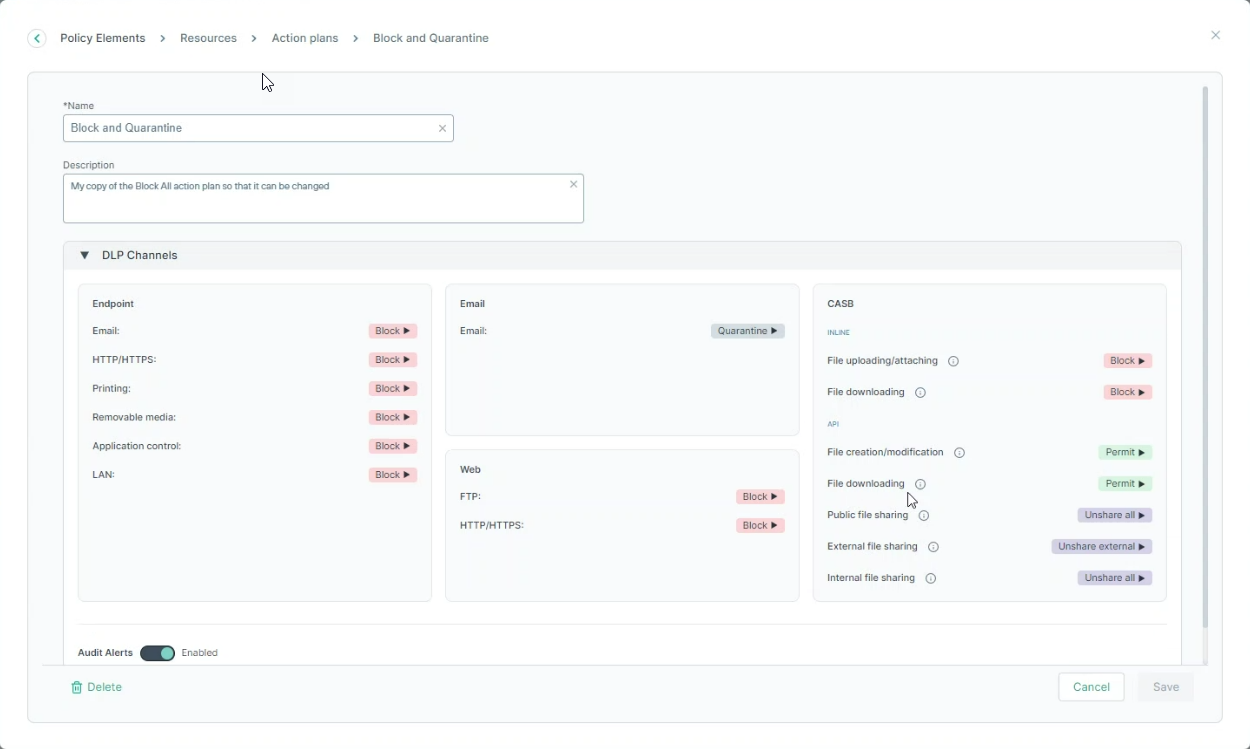
Action plans
Use the Action plans dialog to define how the system responds when various breaches are discovered.
Note: It is possible now to edit predefined Actions plans.
| Name | Description |
|---|---|
| Audit Only |
(Default) Permit all activity on all channels, and log incidents in the audit log. This action plan is designed for mild breaches. |
| Block All |
Block all incidents on all channels, audit them. This action plan is designed for severe breaches. |
Note: It is now possible to Save a predefined resources (i.e. change their configurations) or Save as – i.e. create a new, similar resource.
When Save is selected, the policies that use the predefined resources will be affected, while when Save as is selected, only policies that will use
the new resource will be affected. Also, once a predefined resource is saved, there is an option to Reset it to the original, predefined settings.
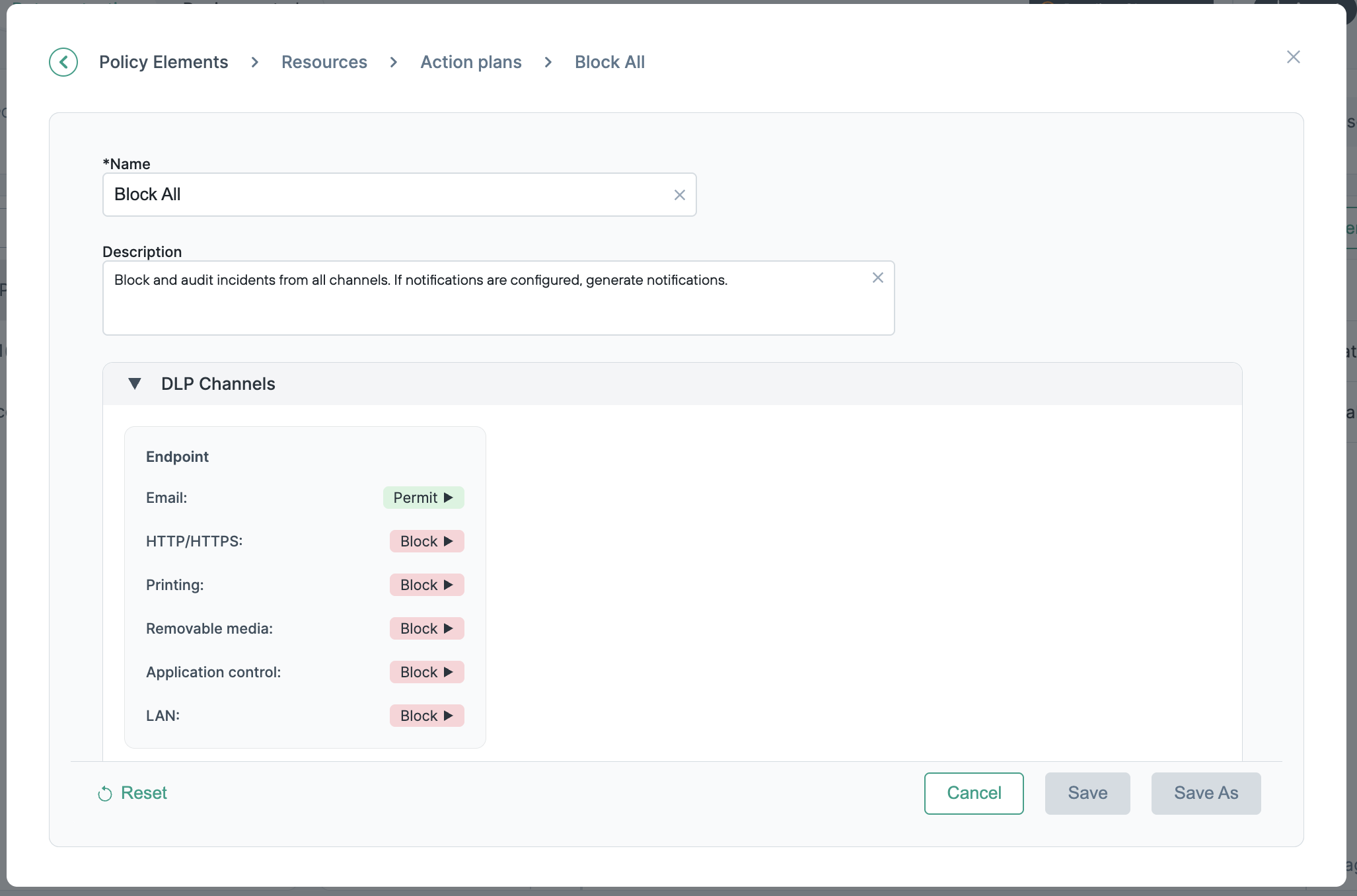
Complete the following steps to add an action plan: