Alert details
Use the Alert details panel to view details about a specific alert.
When you click on an alert from the alerts panel, the Alert details panel displays with additional information about the alert which may include information like the policy rule, and/or IoB triggered by the selected user activity and details about the activity, along with the monitored channel and specific action taken. The top toolbar of the Alert details, includes the date and time, device, domain, operating system, and IP address of the selected activity.

- 1
- Endpoint details: Displays the endpoint details if relevant such as: the agent version installed, policy version, IP address etc.
- 2
- Status
- 3
- Assignee
- 4
- Severity: Indicates the impact of the user actions to the organization.
- 5
- Matched rule: Displays the matched policies and rules.
To select specific rules for filtering:
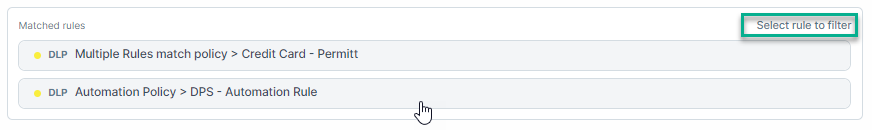
To clear rule filtering:
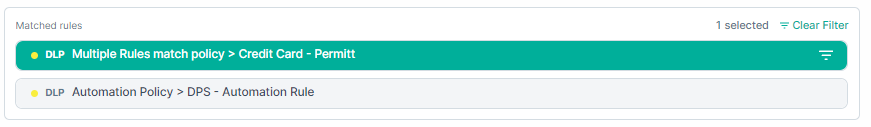
- 6
- Incident history: Shows all actions related to an Alert in chronological order. Includes the status changes, severity changes, assignment changes and any
associated comments.
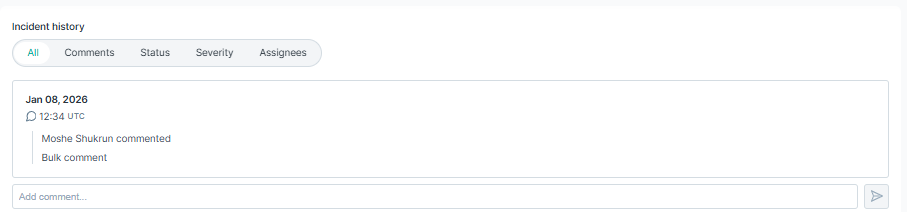
- 7
- Forensics: Displays additional information – metadata and the forensic artifacts (if applicable) captured as part of the Alert. This can include the
precise values that triggered the Alert, the number of matches against different classifiers, file name and file size information and a copy of the actual file or email if the
Alert relates to a DLP Policy where the policies action plan was configured to capture forensics.
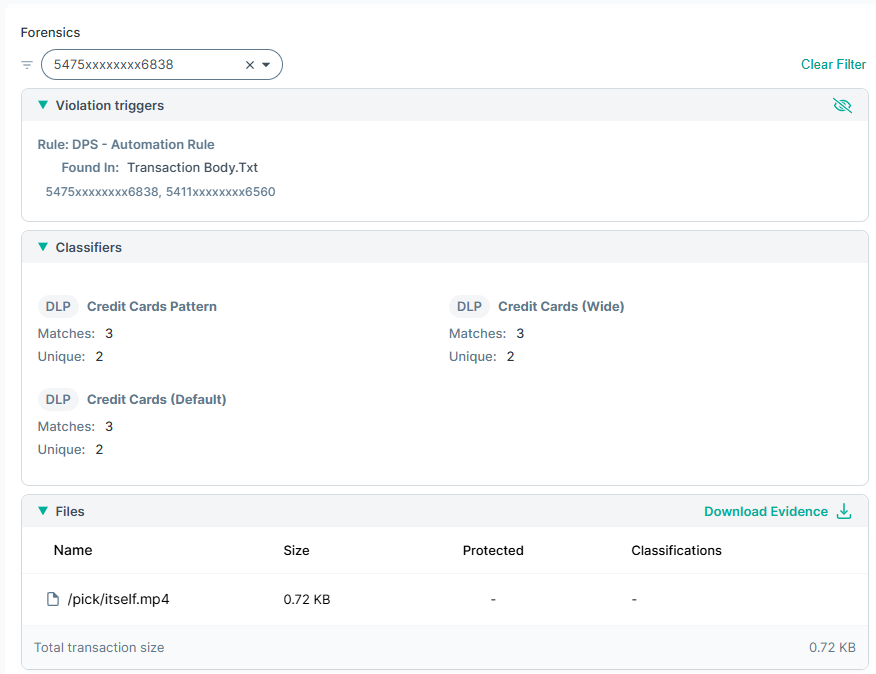
Following detailed information is displayed under the Forensics section:

- a: Violation Triggers: Displays the precise values that triggered the Alert. Values are displayed relative to the DLP Policy and DLP
Policy Rule. Only the first 500 triggers or 500 MB for the Alerts are displayed.
- b: Hide sensitive data: The precise values are always masked. Administrators with the full admin or Investigator role can toggle the
 icon to unmask and mask the sensitive data. Administrators with the analyst role cannot
unmask the sensitive data.
icon to unmask and mask the sensitive data. Administrators with the analyst role cannot
unmask the sensitive data. - c: To display the full list of triggers click the Show More icon.
Note: Violation triggers are not available for alerts that were generated before the forensic feature was introduced. - b: Hide sensitive data: The precise values are always masked. Administrators with the full admin or Investigator role can toggle the
- d: Classifier: Policies use content classifiers to describe the data that is being protected. The classifiers that triggered the Alert are displayed under the Classifier section.
- e: Files: The list of file(s) that contain sensitive information.
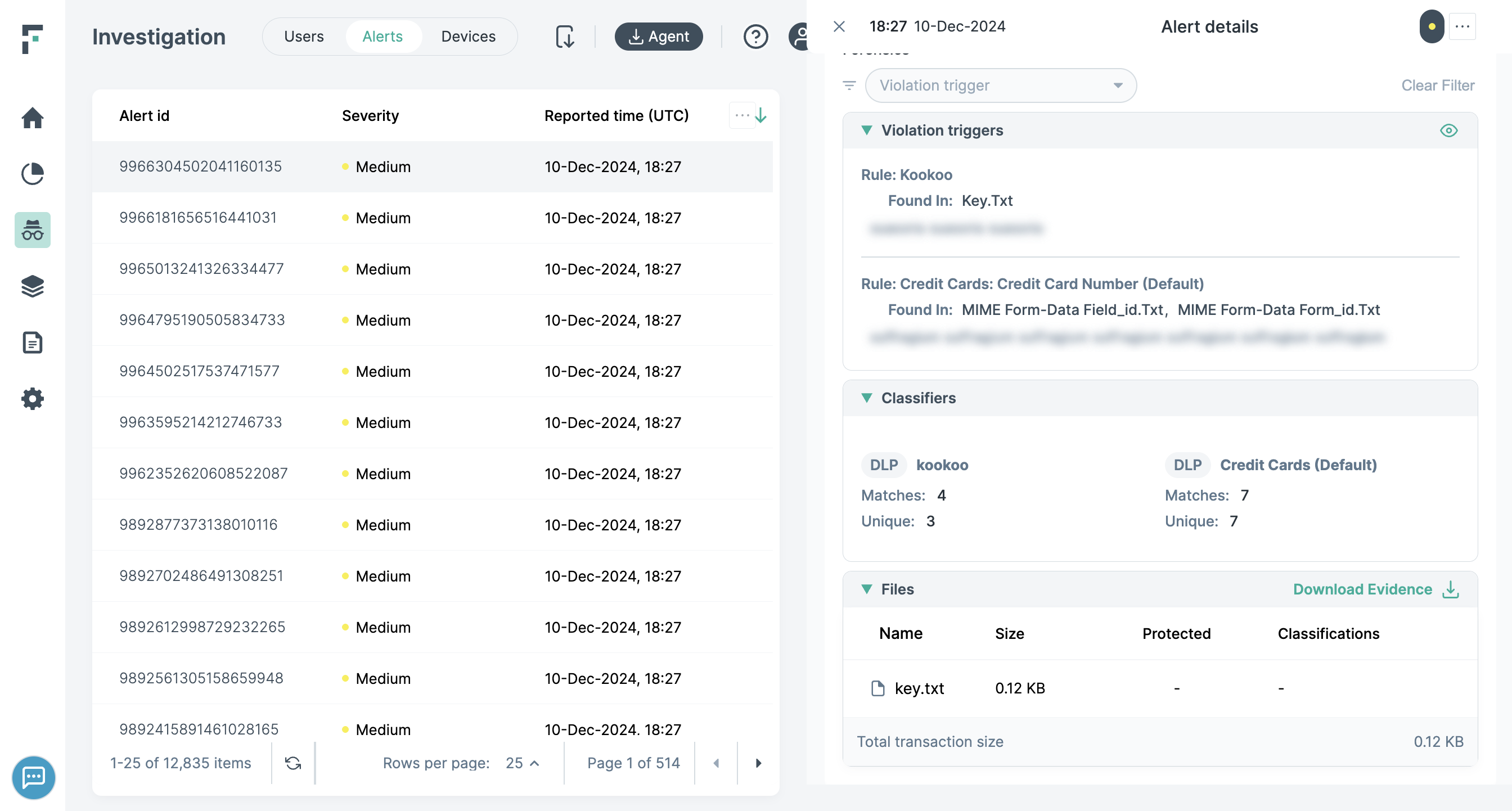
- f: The Download Evidence action allows you to download all available evidence. Regardless of the channel, the evidence is wrapped in an .eml file that contains the files included in the transaction as well as the transaction body (where a body is present). The evidence file can be opened by a standard email client.
- a: Violation Triggers: Displays the precise values that triggered the Alert. Values are displayed relative to the DLP Policy and DLP
Policy Rule. Only the first 500 triggers or 500 MB for the Alerts are displayed.
- 7
- Clicking
 icon gives following options:
icon gives following options:
If you select the Copy Alert ID option, it copies the alert ID to clipboard.
if you select the Print as PDF option, it exports the complete alert details to a PDF.
For users logged in as analyst, the Details field will be anonymized.