Azure Subscription ID, Resource group and connection strings
Steps
- Login to Azure Portal.
-
If there are multiple tenants to choose from, use the Settings icon in the top menu to switch to the tenant which needs to be registered to the application from the Directories +
subscriptions menu.
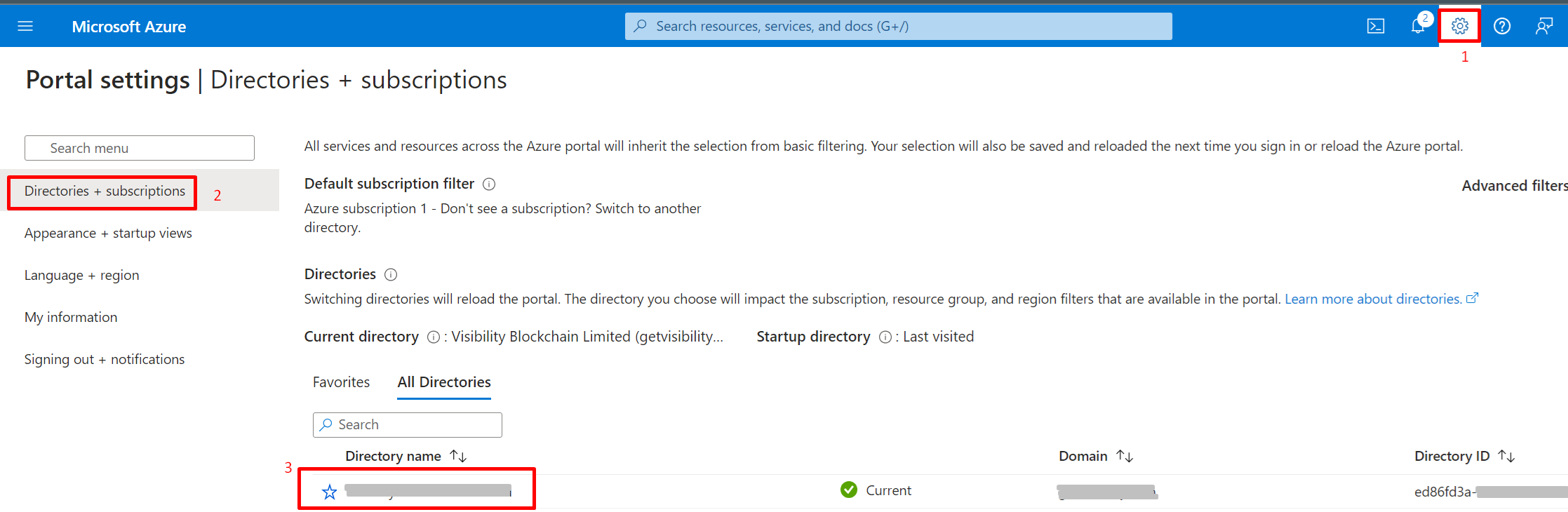
-
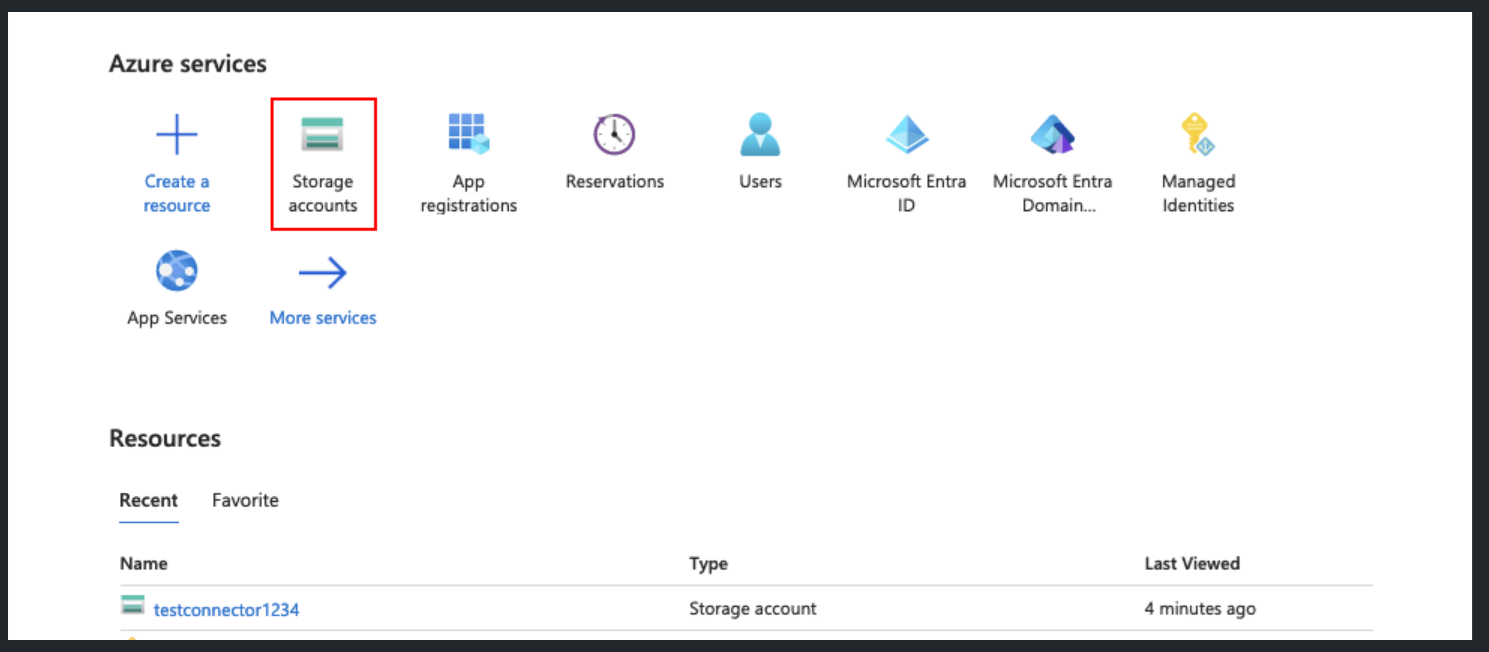
Browse to Storage accounts and select the account to be scanned.
-
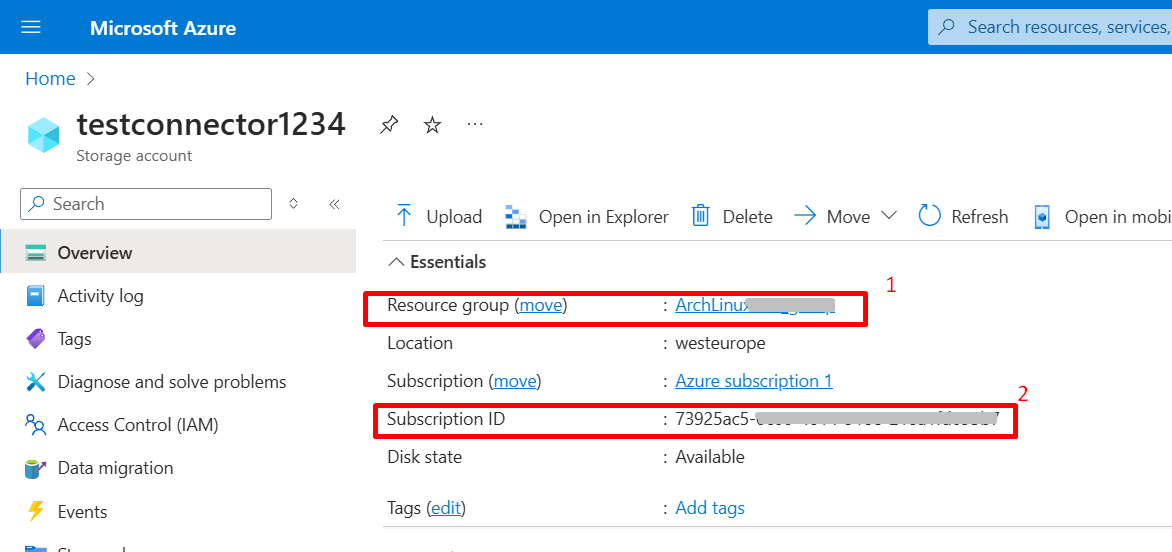
Once the storage account is selected, note the Resouce group and Subscription ID values in the Overview page.
-
Navigate to Security + networking -> Access keys on the left menu and click on Show on the Connection string.
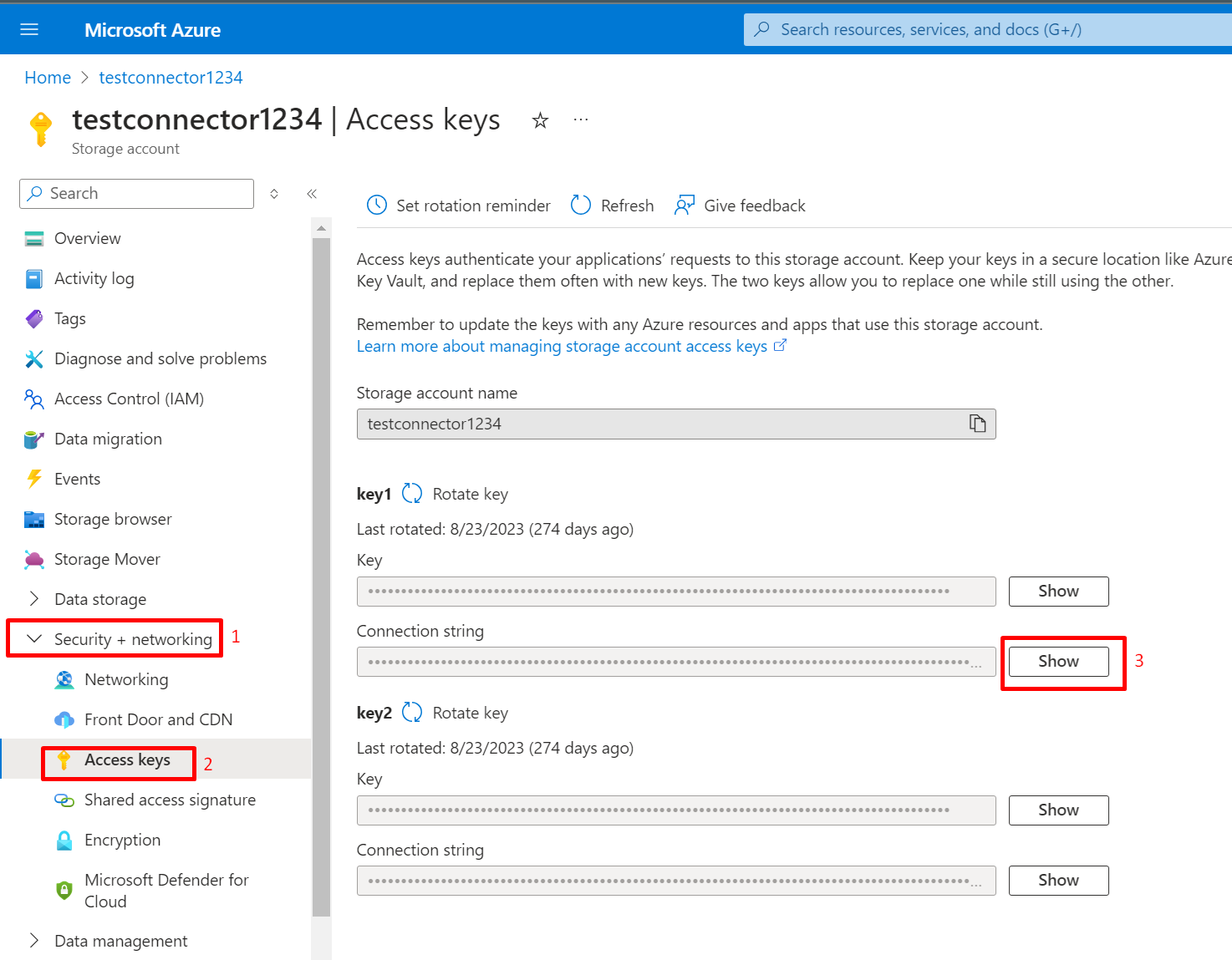
- Copy this Connection string value.
-
Access Control (IAM) Role assignment - there are 2 options, one is to assign a built-in role, the other is to create and assign a custom role. Using a built-in role is an easier
option to configure, while a custom role may be preferred to ensure least privileges assignment for increased security.
- Option 1: In the storage account, go to Access Control (IAM) and check on either Storage Blob Data Owner or Data Contributor role to assign the role to the blob storage. (Per Microsoft's documentation the Data Contributor role is the least privileged, built-in role for Listing Containers).
-
We also need to assign Reader role to the azure app created in the first step.
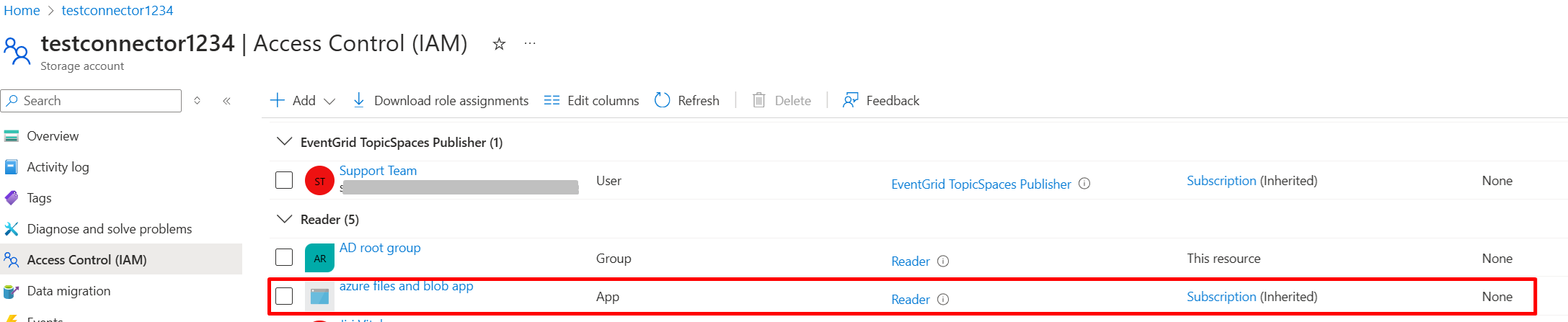
-
Save the changes.
-
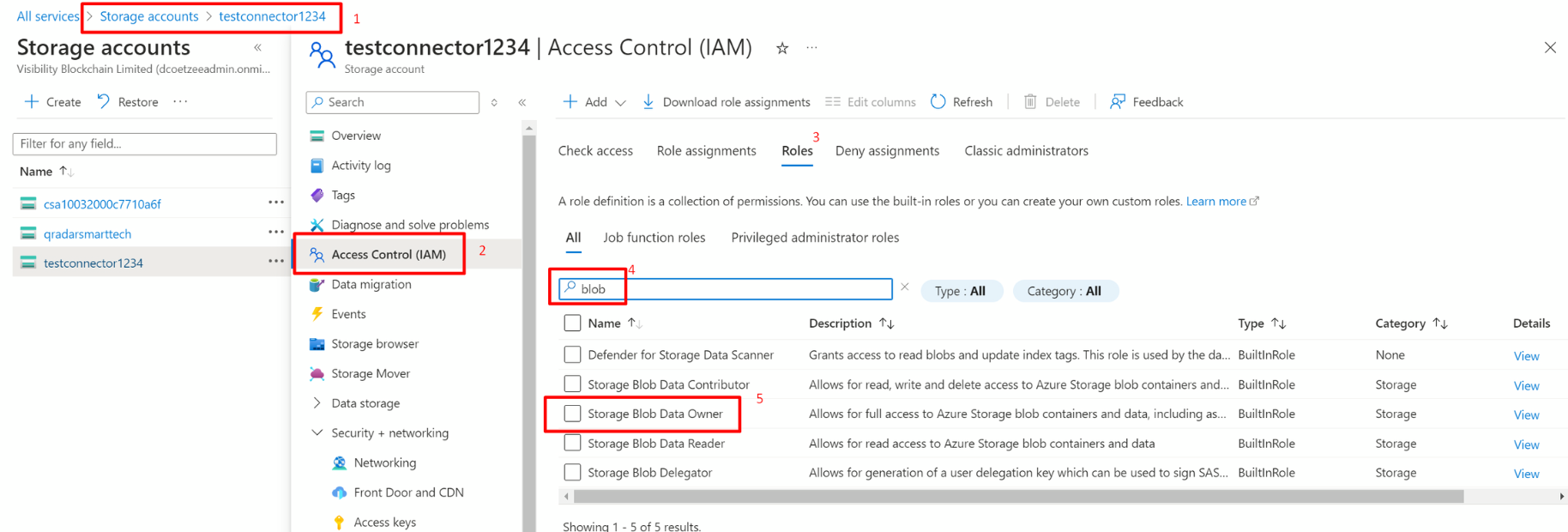
Option 2: This option creates a custom role and assigns the same permissions as the Data Contributor role, except for the delete permissions. In the Blob storage account,
go to Access Control (IAM) and click Add to create a new role. Name the role with a preferred name and choose the following actions below to assign to this custom role.
Select this custom role for the blob and save changes.
Microsoft.Storage/storageAccounts/blobServices/containers/read (Return a container or a list of containers) Microsoft.Storage/storageAccounts/blobServices/containers/write (Modify a container's metadata or properties) Microsoft.Storage/storageAccounts/blobServices/generateUserDelegationKey/action (Returns a user delegation key for the Blob service) Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read (Return a blob or a list of blobs) Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write (Write to a blob) Microsoft.Storage/storageAccounts/blobServices/containers/blobs/move/action (Moves the blob from one path to another) Microsoft.Storage/storageAccounts/blobServices/containers/blobs/add/action (Returns the result of adding blob content) -
We also need to assign Reader role to the azure app created in the first step.
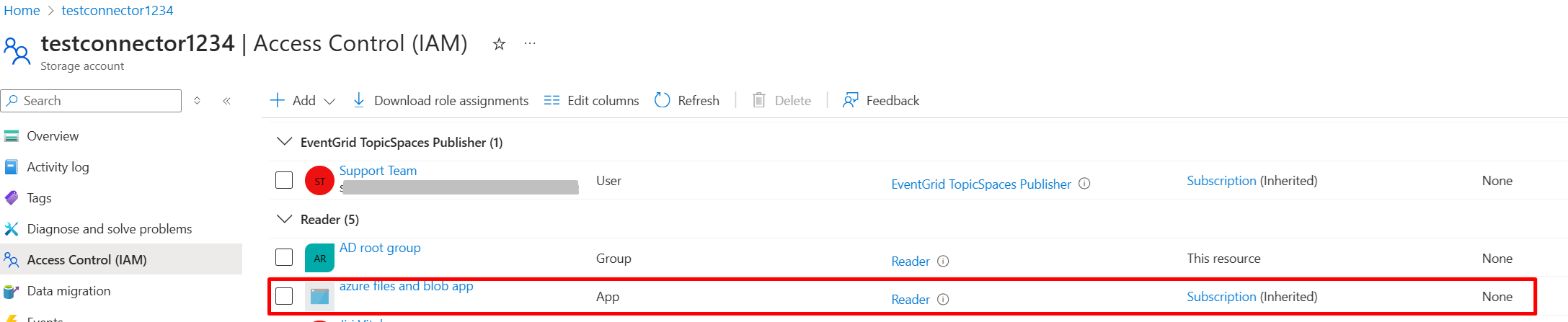
-
Real Time Events Monitoring (Streaming) Permissions: To enable "Real Time Events Monitoring (Streaming)", the following additional Azure permission roles are required:
EventGrid Data ContributorEventGrid EventSubscription ContributorEventGrid TopicSpaces Publisher
Assign these roles using Access Control (IAM) in the Blob storage account, similar to the steps mentioned above for assigning the
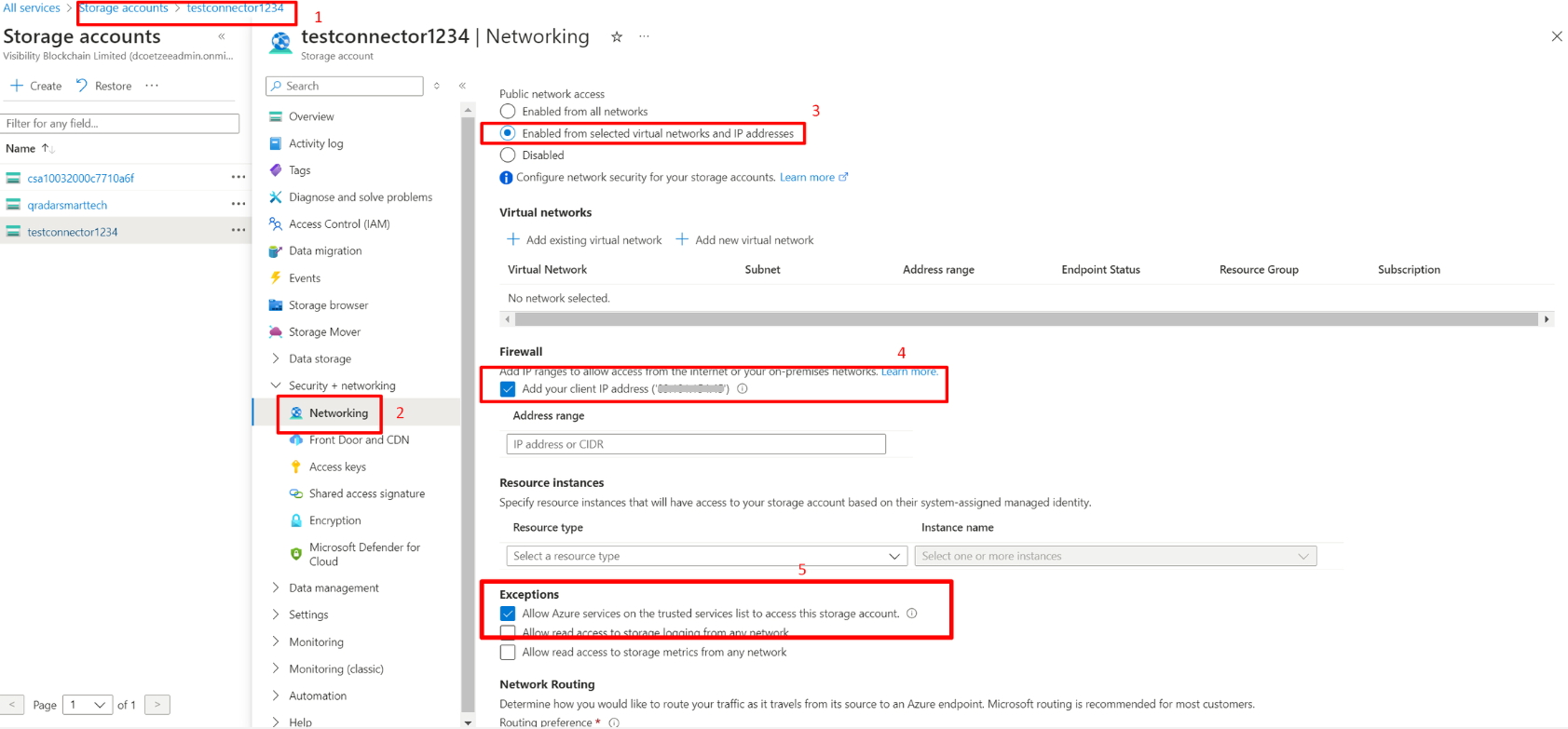
Storage Blob Data OwnerorData Contributorrole. - Next, in the Networking tab, under Public network access, select "Enabled from all networks", or "Enabled from select virtual networks and IP addresses". If the latter was chosen, then under Firewall section add the IP address range for the DSPM server.
-
Enable "Allow trusted Microsoft services to access this storage account" and Save the changes.
*** Firewall rules must also be in place to allow the DSPM server to connect to https://(mystorageaccount).blob.core.windows.net