Data Mapping
Data mapping (Security Posture Policy Controls) serves as building blocks for creating the framework for the data asset inventory. Here you define the fields that will be available in the Data Asset Inventory, allowing data owners to assign metadata tags to their critical data.
It gives organizations the ability to define additional tags or attributes such as:
- Retention period
- Business owner
- Regulatory scope
- Review status
- Project name
Note: You are limited to only one data mapping configuration, meaning all departments will have the same security posture policies. Therefore, design your data mapping to be generic enough to be
used by all departments.
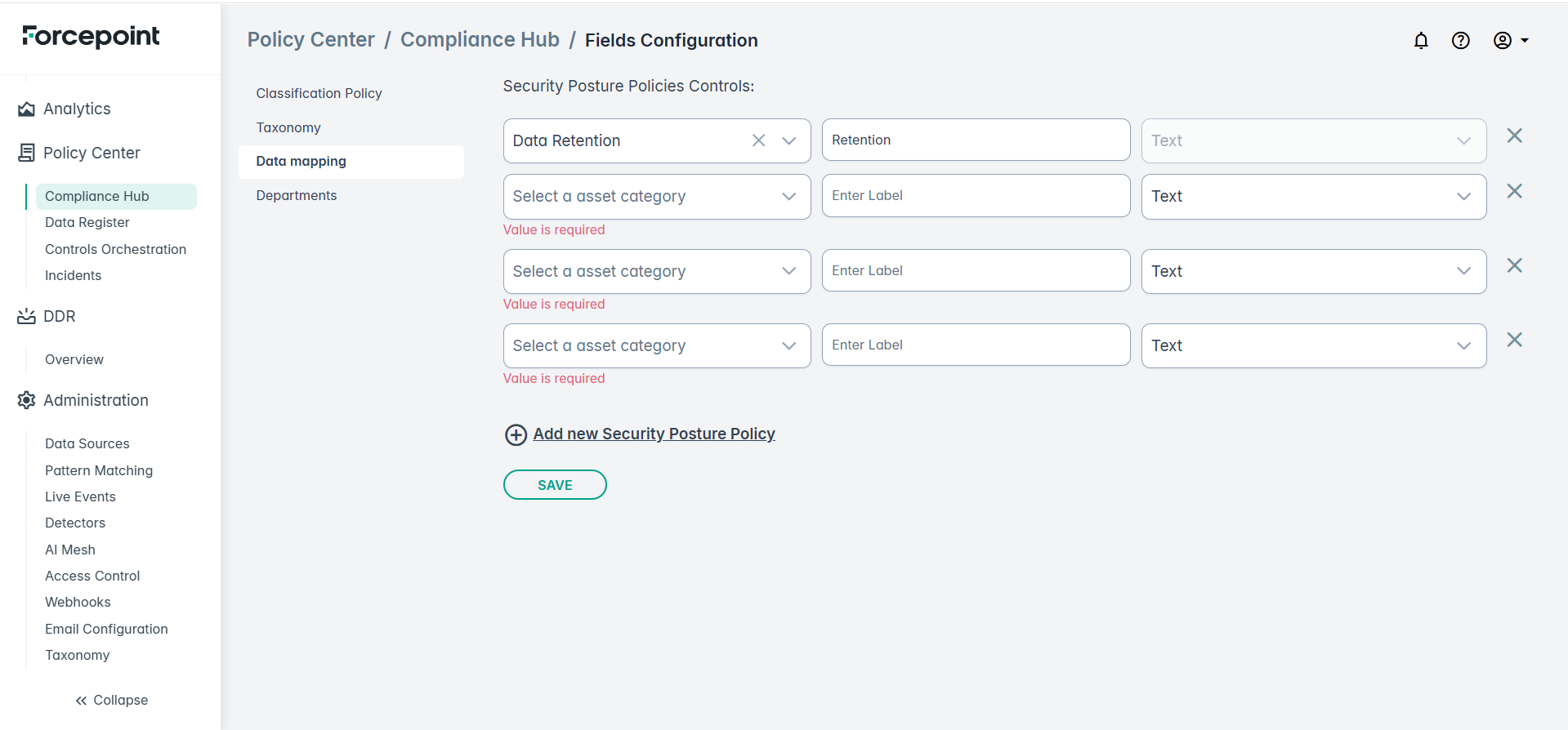
Following fields are important to note:
- Category: This is a name used to group multiple security posture policies.
- Label: This is a text string visible in the Data Asset Inventory, used to describe the purpose of the policy.
- Control: This dictates the type of information used in the Data Asset Inventory. The values are currently Informational and include:
- Text: Creates a free-form text field.
- Yes/No: Creates a Yes/No drop-down menu.
- Select: Adds a selection menu where you can choose from twelve options aligned with common data governance frameworks.
Adding new Security Poster Policy Controls
- Navigate to .
- Click the Add new Security Posture Policy Control button. This inserts a new rule.
- You will need to configure three settings in the rule. Asset category, label, and select the information type. The asset category is reusable, so you need to create each category only once.
- Click Save to save the changes.