Deploying Forcepoint Data Security Cloud | SSE SmartEdge Agent on macOS via JAMF Pro
Steps to deploy the SmartEdge agent to wider audience connected to JAMF Pro for macOS.
Steps
-
Follow the steps below to push and trust certificates via JAMF to target user devices running macOS:
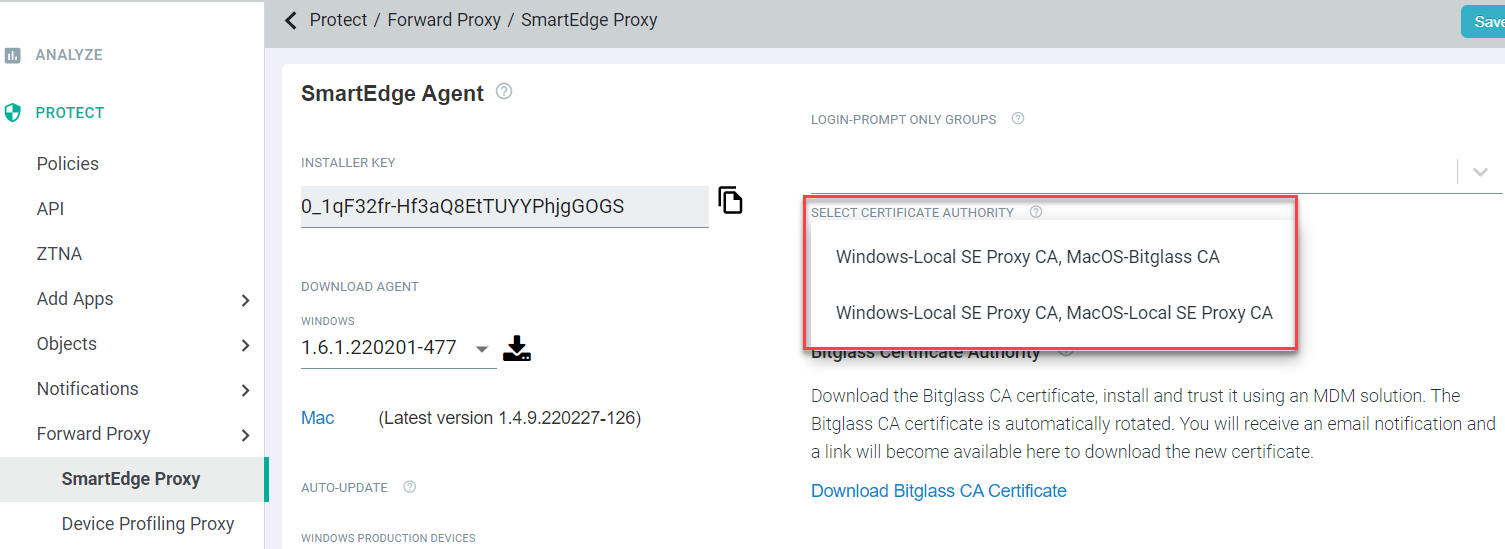
- In the Forcepoint Data Security Cloud | SSE portal, navigate to Protect > Forward Proxy > SmartEdge Proxy.
-
From the Select Certificate Authority drop-down, select one of the option based on which certificates will be handled by SmartEdge agent.
You will notice both options mention Windows, but the Windows options are the same (that is the SmartEdge just generates a client cert that is trusted/used).
- Windows-Local SE Proxy CA, MacOS-Local SE Proxy CA: Should be used with older versions of macOS before Big Sur and will use the SmartEdge generated client cert.
- Windows-Local SE Proxy CA, MacOS-Bitglass CA: Should be used with MacOS Big Sur or new version devices. This will then give you the option to
download the Bitglass root CA that can be pushed to devices and will auto generate client certs that are automatically trusted on the device.
-
After selecting Windows-Local SE Proxy CA, MacOS-Bitglass CA, click the Download Bitglass CA Certificate link from the
Bitglass Certificate Authority section.
Download and save the certificate somewhere easily accessible.
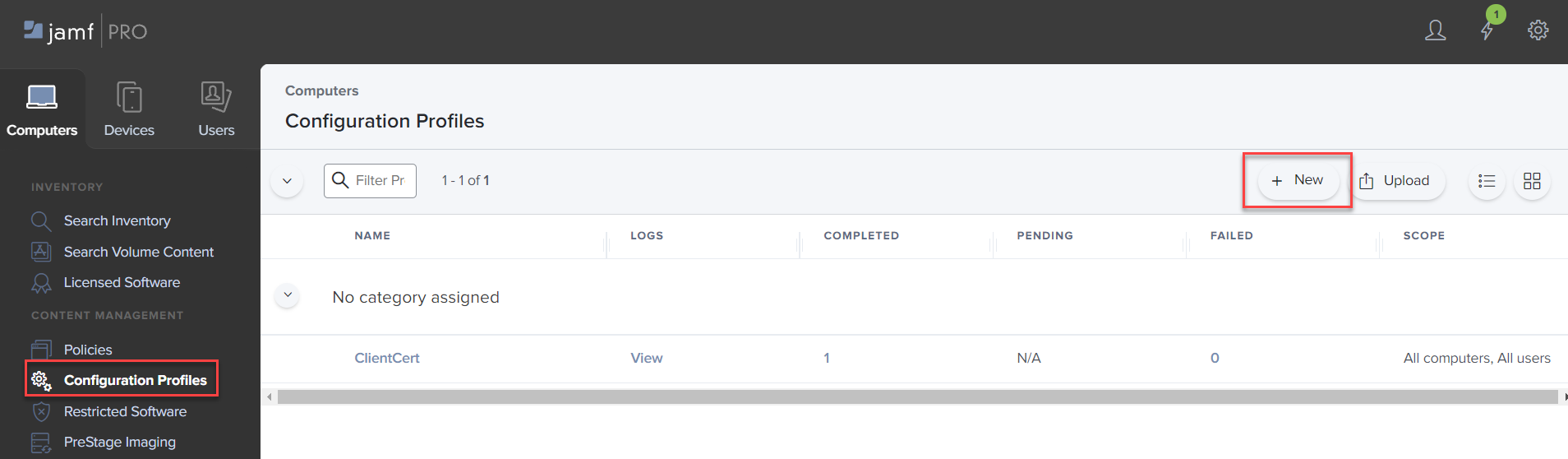
- Open a new window and login to Jamf admin portal.
- Click on the Computers.
-
On the left column, select Configuration Profiles and then click New to create a new profile.
-
Provide a name for your profile and optionally a description for future reference, leave most options as default but change Distribution Method to
Make available in Self Service.
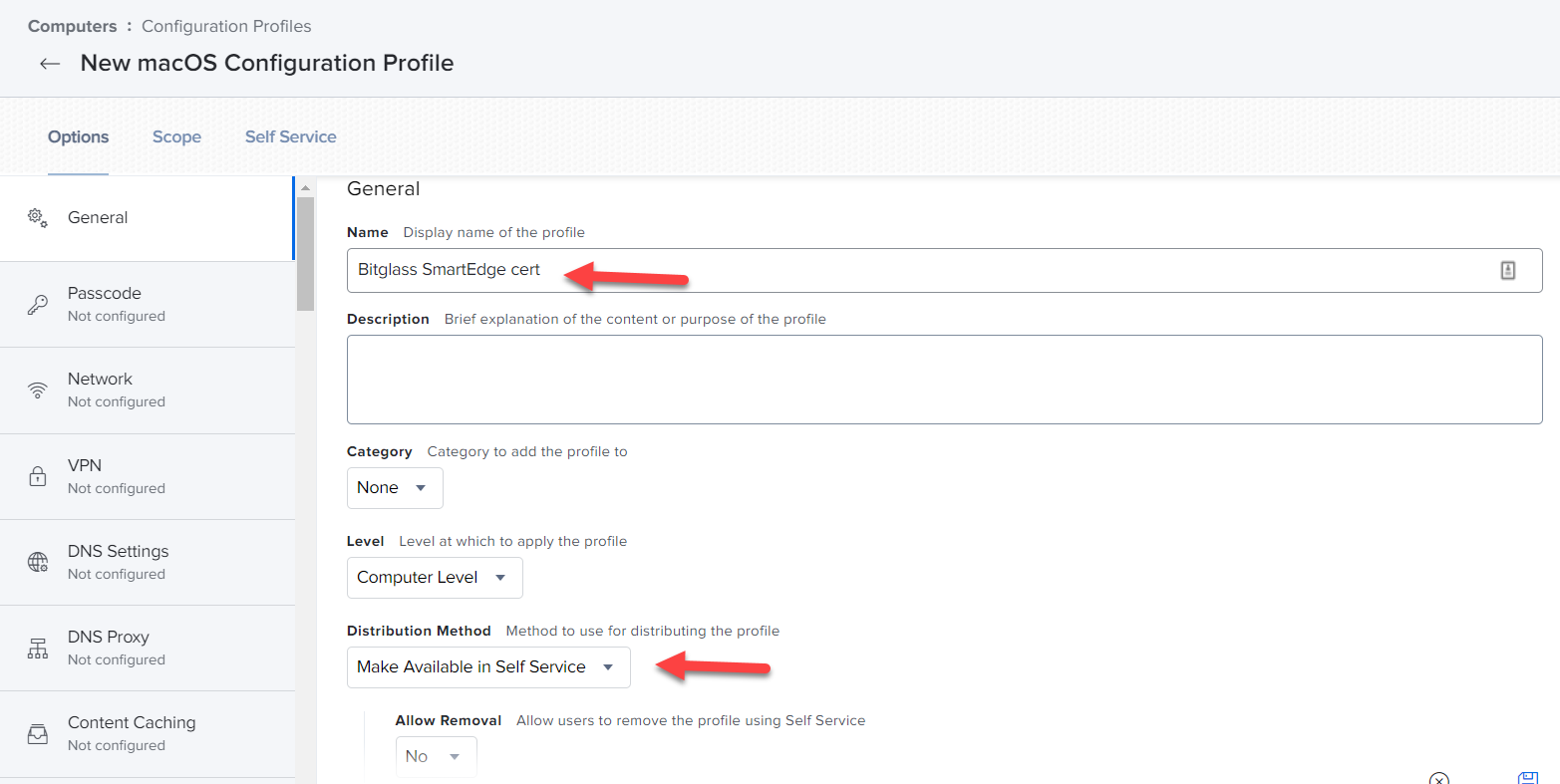
-
On the left column, scroll down and select Certificate and then select Configure in the main screen.
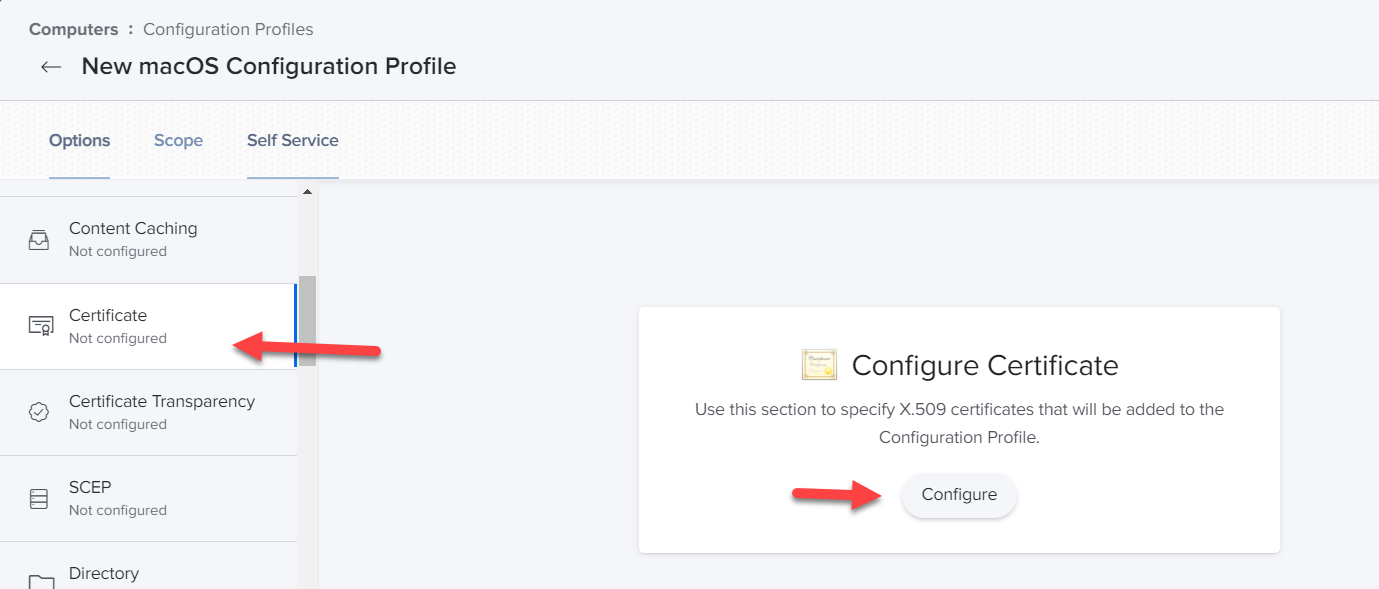
-
In the new window, provide a name for the cert, select upload and then upload the cert you download from Forcepoint Data Security Cloud | SSE. Provide a
password if desired and then make sure to check the box Allow all apps access to ensure the CA has the proper access it needs to generate self
trusted certs.
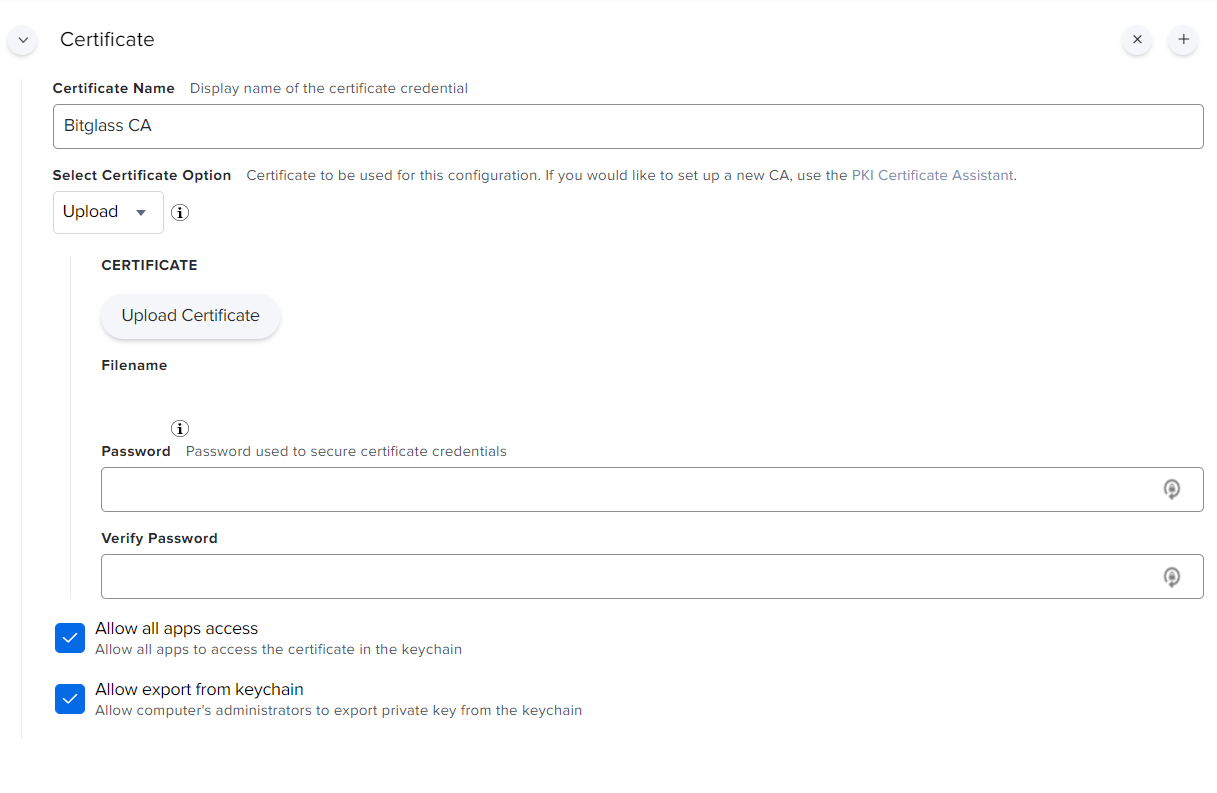
-
Save the certificate profile.
The finished configuration profile should look like the following:
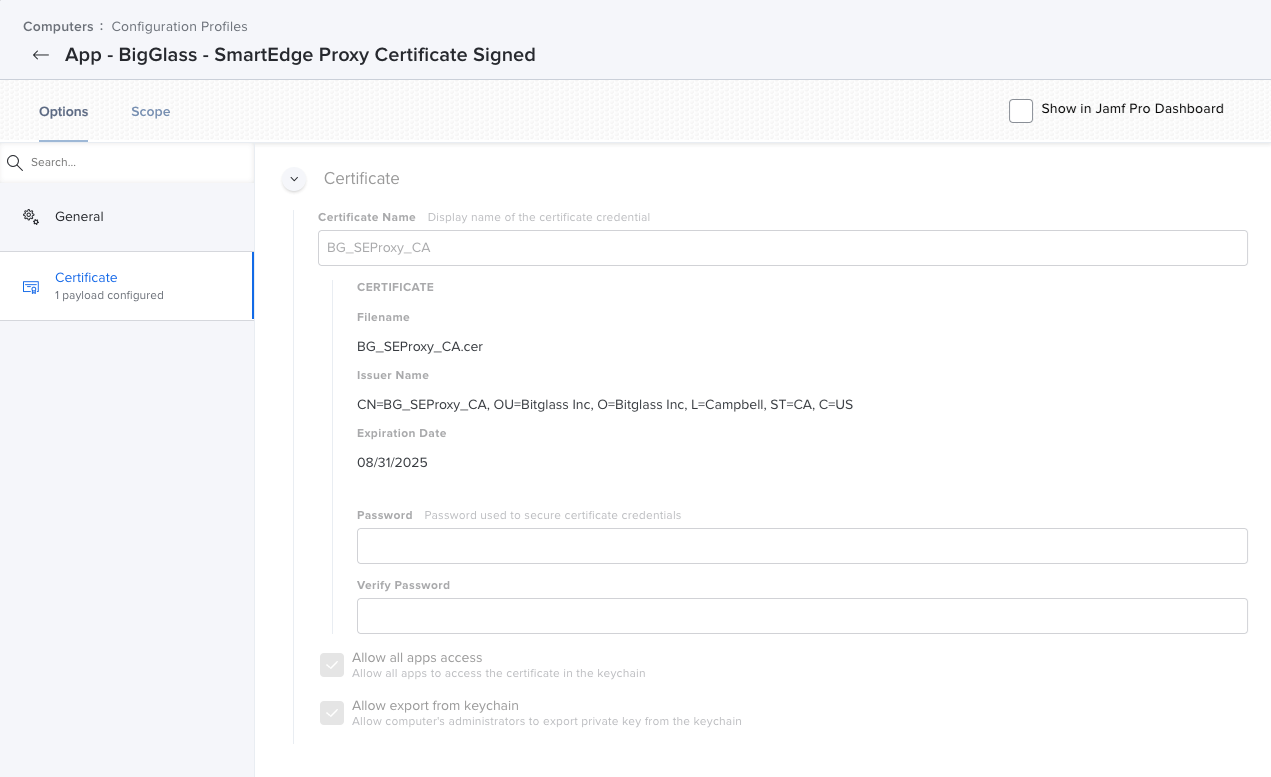
Repeat the same process for your root certificate.
You are ready to push the certificate to your devices. This will now allow the SmartEdge agent on Big Sur or newer version devices to generate dynamic certs.
- Push the certificate to desired devices.
- On the Forcepoint Data Security Cloud | SSE admin portal, navigate to Protect > Forward Proxy > SmartEdge Proxy and download the required Mac agent version.
- Unzip the downloaded package and place the unzipped package folder in /private/var/tmp directory.
-
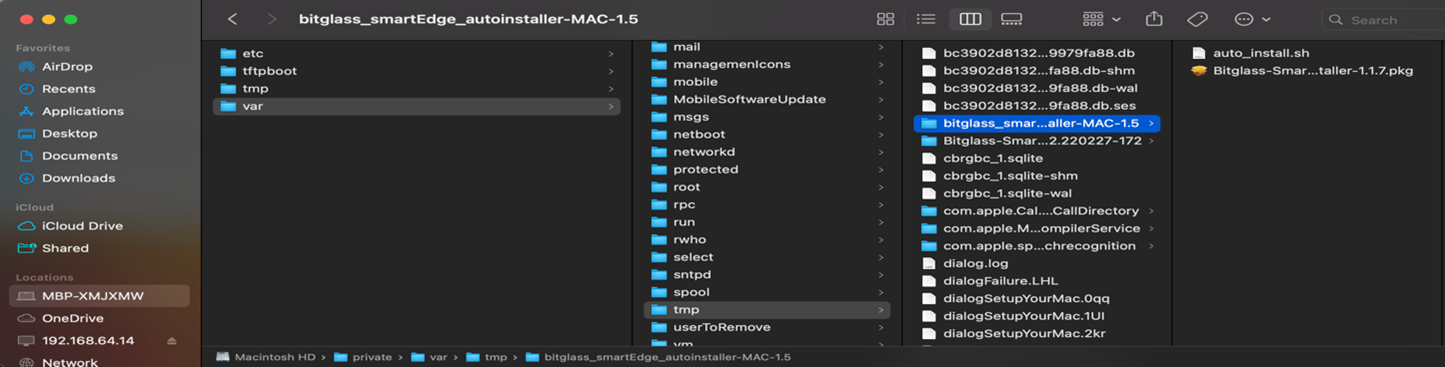
Open the /private/var/tmp location and then locate the folder.
Your folder structure should be similar to the following.
- Download and install the JAMF Composer.
-
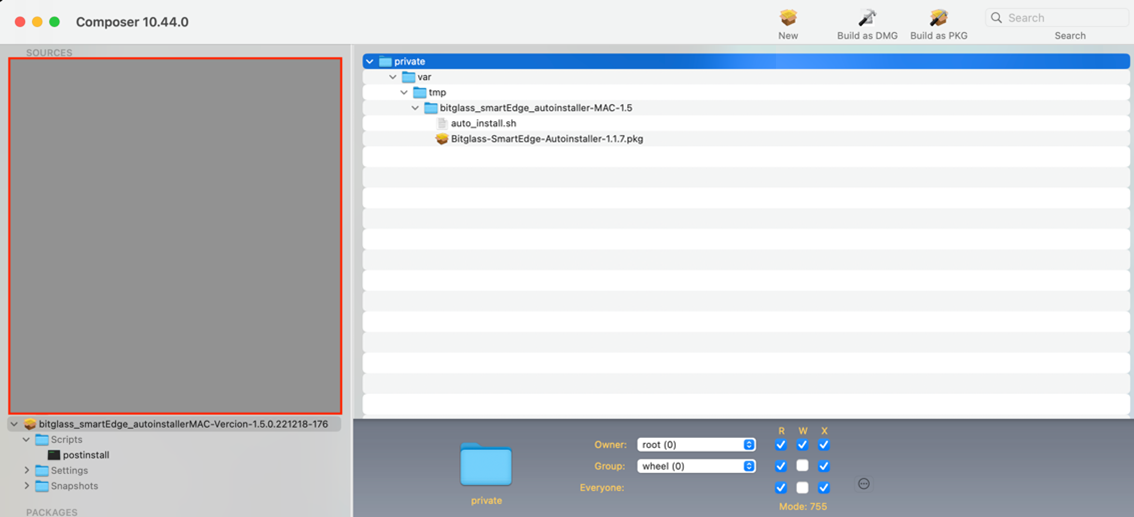
Copy the package and script from the /private/var/tmp location to the source folder in JAMF Composer.
After moving the components, ensure that your package has the correct permissions and matches the appearance shown in the following screenshot.
-
Follow the steps below to create new source package:
- Expand your package payload.
-
Right-click the Script folder, select Add Shell Script and then choose postinstall.
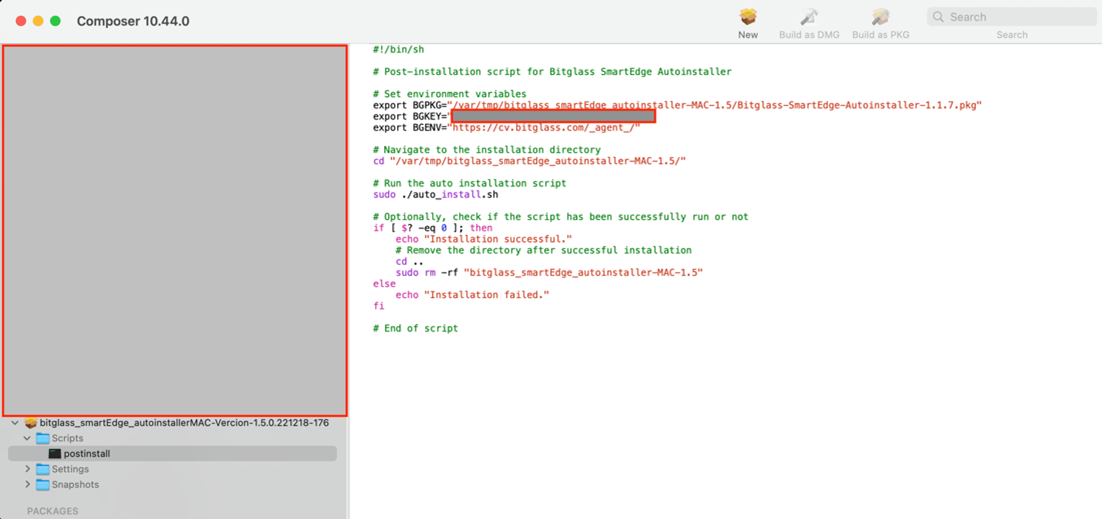
You can refer to the following script as an example of post install script:
#!/bin/sh # Post-installation script for Bitglass SmartEdge Autoinstaller # Set environment variables export BGPKG="/var/tmp/bitglass_smartEdge_autoinstaller-MAC-1.5/Bitglass-SmartEdge-Autoinstaller-1.1.7.pkg" export BGKEY="0_xyzXYZ xyzXYZ xyzXYZ xyzXYZ xyzXYZ xyzXYZ" export BGENV="https://cv.bitglass.com/_agent_/" # Navigate to the installation directory cd "/var/tmp/bitglass_smartEdge_autoinstaller-MAC-1.5/" # Run the auto installation script sudo ./auto_install.sh # Optionally, check if the script has been successfully run or not if [ $? -eq 0 ]; then echo "Installation successful." # Remove the directory after successful installation cd .. sudo rm -rf "bitglass_smartEdge_autoinstaller-MAC-1.5" else echo "Installation failed." fi # End of scriptMake sure to replace the following variables values in the script with your tenant details. You can find these details from auto_install.sh.- BGKEY
- BGENV
- BGPKG
-
Save your changes and click Build as PKG to build the source file.
-
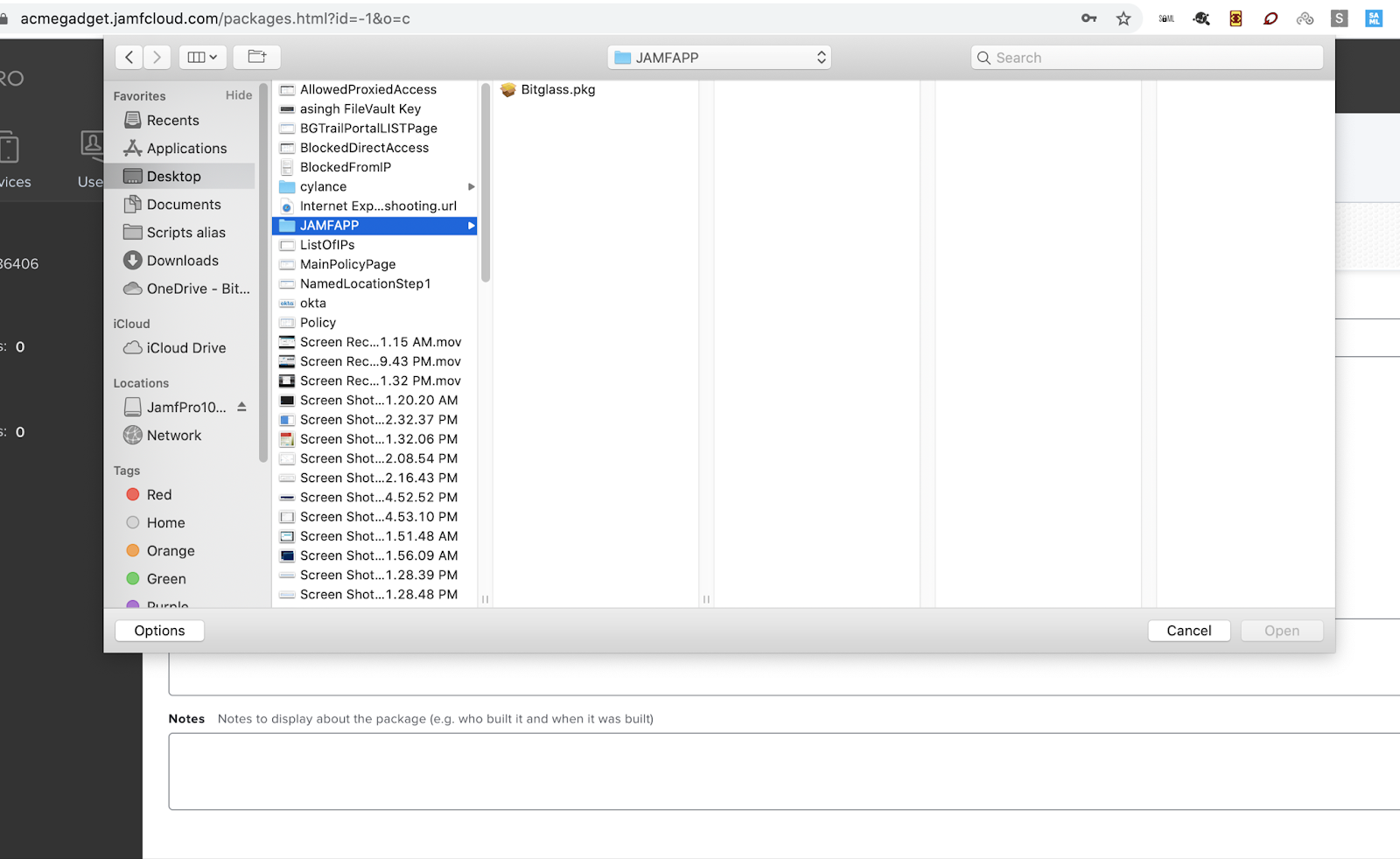
On the JAMF admin portal and upload the new source file into a JAMF policy.
To minimize down time and prevent users running into any connection issues, Forcepoint recommends you to create a smart group with the Criteria set to Profile Identifier, Operator set to is and Value set to your profile identifier. This way the application will install only on the devices that have both configuration profiles installed.
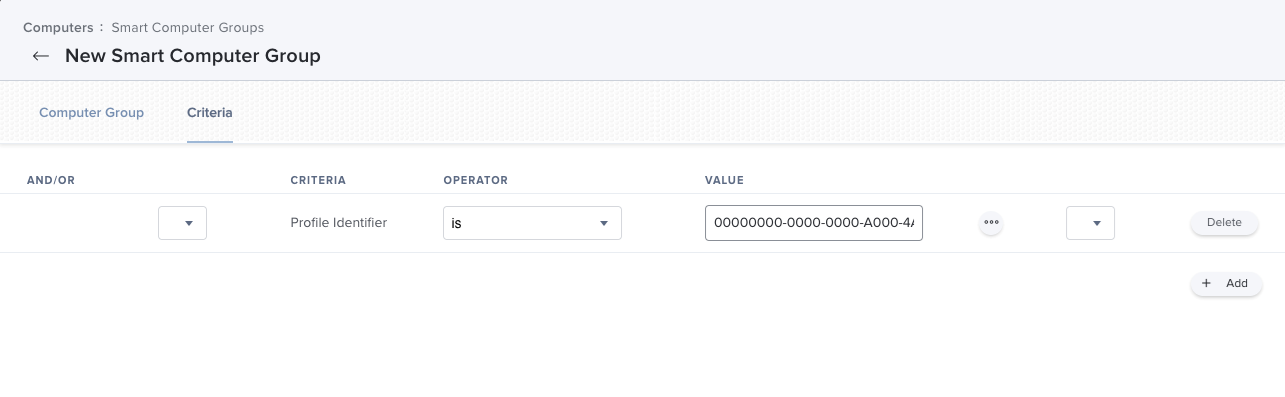
-
Save and apply policy in the JAMF admin portal.
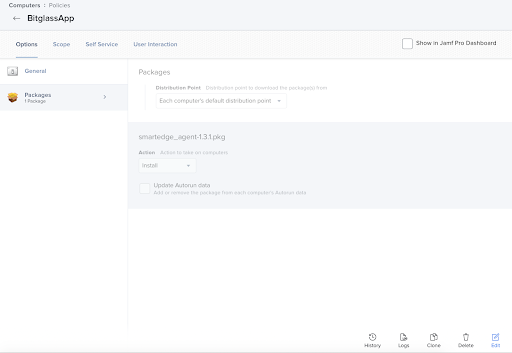
-
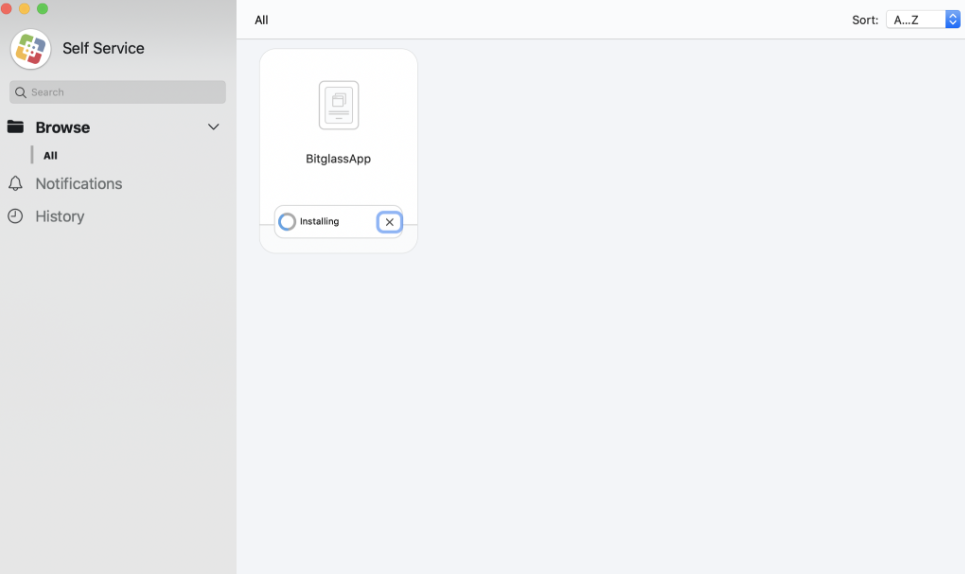
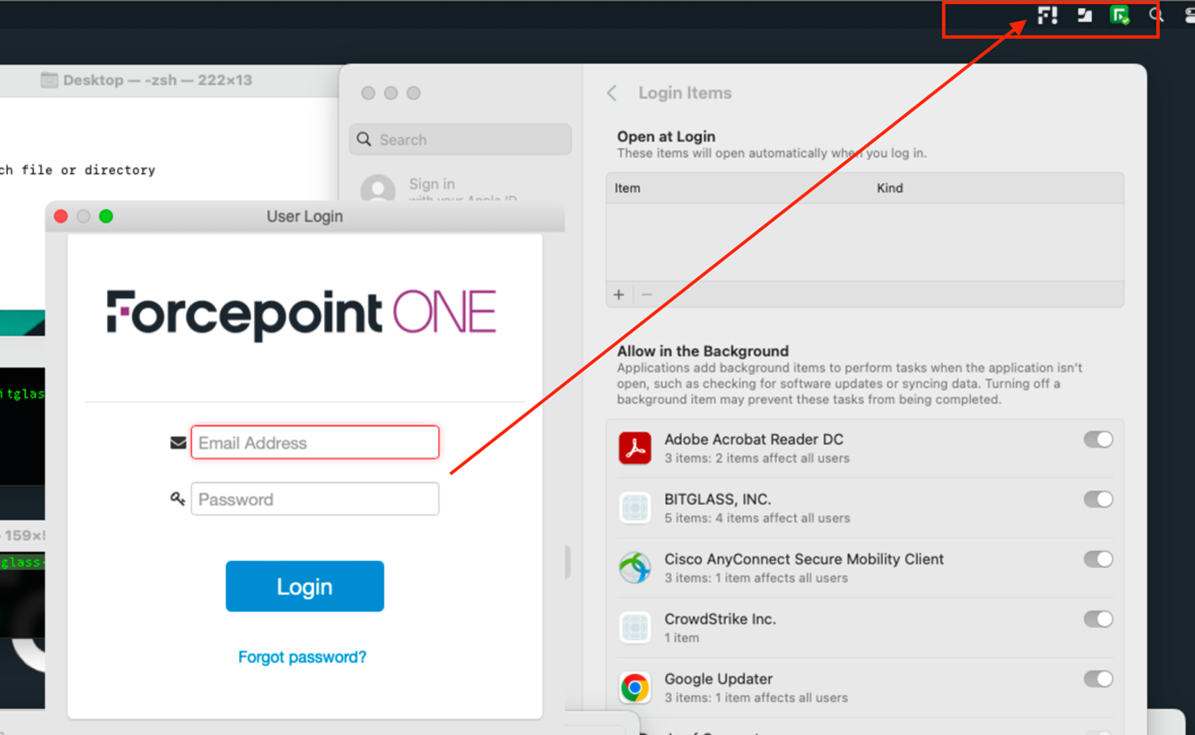
You can verify by looking at an endpoint that is being controlled by your JAMF policy and verify the agent is being installed. Once done, you will see the agent icon in the top
bar.