Configuring SAML attribute match
Admins can configure SAML attributes to be passed from the external IdP to Forcepoint Data Security Cloud | SSE to determine if a device is managed or unmanaged.
Steps
-
Configure the external IdP to pass the SAML attribute’s name and value, for example, attribute name, Custom-managed, and its value, Trust, to Forcepoint Data Security Cloud | SSE.
The attribute name and values passed are compared against expected values setup in Forcepoint Data Security Cloud | SSE Device Profile Objects.
For example, if your external IdP is configured to check for client certs in order to determine if the device is managed or not, an Attribute of Managed with a Value of Yes or No.
- Navigate to Protect > Objects > Common Objects.
- On the Device Profiles tile, click the green plus icon.
-
On the Device Profiles dialog, select SAML Attribute as the Type and then click the green plus
icon to create a new row for attribute and value field.
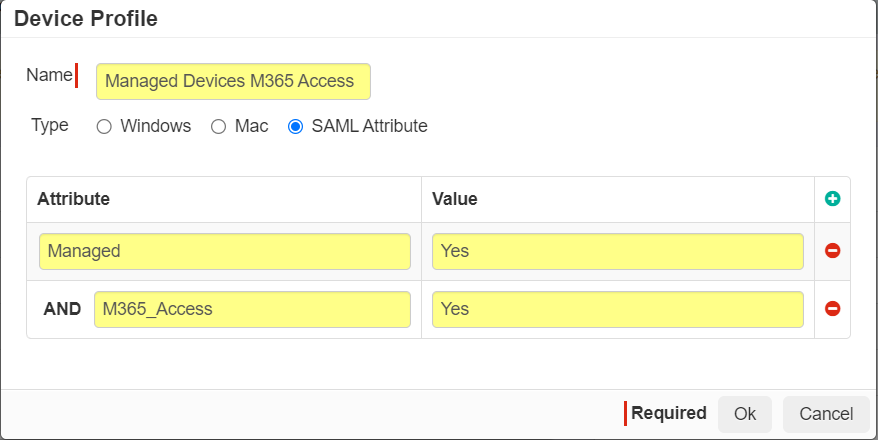
- Entering multiple attribute table items will be treated as AND conditions against one another (All SAML attributes must be present for Forcepoint Data Security Cloud | SSE to consider the device profile object to be a match).
-
These fields are highly customizable, and any attribute can be entered based on your own criteria (for example, Active Directory user attributes). See the following
examples:
- AD account attributes:
- Attribute=ExecStaff, Value=Yes
- Attribute=Contractor, Value=Yes
- Application access control
- Attribute=M365_Access, Value=Yes
- AD account attributes: