Add new rule to policy
Click the Add new rule button on the policy editor, or right-click a specific policy, from the context menu to select the Add new rule option to open the rule editor.
Once a new policy is saved, the policy editor will automatically display the Create rule editor. The rule status can be set to enable or disable.
A policy rule editor consists of the following parts:
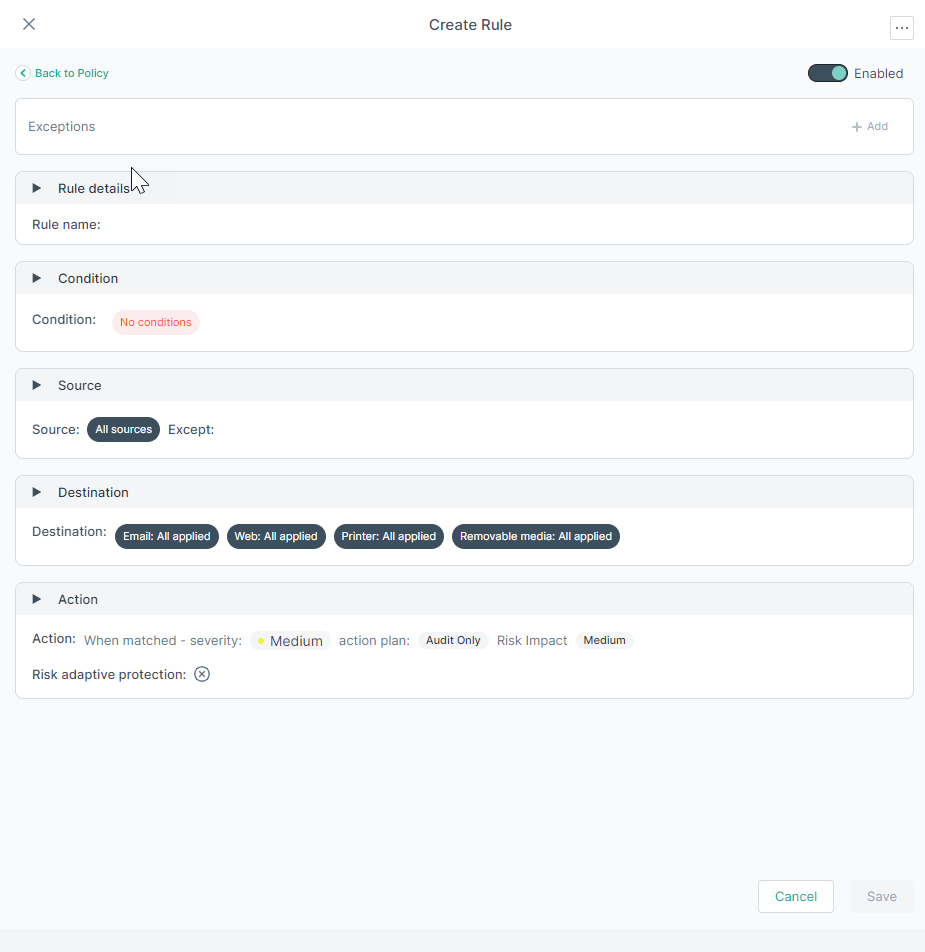
Rule details
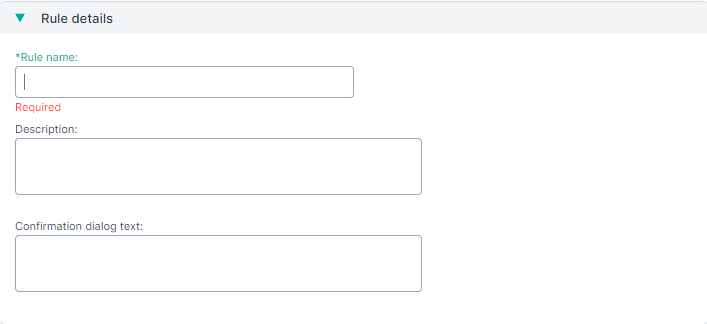
- Rule name (Required): Enter a name that will be used to save the rule.
- Description: Enter a brief description on the purpose of the rule.
- Confirmation dialog text: Enter the text that will be displayed to the user in the pop up displayed when the action plan is Confirm and this action is triggered.
Condition
Defines the type of data that should be matched.
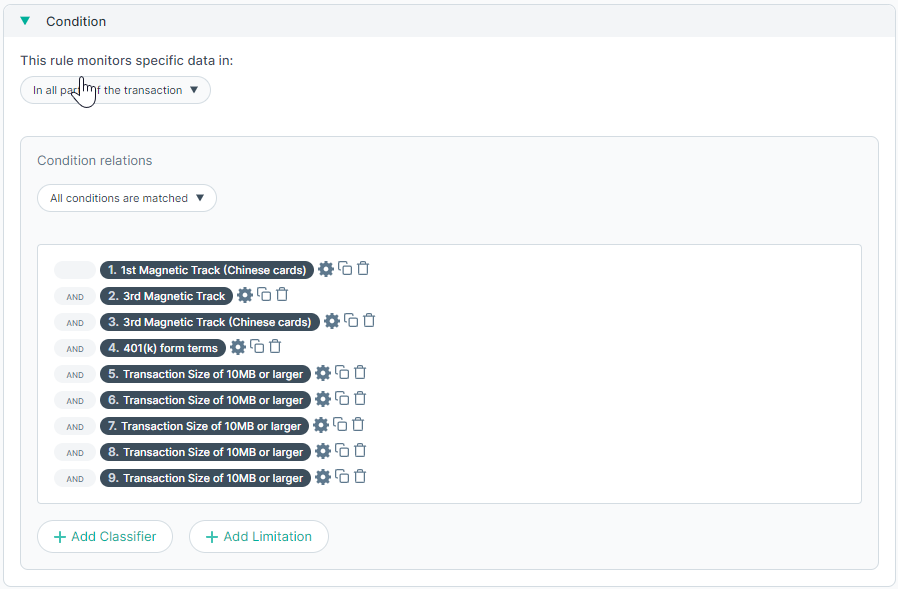
You can also edit the properties of the classifier by just clicking on the classifier in the list:
- 1: Settings - You can edit/modify the properties of the selected classifier.
- 2: Duplicate - You can duplicate the specific classifier.
- 3: Remove - You can delete the specific classifier.
This rule monitors specific data in: This drop-down lists options that indicate when to trigger incidents. Administrators can choose from following options to apply the conditions on:
- In all parts of the transaction: To trigger an incident if the sum of all matches in the transaction exceeds the configured threshold. For example, if the threshold is 3, then a transaction with 2 matches in the message body and one match in the subject line triggers an incident.
- In each part of the transaction separately: To trigger an incident triggered only when the threshold is reached in any one part of the transaction. For example, there would have to be 3 matches in the body text or 3 in the subject line or other message parts for an incident to be triggered.
Condition relations: Indicates when the rule should be triggered if more than one condition is defined.
Administrator can choose to set condition relations to apply conditions from any of the following options:
- All conditions are matched: Trigger the rule if all the selected conditions are matched.
- At least one condition is matched: Trigger the rule if only one of the selected conditions is met.
- User can set custom relation: Using boolean logic define when a rule should be triggered.
You can add classifiers and limitations to the condition relations.
- +Add Classifier: Use this option to add classifiers to the build the condition relations.
- Click +Add Classifier.
- Enable the classifier you want to add from the list. Next, click the + sign to add it to the condition relation.
To view or edit the properties of a classifier, just click the classifier in the list:
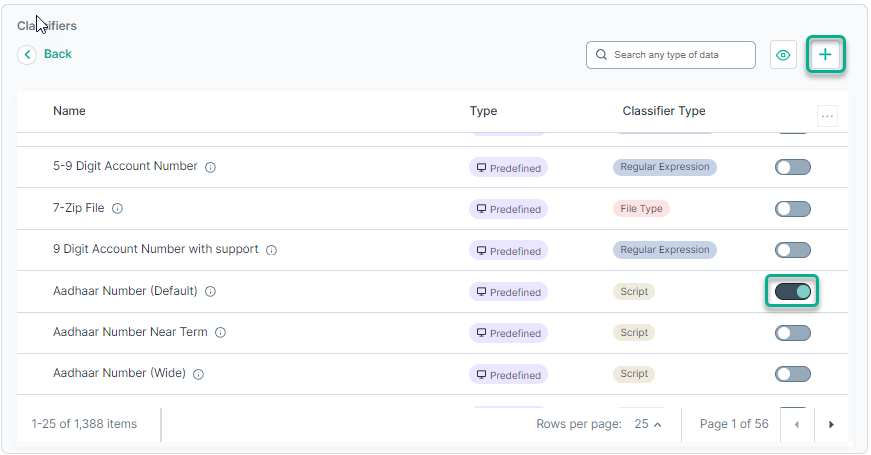
This opens the following dialog, where you can edit the properties of a classifier:
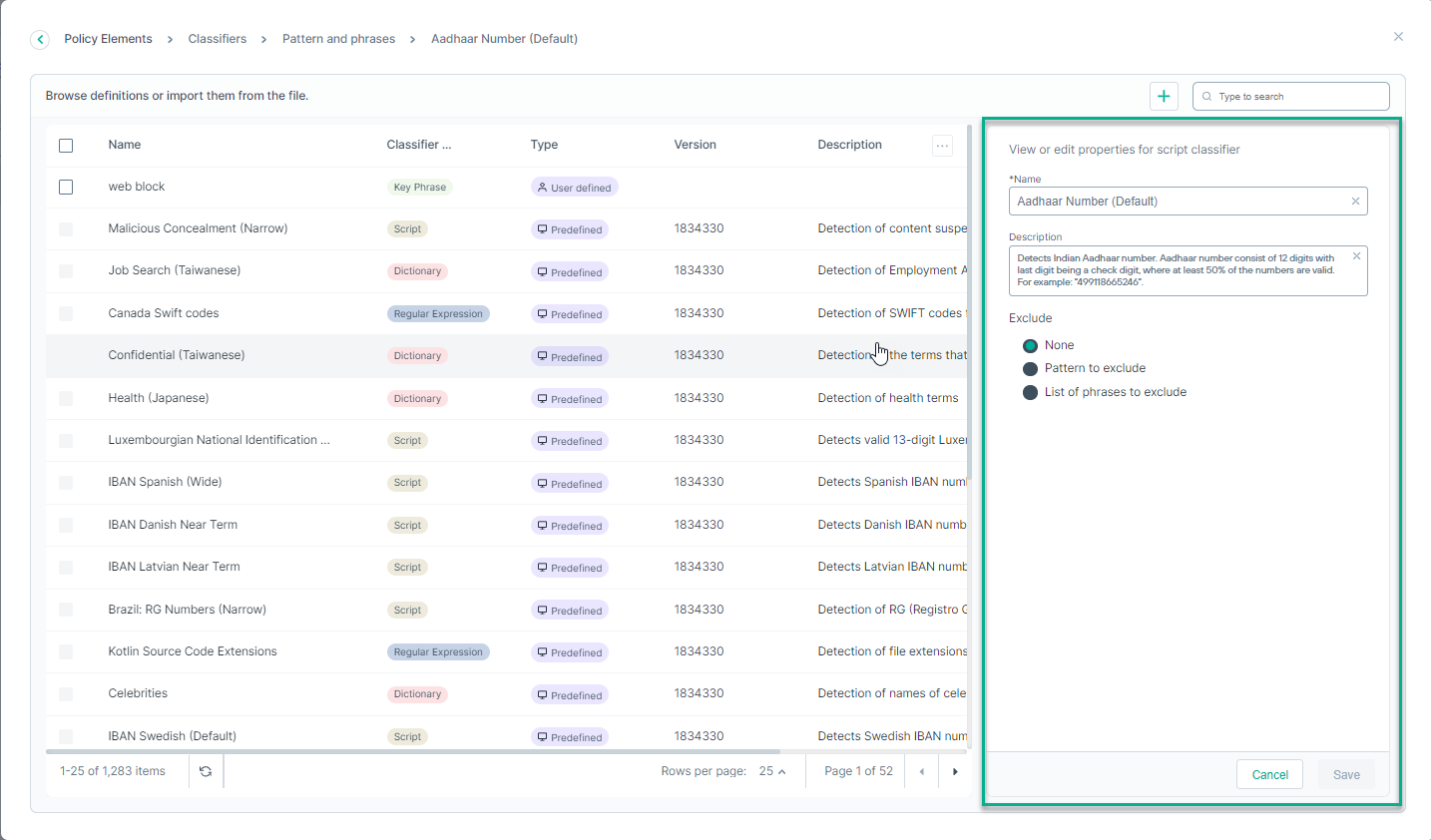
You can enter the pattern or phrases to exclude:
- None
- Pattern to exclude: Enter the pattern to exclude.
- List of phrases to exclude: Include the phrases to exclude. You can include wildcards as well.

- Add Limitation: Use the option to add limitations to the condition. You can define following:
- Transaction Size: Define to detect transactions of the specified size or larger.
- Email Attachments: Define to detect email messages with a certain number of attachments or greater.
- Email Destinations: Define to detect messages sent to a specified number of domains or greater.
Source
Identifies the sources of data, such as endpoints, devices, domains, and networks, that apply to this rule. By default, a rule applies to all sources. A rule can be applied to specific sources (Inclusions), or specific sources can be excluded from the rule (Exclusions). Use the drop-down to select between types of sources, such as Users, Group Directory, Registered endpoints, Custom computers, Domains, Networks, Business units, Organizational units, or Computers. Use the search option to locate one or more elements and then click the + icon to move the selected elements to the Inclusions or Exclusions box as required. You can also choose to add or remove multiple selections using the Add all or Remove all buttons.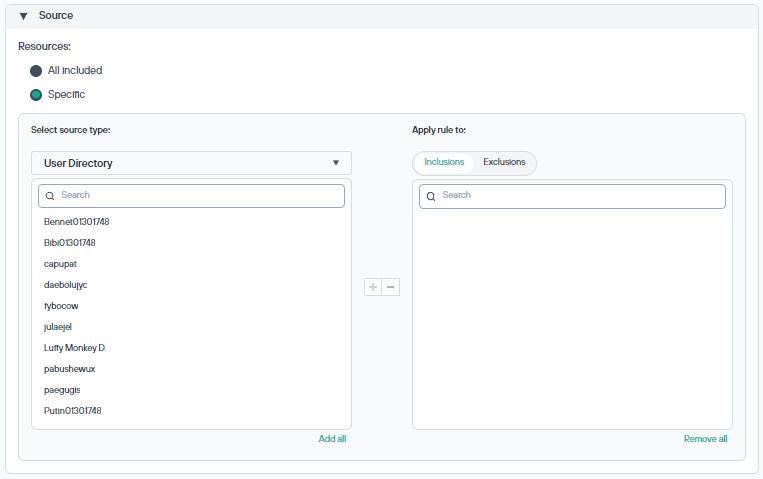
Destination
Define the destinations for data protected by this rule.
From the Select destination field, select the following destinations:
- For the endpoint destination you can select any of the following channel types:
- Email: Select the Email destination to monitor email on endpoint machines. By default, email is analyzed on all endpoint destinations.
You can either select Endpoint or Cloud as channel.
Note: Cloud Email requires a separate license and is displayed only if this license is in place.- Set the email destination toggle button to Enabled.
- If you selected Endpoint Email, specify whether the rule should be applied to All included or Specific
destinations. If selected Specific, use the search option to locate one or more elements and click the + icon to move the selected
elements to the Inclusions or Exclusions box as required.
To add, edit, or delete domains, see the Domains section.
Directions: You can select from either Outbound or Internal.
- Web Select Web destination to prevent or monitor users posting sensitive data to networks, domains, business units, custom computer,
Organizational units, computers, countries or URL categories via any of the following web channels:
- Endpoint HTTP- websites, blogs, and forums accessed by endpoint machines over HTTP
- Endpoint HTTPS- websites, blogs, and forums accessed by endpoint machines over HTTPS
- HTTP
- HTTPS
- FTP
Note: HTTP, HTTPS and FTP destinations require a separate license and are displayed only if this license is in place.Set the Web destination toggle button to Enabled.
Note: Several SaaS domains are excluded from analysis by default. Optionally, exclude more domains or remove domains from the exclusion list. You can also customize the list of resources that are excluded from web policies by default. For more information, see Business Units section.Use Channels field to select or deselect individual Web channels.
To add, edit, or delete networks, domains, business units, and custom computers, see the Resources section.
- Printing: Select Printing destination to analyze files that endpoint users send to printers.
- Set the printing destination toggle button to Enabled.
- Specify whether the rule should be applied to All included or Specific destinations. If selected specific use, the search option to locate one or more elements and the + icon to move the selected elements to the Inclusions or Exclusions as box required.
- Removable media: Select Removable media channel to analyze media such as thumb drives, external hard drives, and other USB devices on the
endpoint machines. By default, all removable media is included.
- Set the removable media destination toggle button to Enabled.
- Specify whether the rule should be applied to All included or Specific destinations. If selected Specific, use the search option to locate one or more elements and the + icon to move the selected elements to the Inclusions or Exclusions box as required.
- Applications: Select Applications destination to analyze content that is being cut, copied, pasted, or otherwise handled by users on
endpoint applications. (Windows endpoints only).
- Set the applications destination toggle button to Enabled.
- You can select from:
- Online application groups: SaaS and other online applications.
- Application groups: Installed applications.
Use the search option to locate one or more elements and the + icon to move the selected elements to the Inclusions or Exclusions box as required. You can also choose to add or remove multiple selections using the Add all or Remove all buttons.
- LAN: Destination to analyze endpoint file copy over LANs. By default, outbound traffic for all networks is covered, that is, traffic going from the endpoint to all LANs.
Endpoint LAN control is applicable to Windows endpoints using Windows file sharing only.
- Set the network share destination toggle button to Enabled.
- Specify whether the rule should be applied to All included or Specific destinations.
You can select from following elements:
- Networks
- Custom computers
- Business Units
If selected Specific, use the search option to locate one or more elements and the + icon to move the selected elements to the Inclusions or Exclusions as required.
- Email: Select the Email destination to monitor email on endpoint machines. By default, email is analyzed on all endpoint destinations.
- CASB
Select CASB to analyze files sent to supported cloud applications, such as Office365 or Box.
You can either select API or Inline.
If you selected API, you next need to specify whether the rule should be applied to All included or Specific cloud applications.
If you selected Specific you next need to select the Cloud Applications from the list. You can use the + or - buttons to add them to the Inclusions or Exclusions list.
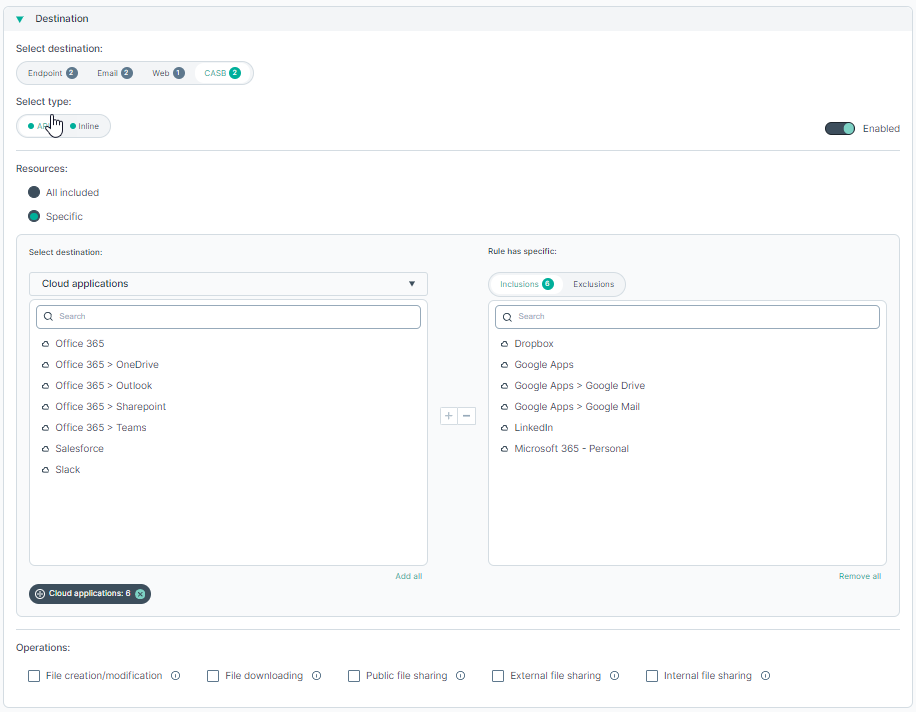 You must select at least one operation from following available options:
You must select at least one operation from following available options:- File creation/modification
- File downloading
- Public file sharing
- External file sharing
- Internal file sharing
Purpose of each operation is explained in the table at the end of this section.
If you selected Inline, you next need to specify whether the rule should be applied to All included or Specific cloud applications.
If you selected Specific you next need to select the Cloud Applications from the list. You can use the + or - buttons to add them to the Inclusions or Exclusions list.
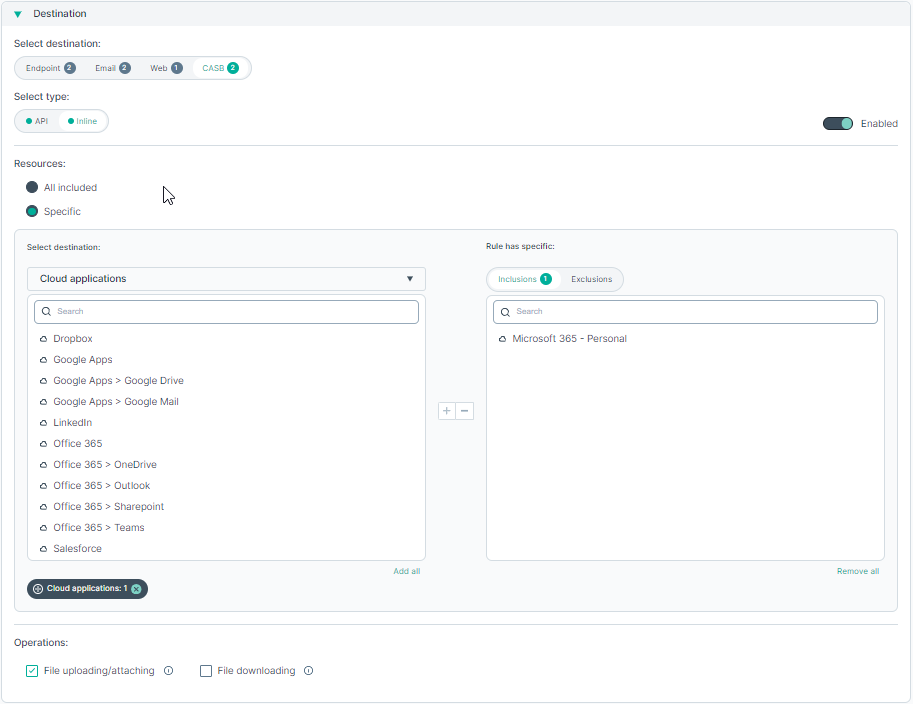 You must select at least one operation from following available options:
You must select at least one operation from following available options:- File uploading/attaching
- File downloading
Purpose of each operation is explained in the table at the end of this section.
Action
Defines the severity and action to apply based on the matched conditions. Also allows for selection of notification templates to notify when certain actions are taken. For details, see Notification Templates.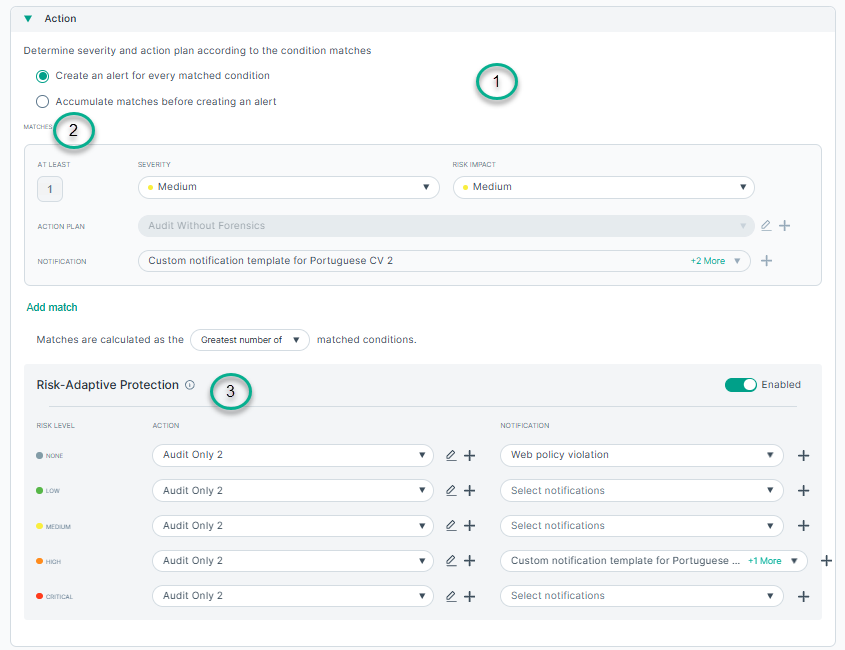
- 1
- Determine severity and action plan according to the condition matches: Choose any of the following options to trigger an incident:
- 1a
- Create an incident for every matched condition: To trigger an incident every time a condition in the rule is matched. (For example, if a user sends an email message containing sensitive content, then prints the message, 2 incidents are generated.)
- 1b
- Accumulate matches before creating an incident: To have the system collect matches for a particular source over time and create incidents when a threshold is
met (drip DLP). The system remembers user activity and generates incidents for matches that occur within a defined period.
Use the drop-down to set the Count for matches:
- transactions: Count incident transactions as they accumulate for a given source, even though each incident can have multiple triggers.
- unique matches: Count unique matches to count violation triggers that accumulate for a source, but only triggers that are unique.If, for example, there is a rule that does not permit 10 different credit card numbers to be sent within 1 hour:
- If a user sends 1 message with 20 credit card numbers, 1 violation trigger is counted.
- If the user sends 20 email messages with the same credit card number, no triggers are counted, because the numbers were not unique.
Note that case differences are counted separately in word-related classifiers. For example, word, Word, and WORD.
- all matches: Count all matches (default) that accumulate for a source, even duplicates. In the example above, even if the user sent 20 messages with the same credit card number, 20 triggers are counted.
Matches and transactions are counted individually for each source, such as user name or IP address, and they are counted only on the policy engine that detects them. Incidents are generated only when the threshold is met on a single policy engine.
Select a time period for accumulating matches. The time period is a sliding window. It resets every time a match is detected.
Use The rate of matches should decline... field to specify how long the system should continue counting matches once the rate begins to decline.
If the system continues to detect the configured number of matches over the configured period, it continues to accumulate the matches in the same incident.
- 2
- Matches: Use the Add Match button to add new matches.
Use the AT LEAST field to define the threshold for triggering an incident. For example, trigger an incident when there are at least 3 matches (3 or more). If the threshold is not met, the match count is 0.
Specify the incident SEVERITY for the match from the drop-down:- Low: Incidents that match this rule are of low importance. The policy breach is minor.
- Medium: Incidents that match this rule are of medium importance. The policy breach is moderate.
- High: Incidents that match this rule are very important and warrant immediate attention. The policy breach is severe.
If Risk adaptive protection is enabled, then the RISK IMPACT can be set using the drop-down. The value selected will impact the risk score calculation for the affected user.
Select an existing ACTION PLAN using the drop-down. If you want to add new action plan, click the + icon, and for editing click the pencil icon.
For more details, see the Action plans section.
Using the Matches are calculated... field, you can set how matches should be calculated:- Select Greater number of matched conditions to have the number of matches compared, and only the greatest number reported. For example, if there are 5 matches for the classifier “Confidential Pattern”, 3 for “SSN Pattern”, and 10 for “My Key Phrases”, the number of matches would be defined as 10.
- Select Sum of all matched conditions to have the number of matches added together and the total reported. Given the same example as above, the number of matches would be defined as 18.
- 3
- Risk adaptive protection: If enabled, different actions can be selected according to the source user’s risk level. An action can be set for the following risk levels:
- Level 1- None: The user does not have a risk score currently.
- Level 2- Low: The user’s risk score is between 1 and 39.
- Level 3- Medium: The user’s risk score is between 40 and 69.
- Level 4- High: The user’s risk score is between 70 and 89.
- Level 5- Critical: The user’s risk score is between 90 and 100.