Setting ATP scanning policy
You can protect your cloud application from malware by setting up ATP scanning using any of the ATP options that you have purchased. Setting up ATP scanning for your cloud application, is same as configuring any other data pattern with minor difference.
Protecting your cloud application with ATP scanning is quick and easy. Start by navigating to the page and locate the cloud application you wish to add ATP to. You can setup protection as a proxy policy to scan data inline and/or as an API policy for scanning data at rest.
Proxy policy
Setting up ATP scanning in proxy/inline policy for your cloud application, is same as configuring any other data pattern in a policy with minor difference. Malware scanning only applies to files during download or upload.
- Add a new policy line or modify an existing policy line. Select into the Action column to open up the Action dialog.
- In the Action dialog, you can then add a new policy line to either upload or download. Under Data Patterns look for and select the appropriate
malware data pattern you are using.When you select the malware data pattern you have purchased under Data Patterns, you will notice that:
- Block/Deny and Allow are the only available policy actions since Forcepoint Data Security Cloud | SSE will not attempt to
open or modify the file.
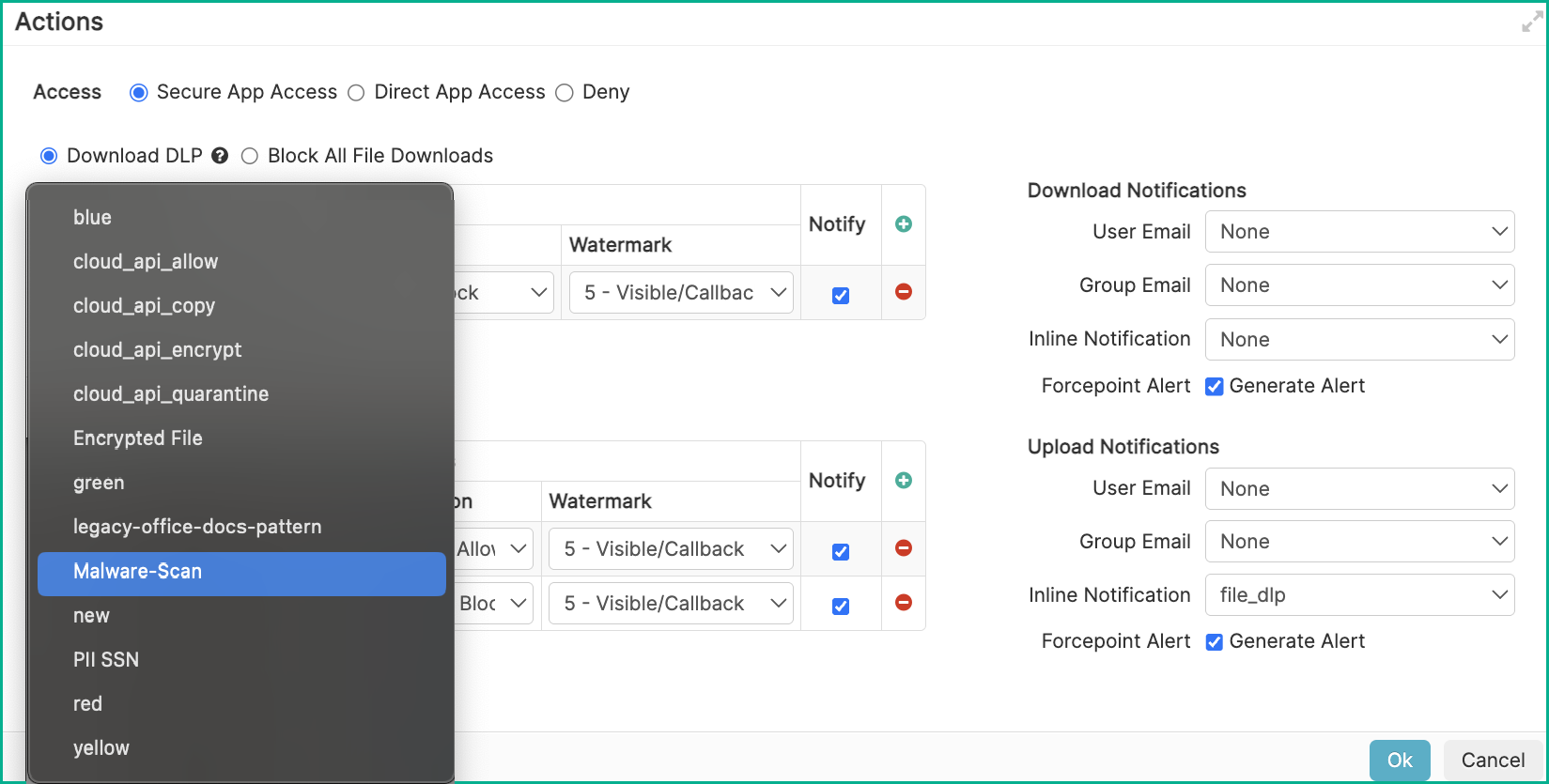
- The ActiveSync Mail (subject, Body) and Watermark fields are not supported and grayed out.
- Block/Deny and Allow are the only available policy actions since Forcepoint Data Security Cloud | SSE will not attempt to
open or modify the file.
API Policy
Setting up ATP scanning in API policy for your cloud application is the same as configuring any other data pattern in an API policy, with a minor difference.
Once the API has been set up for an application with malware patterns, you can configure policy actions for data at rest by following these steps:
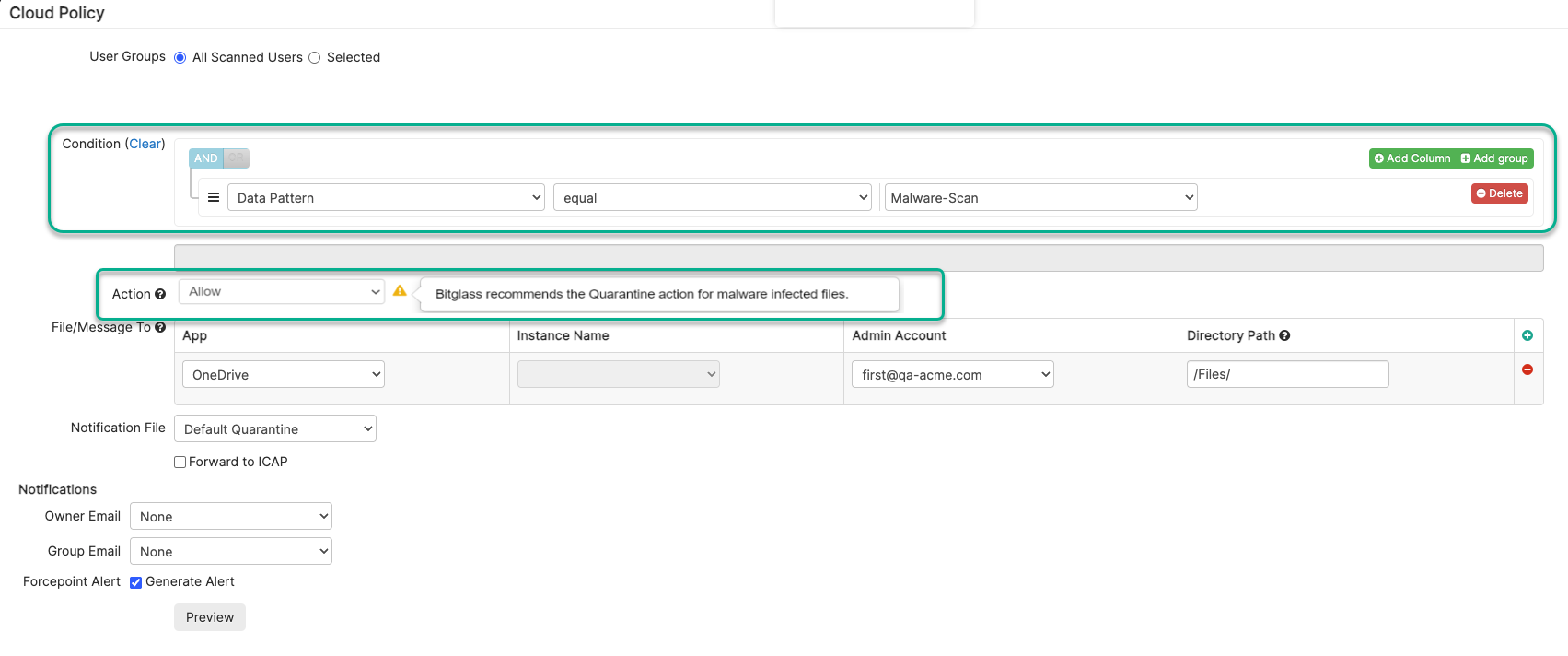
- Open the Cloud Policy dialog for the application.
- In the Conditions widget, click the Add Column option and set it to Data Pattern that equals your specified malware data pattern.
- In the Actions drop-down, select the desired policy action from the list:
- Quarantine
- Remove All Sharing
- Remove Public+External Sharing
- Remove Public Sharing
- CreateCopy
- Allow/Alert
Note: Encrypt action is not supported.Forcepoint Data Security Cloud | SSE will pop up a warning message to suggest setting the action to quarantine.
Typically when an API scan policy quarantines a file, it moves the file as-is directly to the quarantine folder. For a an ATP policy, the file will be zipped and encrypted with a default password of infected to prevent any other policy scans from attempting to open and analyze the file, thus infecting the system with malware.