Configuring a device profile for Windows or Mac devices
You can create device profiles to determine managed devices when creating policies and providing different levels of access on managed and unmanaged devices.
Steps
-
Navigate to Protect > Objects > Common Objects.
-
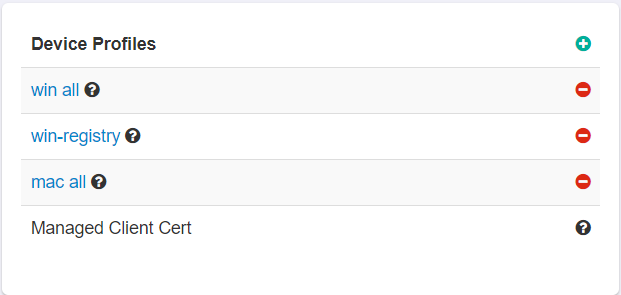
To add a new device profile, click the green plus icon available on the upper-right corner of the Device Profiles section.
Device Profile dialog opens.
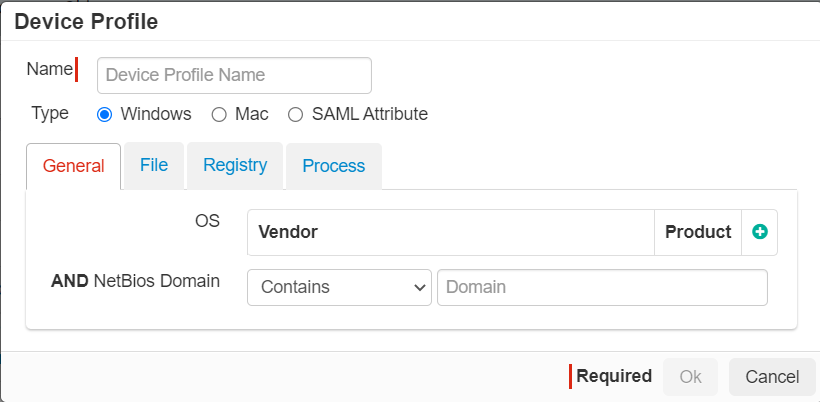
- Enter an unique Name for device profile.
- Set the criteria for what will determine if the device is managed.
-
Select Type among Windows, Mac or SAML Attribute.
To create a device profile for SAML attribute, see Configuring SAML attribute match.When you select Windows as Type, then the following tabs are available:
- General
- File
- Registry
- Process
When you select Mac as Type, then the following tabs are available:- General
- File
- Serial
- Process
-
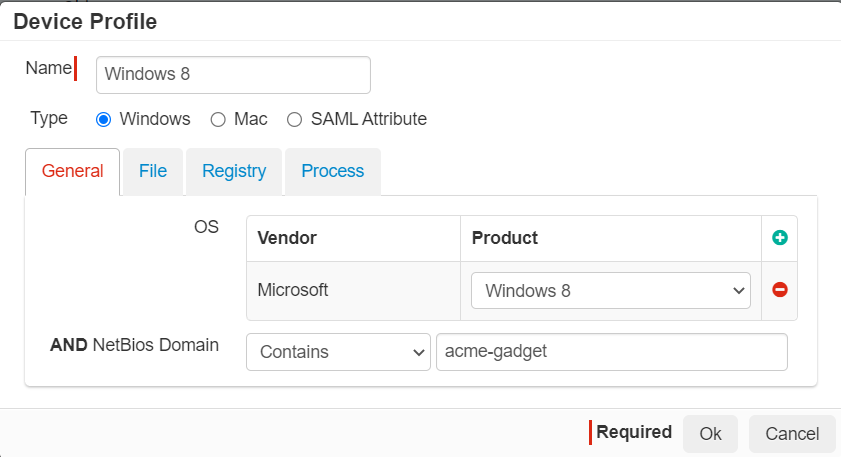
General Tab: Allows you to check the version of the Operating System.
For Windows machine, the General tab also includes the ability to enter a BIOS Domain as well to check if a device is connected to your corporate Active Directory domain.
-
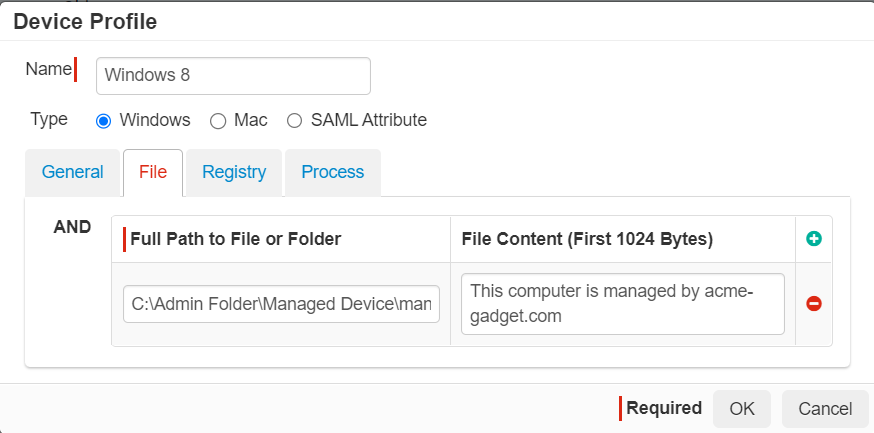
File Tab: Allows you to enter a full path to a folder or a specific file to check for its presence.
You can also be more granular to look for specific content contained within the file. Forcepoint Data Security Cloud | SSE will check the first 1024 bytes for a content match based on what you entered in the File Content field.
-
Registry: This checks for the presence of a registry key as well as the key name and optionally a string key value comparison.
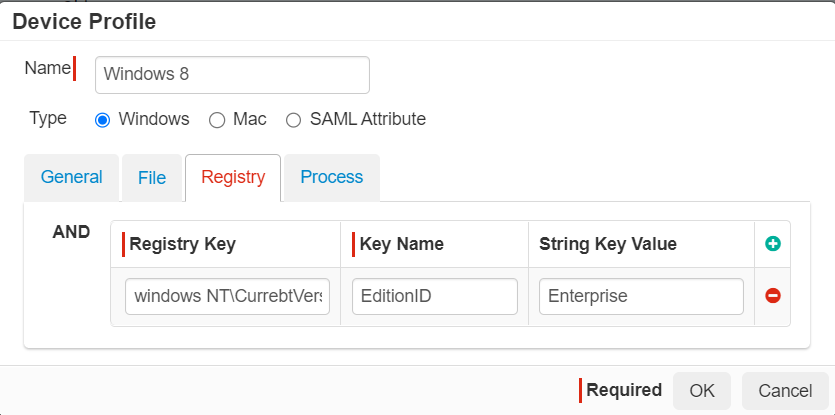
-
Serial Number: Macs have unique serial numbers, and this option will allow you to check against a list of known managed Mac machine serial numbers.
You can either manually enter the serial numbers yourself or upload a file containing all the serial numbers (each on individual lines).
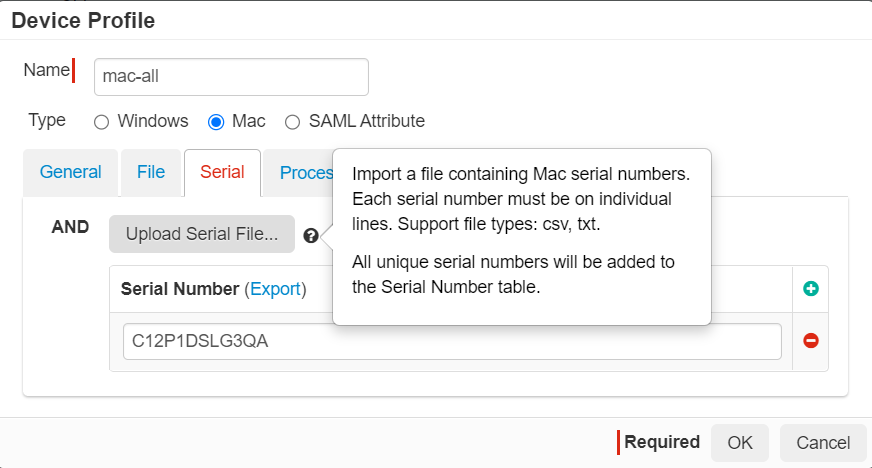
-
Process Tab: Allows you to check to ensure a particular service is running during authentication.
For example, check to ensure the devices has anti-virus software running before granting access. If the process is not running, deny access.
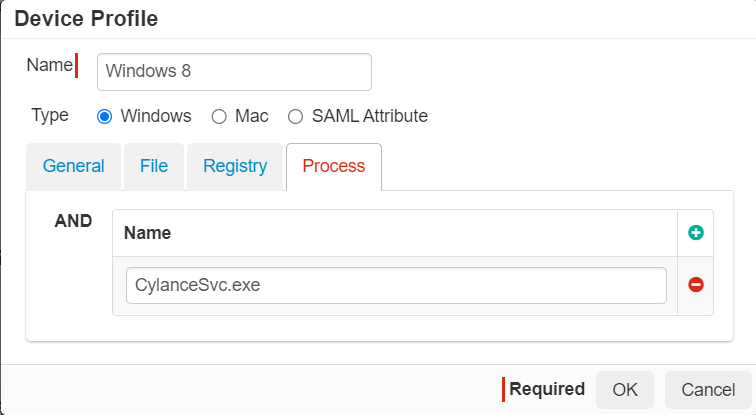
Note:When using the Process tab, enter the full name of the service. For Windows machines, you will need to include the extension of the service whereas for Mac you only need the name.
- Windows example: CylanceSvc.exe
- Mac example: CylanceSvc
For Office 365, the Forward Proxy agent can utilize post authentication to verify the device is still compliant with the policies configured Device Profile. For example, if you are requiring a process to be running to be authenticated and the process stops running, then the device will become invalid and is then logged out.
- To save the device profile, click OK.