Configuring contextual access control
Each application can have multiple policy rules which are evaluated in a top down fashion until a match is found. All rule criteria must match for the actions to be applied. An implied deny rule is applied if no rules match at the end of policy evaluation. Forcepoint Data Security Cloud | SSE policies match and function in a manner similar to a traditional corporate firewall.
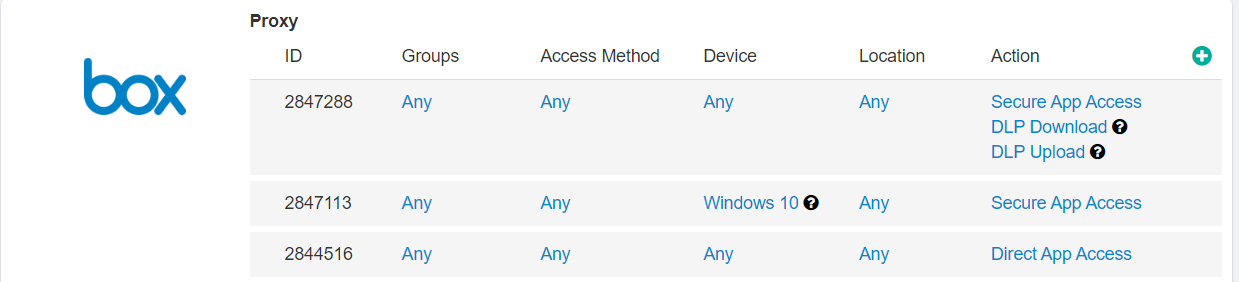
- Group: Locally defined groups or security groups and OUs pulled from active directory. Can add as many groups as are needed for the policy. Can also negate the group so
that policy line applies to everyone except the group you selected.
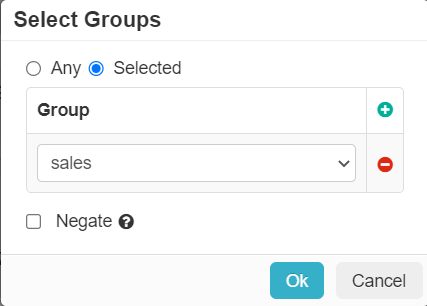
- Access Method: The access method is the method the user uses to access the application. Available access methods vary based on the application. The following table
describes the Access Methods by application. It also lists corresponding access methods used in previous releases.
Applications Access Methods Prior Access Methods Custom App Any Any, Web, Client Apps Any API Any Web Admin Portal Web, REST API Web, REST API Microsoft 365 Any, Activesync1, Basic Auth, SSO Auth Any, Web, Activesync, Legacy Outlook, Legacy Client Apps, Modern Auth Apps Google Workspace Any, Activesync2, SSO Auth Any, Web, Activesync, Client Apps Exchange3 Activesync4 Any, Activesync, Client Apps Predefined Apps (all others) Any Any, Web, Client Apps Unmanaged apps Any Any While adding a new proxy policy, Any is selected by default unless Any is not a valid option for that Application.
The prior Access Method remains active with the old behavior until the access method is updated in the policy rule. When you click a prior access method, a pop-up to the one below appears asking you to migrate to a new access method:
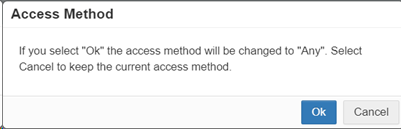 Note: Secure access method + Managed Client Cert in not supported for client apps but supported for Web access. When selecting Secure access for SSO Auth + Managed client cert option, client apps like OneDrive/Outlook will be blocked.
Note: Secure access method + Managed Client Cert in not supported for client apps but supported for Web access. When selecting Secure access for SSO Auth + Managed client cert option, client apps like OneDrive/Outlook will be blocked. - Device: Set contextual access controls based on the users device (OS/user agent, managed vs unmanaged, etc).
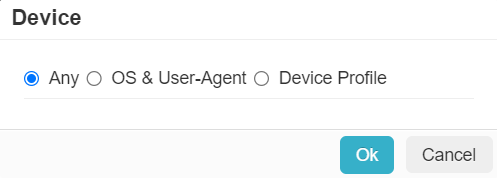
- OS & User-Agent: Allows you to match from a predefined set of common operating systems and/or User-Agent Strings.
- Device Profile: Allows you to match on Device Profiles which are managed under .
- Location: This column allows you to restrict or control where a user is accessing the cloud application from (either geographic location or IP).
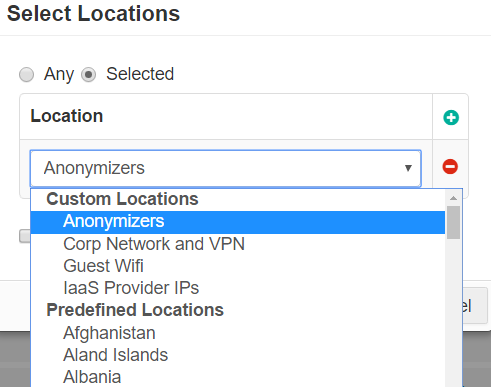
- Predefined locations include a list of countries. Country match is done using a geo-IP lookup to match source IP address to country.
- Custom Locations can be configured under . To configure a custom region, enter an IP address, subnet, or IP ranges on individual lines. Remember to use external internet facing addresses (for example, 67.228.234.100/30). Custom locations also include predefined locations that are not based on countries (for example, Anonymizers and IaaS Provider IPs). These locations are managed and updated by Forcepoint Data Security Cloud | SSE.
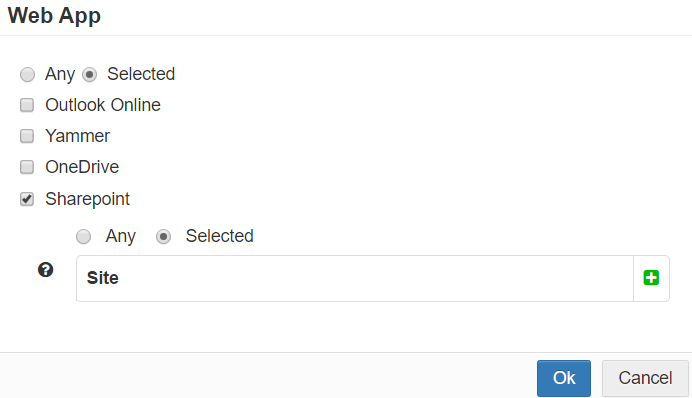
- Web App (M365 Only): Allows you to deny user access to specific web apps inside of O365.
You can keep as Any (all web apps) or select specific apps.
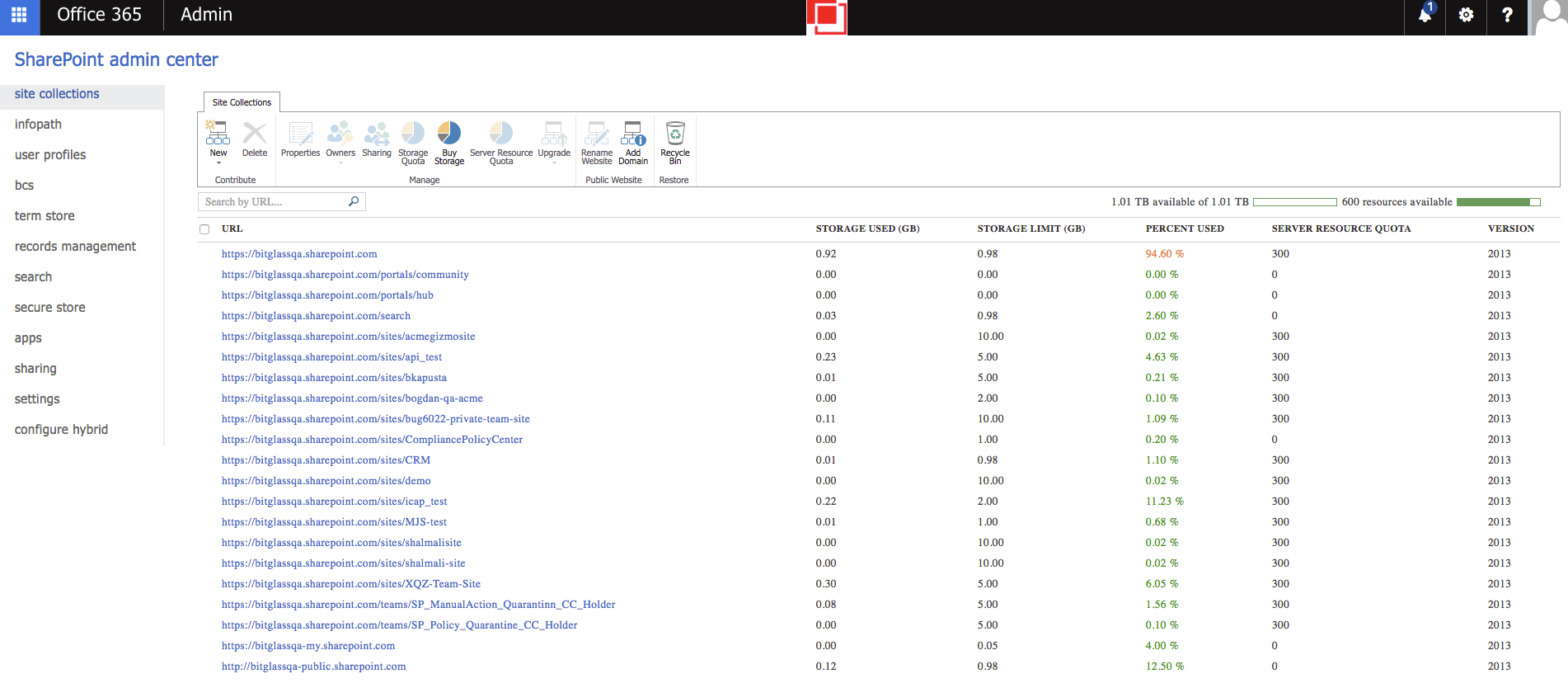
For Sharepoint sites, you can enter the URL for any top level site. To find a list of all top level site URLs, navigate to your Sharepoint Admin Center and select site collections.
 Note:
Note:- Sharepoint document libraries and folders are not supported.
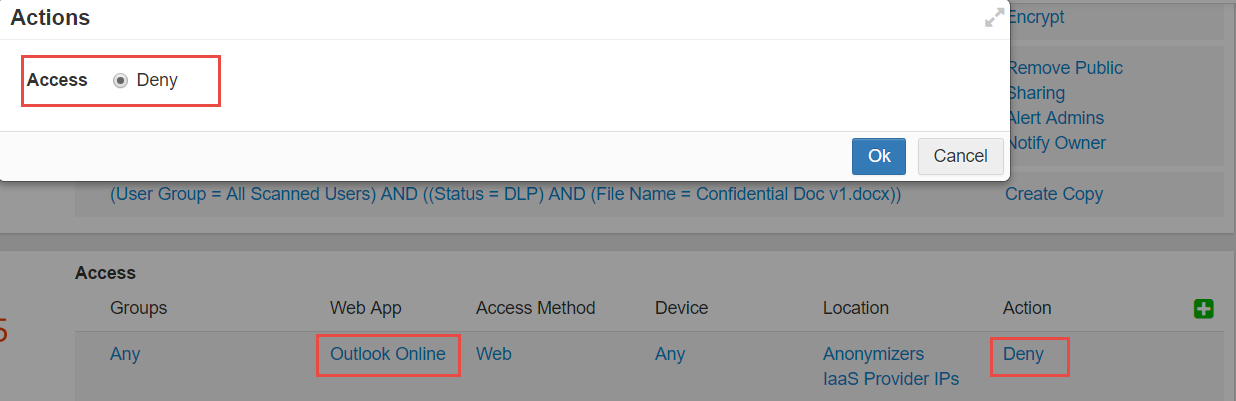
- Specifying a Web App (except for Any) will only allow for a Deny action. This is due to the web apps pulling resources
from different domains unrelated to the actual URL causing other Office 365 locations to be accessible that are not intended to be accessed based on the policy setup.
- Action: This column will allow you to control what policy action is applied to the user based on the above policy configuration. You can set them to Secure App Access
(sending them the proxy), Direct App Access (to send them direct and bypass Forcepoint Data Security Cloud | SSE), or Deny. You can also set them to Isolate (to isolate a user session when
browsing suspicious or risky websites) for SWG Content Policies if the RBI license is enabled for the tenant. Refer to the Configuring proxy policy actions for more information on
configuring these policy options.Note: It is not recommended to set a policy line with a specific region location and action set to Direct App Access. Policy lines are checked and applied during initial login. This means a user who is only allowed Direct App Access when within a specific region can just change location after login since they will be sent direct to the app and Forcepoint Data Security Cloud | SSE will no longer be monitoring their connection.