Configuring MFA login policy
Administrator can enforce an Multi-Factor Authentication (MFA) check after a user authentication before granting access.
Steps
- Navigate to Protect > Policies page.
-
On the Login Policy tile, click the Add Action drop-down and then select the Multi-Factor Authentication action.
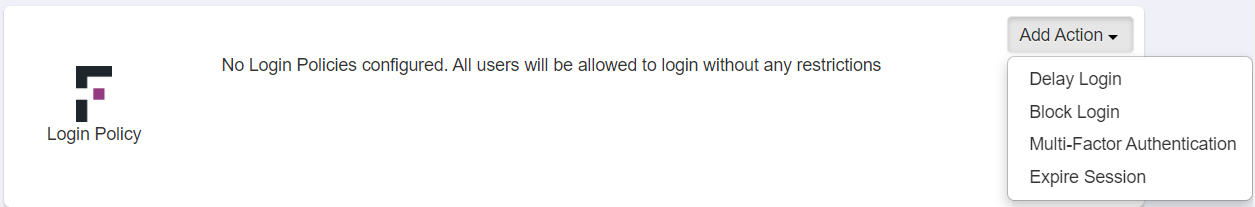
A default policy gets created for the Multi-Factor Authentication Login.

You can either Save the policy or you can edit the default policy variables.
-
To specify which Groups the action applies to:
Groups can be locally defined groups, security groups and OUs pulled from active directory.Note: By default, Any is selected which means policy is applicable to all groups.
Available options are:
- Any
- Selected
- Click the Any value to open the Select Groups dialog box.
-
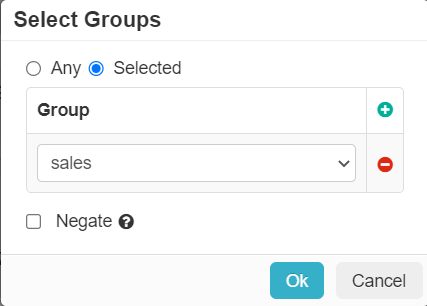
To limit the policy to selected groups, click Selected option.
-
To add a group, click the green plus icon and then select the group from the drop-down you wish the action to apply to.
You can add as many groups as needed for the policy.
- Select the Negate checkbox to apply policy line to every group except the group you selected.
- To save the selected group(s), click Ok.
-
To specify which Device the action applies to:
Note: By default, Any is selected which means policy is applicable to all devices including unmanaged devices.
Available options are:
- Any
- OS & User-Agent
- Device Profile
If you want to select common operating systems and/or User-Agent Strings:- Click the Any value to open the Device dialog box.
- Select OS & User-Agent option.
-
Select the applicable operating systems.

Available options are Apple iOS, Apple Mac OS X, Google Android, Google Chrome OS, Microsoft Windows Phone, Microsoft Windows PC and Other OS. -
To limit the policy to matches of selected operating systems along with any user-agent strings, click the green plus icon and then enter the string(s).
You can add as many user-agent strings as needed for the policy.
- Select the Negate checkbox to apply policy line to every device except the device you selected.
- To save the selected device(s), click Ok.
If you want to select device profile:- Click the Any value to open the Device dialog box.
-
To limit the policy to selected device profiles, click Device Profile option.

-
To add a device profile, click the green plus icon and then select the device profile from the drop-down you wish the action to apply to.
You can add as many device profiles as needed for the policy.
- Select the Negate checkbox to apply policy line to every device profile except the device profile you selected.
- To save the selected device profile(s), click Ok.
-
Apply specific actions when a user is accessing from certain Location:
Available options are:
- Any
- Selected
- Click the Any value to open the Select Locations dialog box.
-
To apply specific actions when a user is accessing from certain locations, click Selected option.

You can restrict or block users entirely from unsafe or untrusted locations and restrict or control where a user is accessing the cloud application from (either geographic location or IP).
-
To select a location, click the green plus icon and then select the location from the drop-down you wish the action to apply to.
You can add as many locations as needed for the policy.
- Select the Negate checkbox to apply policy line to every location except the location you selected.
- To save the selected location(s), click Ok.
-
Select a unique Behavior at login that will trigger the policy action.
Available options are:
- Any
- Selected
-
Click on the default behavior to open Behavior dialog box.

- To trigger the policy action based on specific behavior, click Selected option.
- To trigger the policy action when a new device is detected that they have not used before, select New Device Detected checkbox.
-
To trigger the policy action when a user logs in to protected applications from distant locations within a short amount of time, select Suspicious User
Locations checkbox.
For example, if the user login to M365 in California and then 5 minutes later log in to Salesforce from New York.
- To trigger the policy action when users, with risk score greater than specified number, login to the Forcepoint Data Security Cloud | SSE portal, select the User Risk Score > checkbox and then enter a number.
- To save selected details, click OK.
-
Select a specific Time Range (days of the week or workday hours) for when the action will apply.
Available options are:
- Any
- Selected
-
Click on the default time range to open Time Range dialog box.

You can select Any to apply action any time and day or you can select Selected to prevent users (especially contractors) from having accessing beyond work hours and days.
Note: When you select Selected, approved start time, end time, and days are shown for region. - Select the Start time.
- Select the End time.
-
Select the applicable Day(s).
Available options are Sun, Mon, Tue, Wed, Thu, Fri and Sat.
- To save selected details, click OK.
-
Select the Action to be taken when a policy is met.
-
Click on the default action to open Action dialog box.
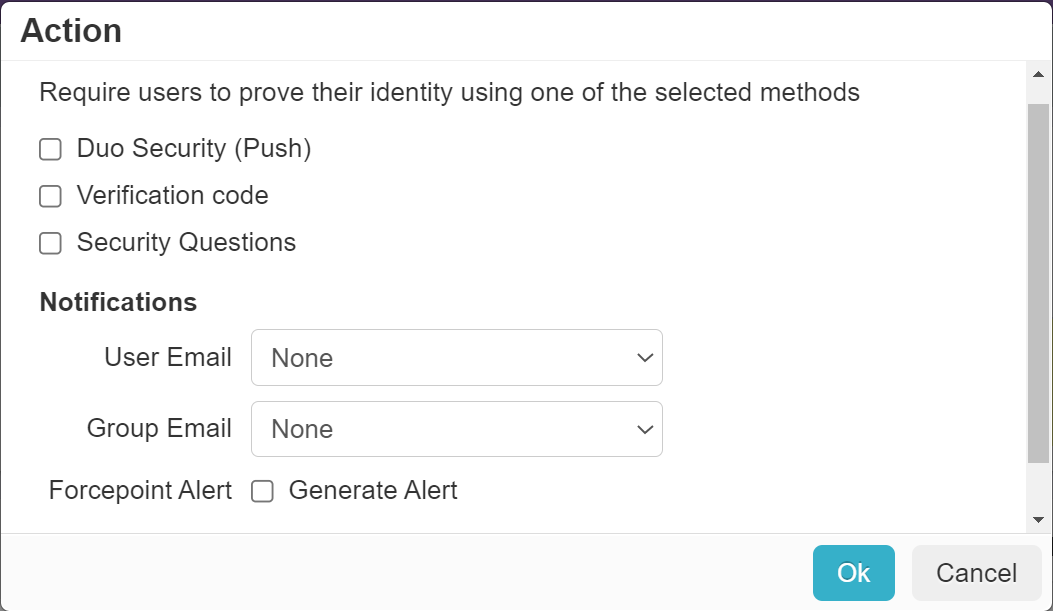
- To enforce duo security (Push) MFA check after a user authentication before granting access, select Duo Security (Push) checkbox.
-
To enforce verification code MFA check after a user authentication before granting access, select Verification Code checkbox.
By default, Verification Code is selected.
- To enforce security questions MFA check after a user authentication before granting access, select Security Questions checkbox.
- To notify about the MFA check to user, select the appropriate User Email.
- To notify about the MFA check to group, select the appropriate Group Email.
-
To generate a Forcepoint alert, select the Generate Alert checkbox.
Admin can view Forcepoint alerts from Analyze > Alerts page.
- To save selected details, click OK.
-
Click on the default action to open Action dialog box.
- To save the updated policy, click Save.