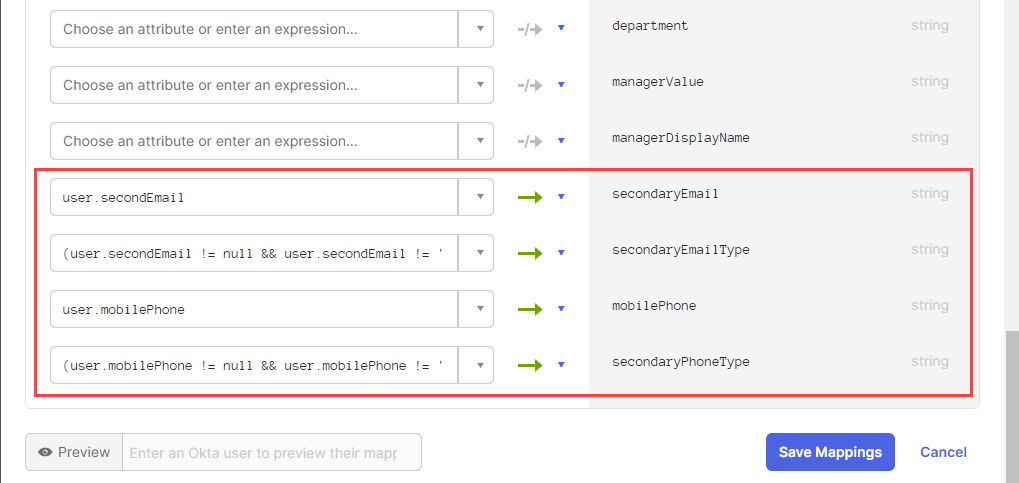
- To save the mappings, click Save Mappings.
-
To apply these mappings to all users with the profile, click Apply updates now.
Now, when Okta provisions the users into Forcepoint Data Security Cloud, it will also includes these additional attributes you have added/mapped.
-
Add the attributes to the list. Click Add Attribute and then fill out the new dialog window with the information below for each of the attributes
you wish to add.
-
To push/provision users individually through the Assignments tab of the SCIM application:
-
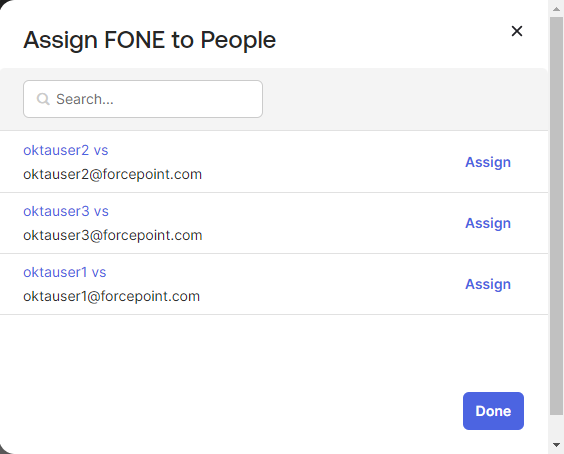
Click the Assign drop-down and select Assign to People.
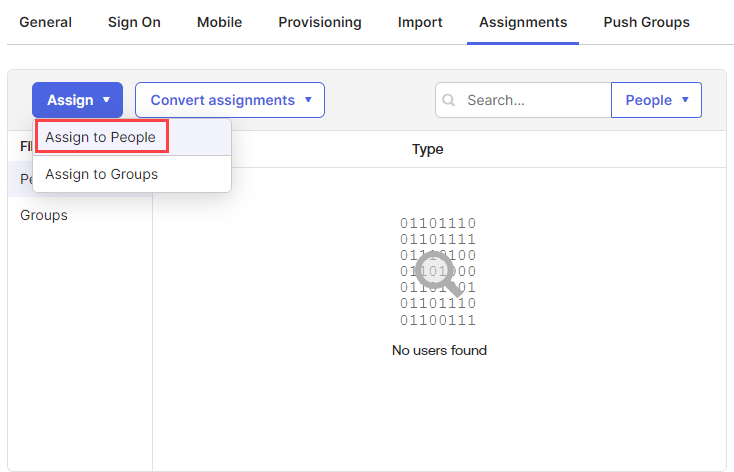
-
In the dialog, search for and assign the users you want to be provisioned over to your application and click the Assign button.
-
Verify the user details in the dialog. If required, modify the user details.
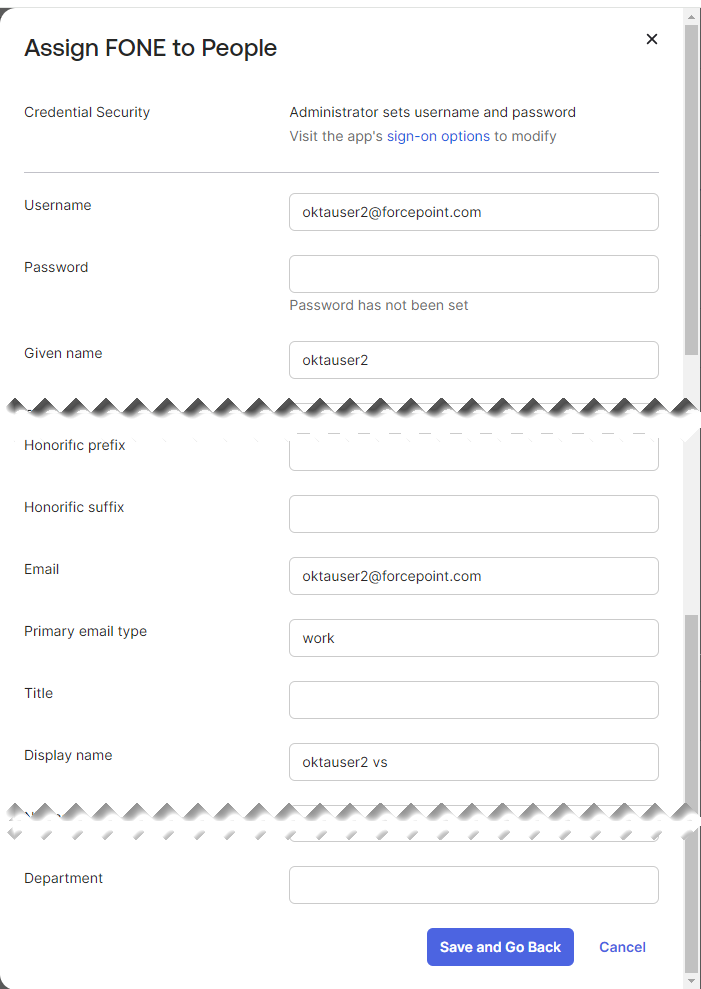
- To save the changes, click Save and Go Back.
-
Click Done after assigning all the required users to the application.
All the users assigned to the application will automatically be pushed into Forcepoint Data Security Cloud along with their attributes and future changes (or deactivation) to their account in Okta will get pushed to Forcepoint Data Security Cloud automatically as well.
You can also assign users to the application from their user profile under the Applications tab of the Directory > People page.
-
Click the Assign drop-down and select Assign to People.
-
To push/provision a group of users together through the Assignments tab of the SCIM application:
-
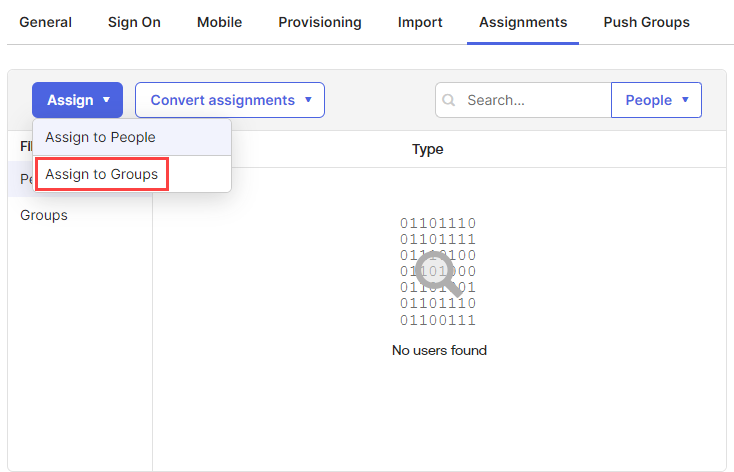
Click the Assign drop-down and select Assign to Groups.
-
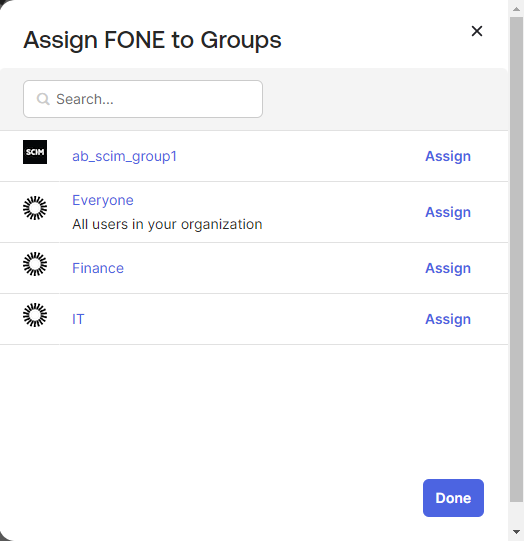
In the dialog, search for and assign the groups you want to be provisioned over to your application and click the Assign button.
-
Verify the user details in the dialog. If required, modify the user details.
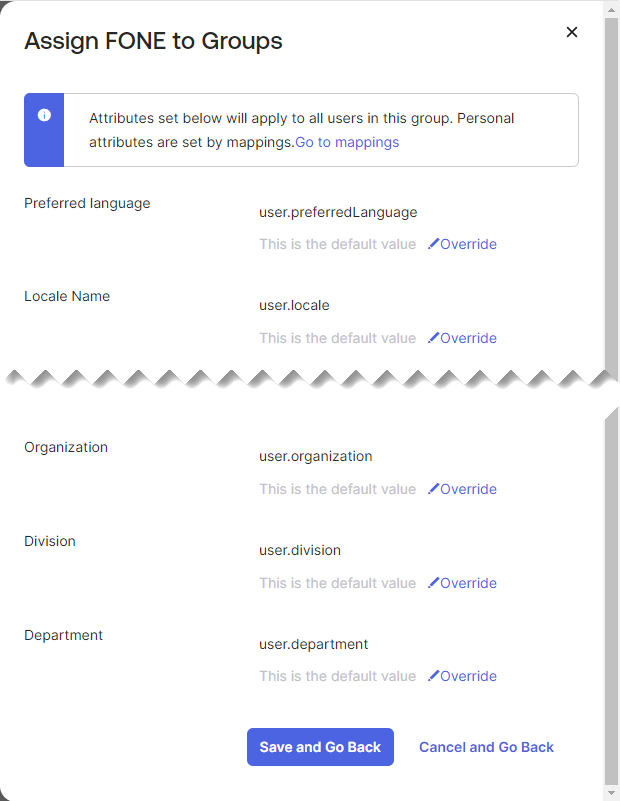
- To save the changes, click Save and Go Back.
-
Click Done after assigning all the required groups to the application.
All the users associated with the selected groups assigned to the application will automatically be pushed into Forcepoint Data Security Cloud along with their attributes and future changes (or deactivation) to their group in Okta will get pushed to Forcepoint Data Security Cloud automatically as well.
You can also assign groups to the application from the group profile under the Applications tab of the Directory > Groups page.
Note: Adding groups the application or from group profile will only sync the users over but not the group object itself. If you want the group information synced in addition to the users, follow the steps in Step 12 in addition. -
Click the Assign drop-down and select Assign to Groups.
-
To sync over the group object information, add those groups to the Push Groups tab in the SCIM application in addition to assigning the groups to the
application.
-
Click the Push Groups drop-down, select the Find groups by name.
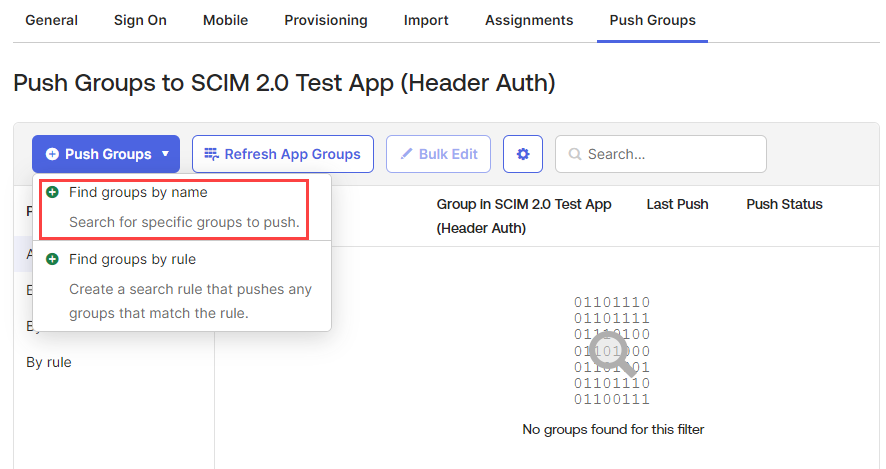
-
Search for the group(s) you wish to add by name and select it.
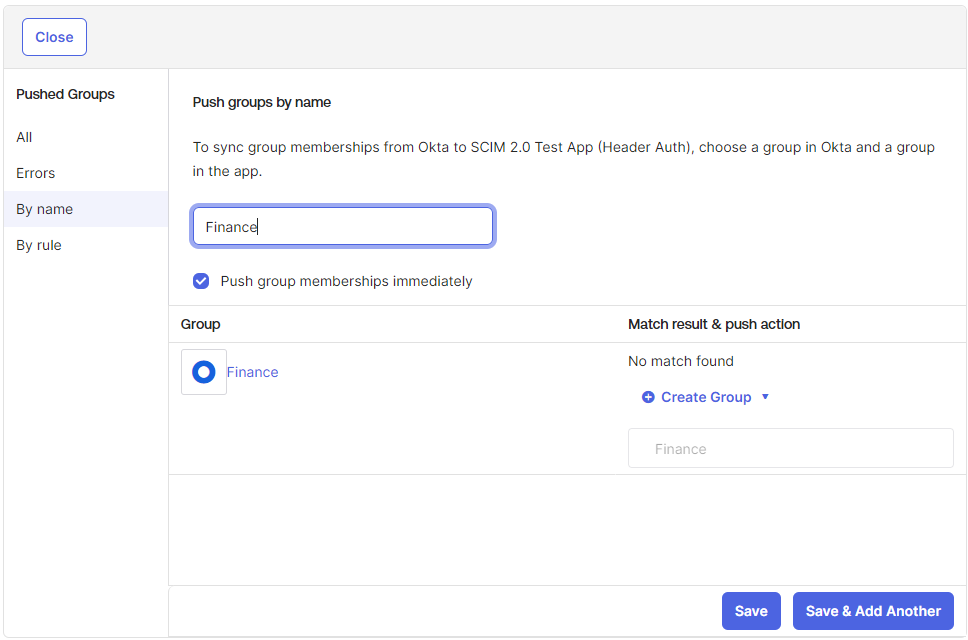
-
Leave the Match result and push action section as is and then click either Save or Save & Add
Another if you intend to add more groups.
Once the group is added, the group object will be provisioned into Forcepoint Data Security Cloud. Admins can choose to manually push these to Forcepoint Data Security Cloud, but the push should happen automatically.
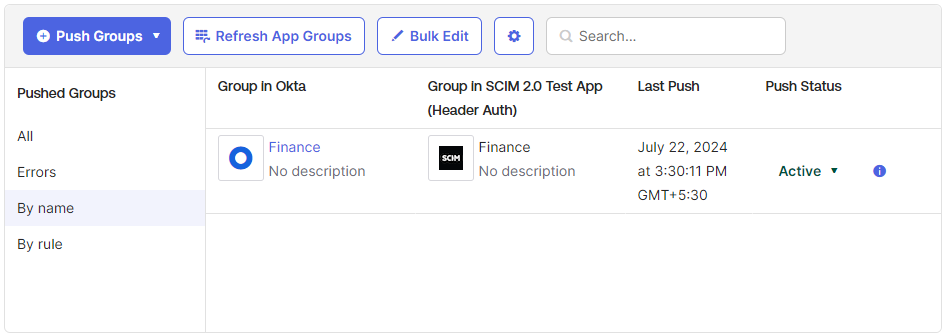
-
Click the Push Groups drop-down, select the Find groups by name.
Result
- Users in Admin > Users page
- Groups in Admin > Groups page
Next steps
- Now you are set to use Okta as the IdP to login to Forcepoint Data Security Cloud.
- Now you can enforce users from the specific username domain to get authenticated by the selected Okta IdP. To configure username domain, refer to Adding a new username domain.