Reviewing the CASB Inline score calculation
CASB Inline score evaluates the implementation of the best practices for the four pillars of CASB.
- Visibility
- Identity and Access Management
- Data Protection
- Threat Protection
CASB Inline score contributes 20% of the overall Index if all components are enabled. Each CASB Inline component contributes 25% to the overall CASB Inline.
Application specific score components are evaluated for up to three inline applications configured with the respective policy. Inline applications are given points for policy only if SSO is configured for the application.
If you are not using the Inline CASB capabilities or only using these capabilities partially, then consider each of the following recommendations based on their applicability to your deployment.
Visibility Score
- ShadowIT Discovery (25%) – At least one Firewall or Proxy log Uploaded for ShadowIT scanning. To upload logs manually for Shadow IT discovery, refer to Uploading logs manually for Shadow IT Discovery.
- ShadowIT Discovery (25%) – Log streaming setup for continuous Shadow IT scanning. To setup automatic log collection for Shadow IT reporting, refer to Set up automatic log collection for Shadow IT reporting.
- SIEM Integration (50%) – Automated log export setup for continuous ingestion of logs to SIEM/SOAR or external storage. To export logs, refer to Exporting logs using API.
Identity and Access Management Score
Identity and Access Management Score has five components weighted as below. To create login policies, refer to Configuring login policies.
- MFA (20%) - Measures if Multi-Factor-Authentication (MFA) has been enabled for Admin login to the SSE portal and for end user logins.
- Admin MFA (10%) – Measures if MFA has been enabled for Admin login to the SSE portal. The screen shot below shows one such example:
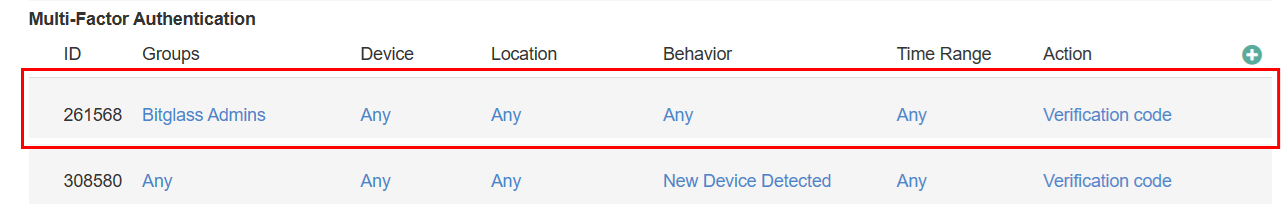
- User MFA (10%) – Measures if MFA has been enabled for end user logins. The screen shot below shows one MFA policy for all users logging in on a new device.
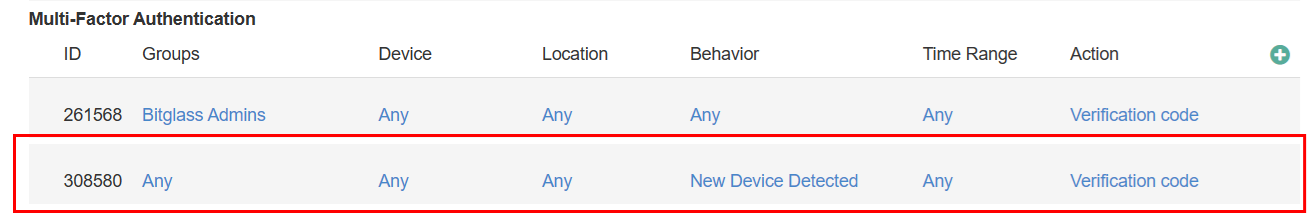
- Admin MFA (10%) – Measures if MFA has been enabled for Admin login to the SSE portal. The screen shot below shows one such example:
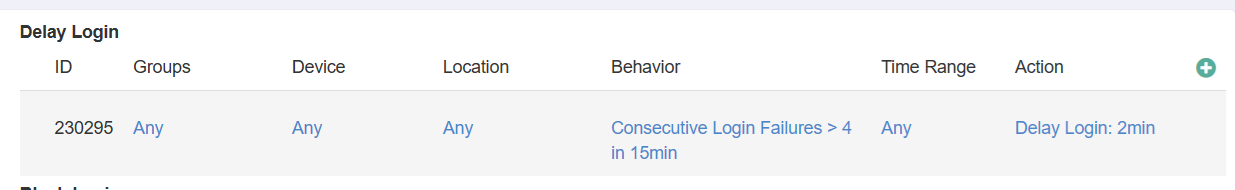
- Delay Login (20%) – Measures if a policy has been configured to protect against brute force login attempts. The screen shot below shows a policy that will require the
user to wait for 2 minutes before attempting to login after more than 4 failures in a 15 minute period.
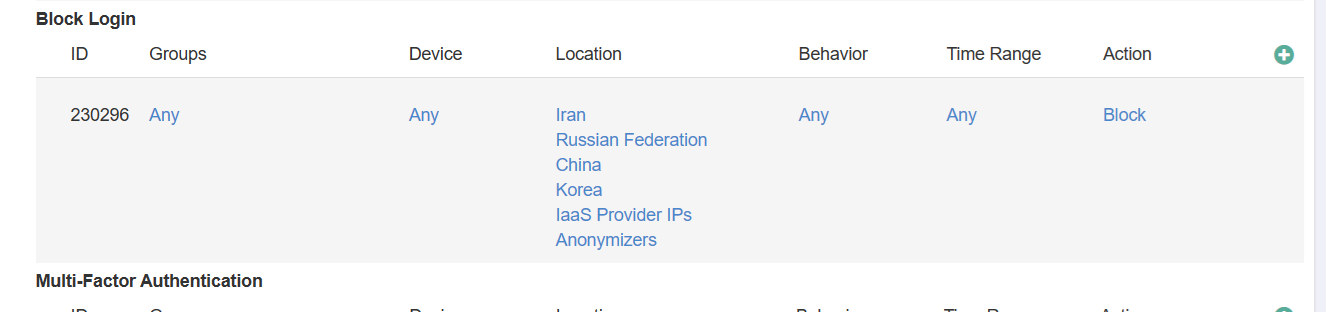
- Block Login (20%) – Measures if a policy has been configured to prevent logins from unwanted locations. The screen shot below shows a policy that blocks logins from the
configured locations.
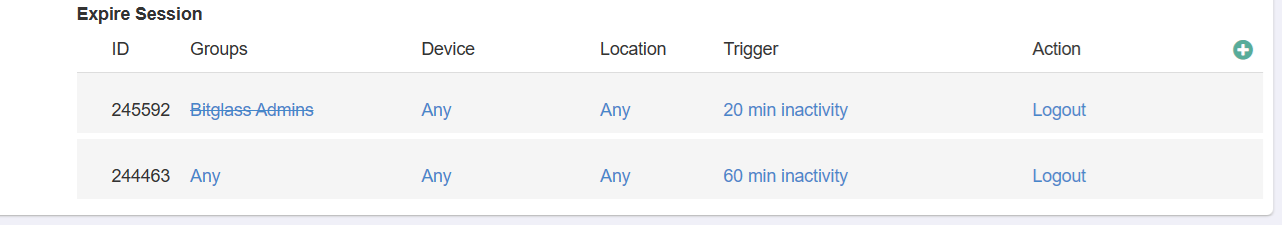
- Expire Session (20%) – Measures if a policy has been configured to automatically timeout unmanaged devices after a configured period of inactivity. The screen shot below
shows a policy that will automatically timeout non admins after 20 minutes of inactivity.
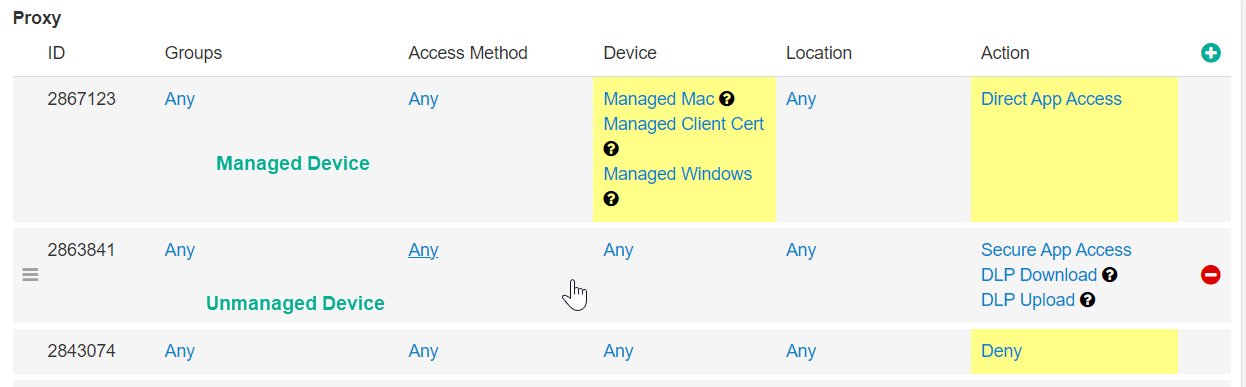
- Managed vs Unmanaged Device Segmentation (20%) – Measures if differentiated policies have been configured and applied based on device type. Refer to Configuring managed device identification for more
details. The below screen shot shows a managed app inline policy with different actions for different device types.
Data Protection Score
- Custom Data Pattern (33.33%) – Measures if Custom Data Pattern(s) to identify proprietary sensitive information has been configured.
- Exact Data Match and File Fingerprinting (33.33%) – Measures if an Exact Data Match and/or File Fingerprinting Data pattern has been configured.
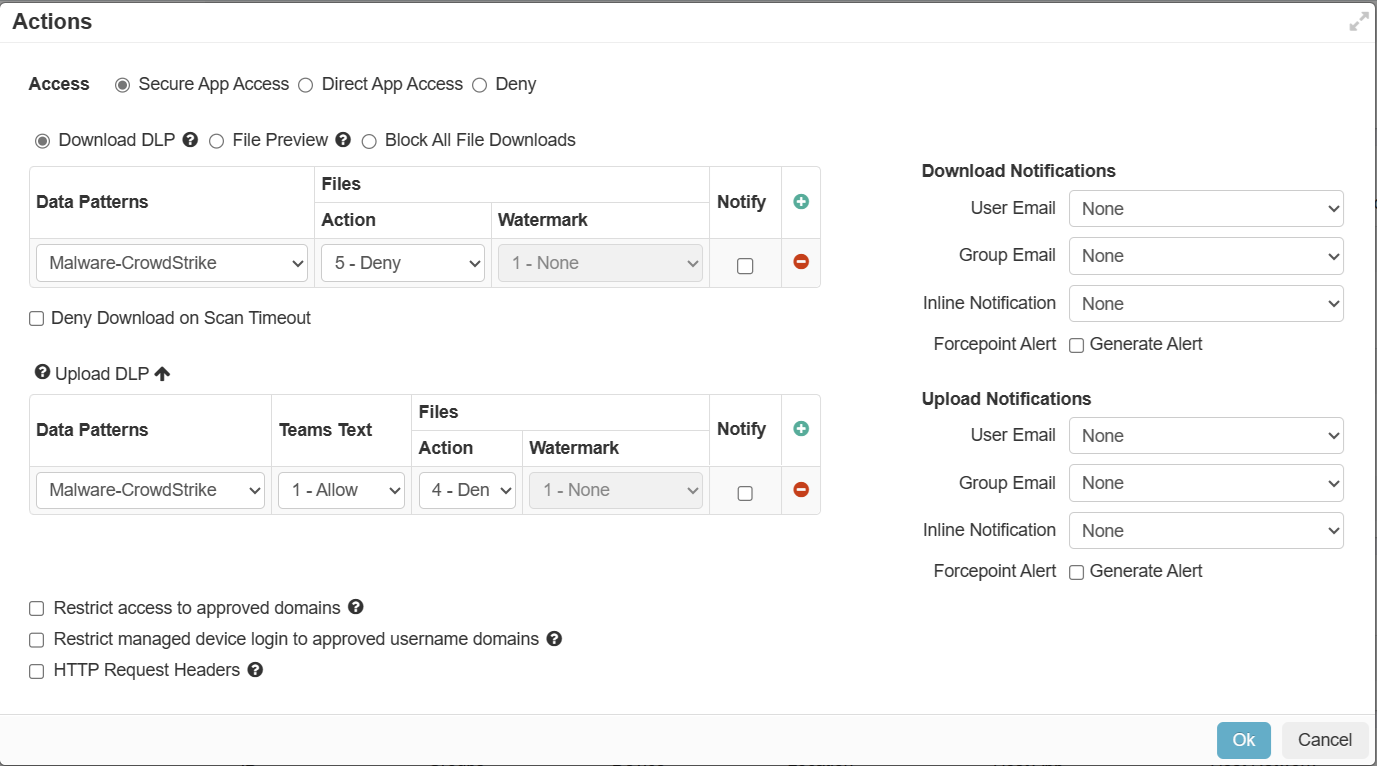
- Inline DLP Configuration (33.33%) – Measures the ratio of inline applications with DLP policy enabled over the total number of configured inline applications (up to three applications).
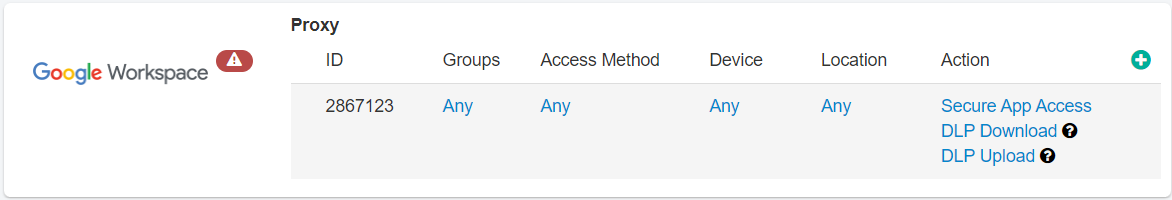
Following is an example of inline policy with secure app access and custom data pattern for sensitive data:
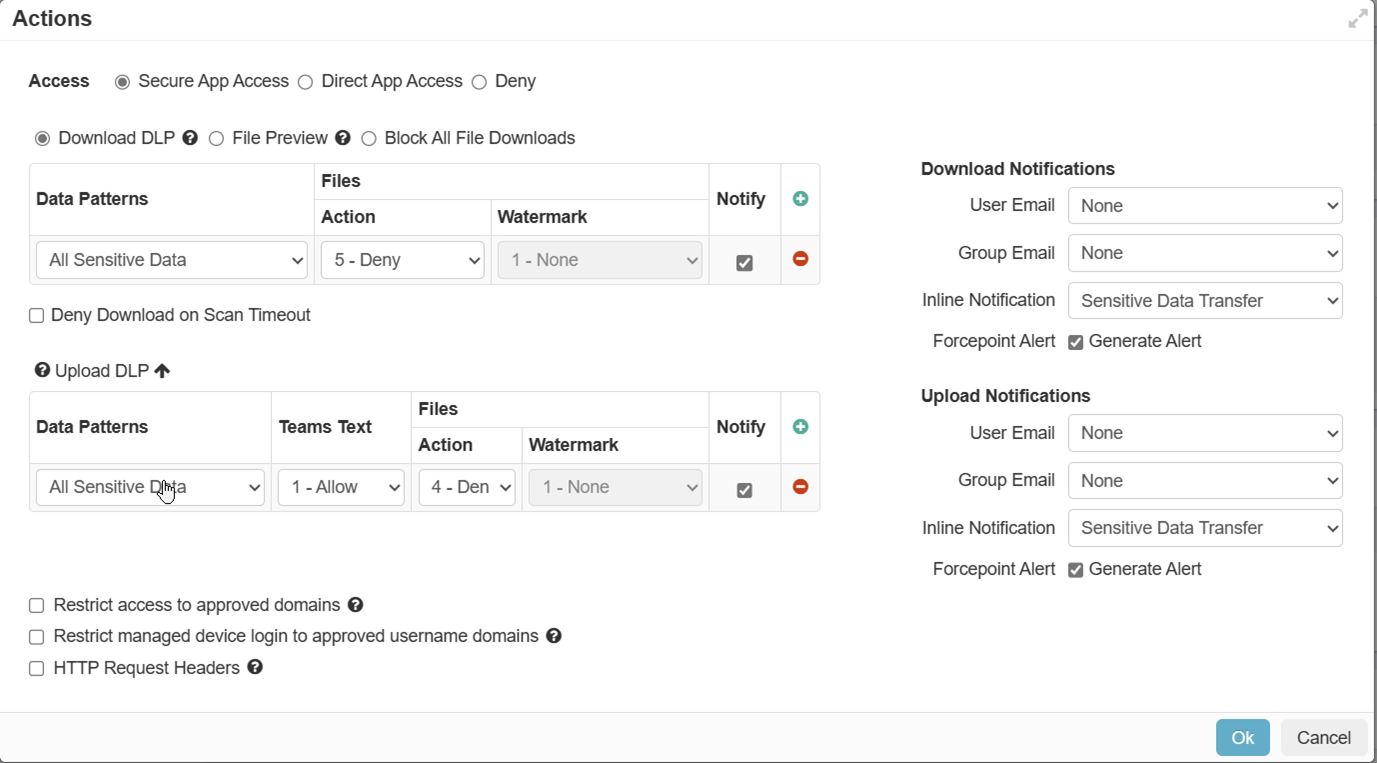
To configure custom data patterns and to configure inline policies for secure app access, refer to Configure DLP and Configuring proxy policy actions respectively.
Threat Protection Score
Threat Protection score measures the ratio of inline applications with Secure App Access policy blocking download of malware over the total number of configured inline applications (up to three applications).
To configure inline policies for secure app access, refer to Configuring proxy policy actions.
Following is an example of inline policy with secure app access for the Google Workspace application: